Understanding IoT Security Challenges
IoT or Internet of Things defines the interconnection of a large number of devices present globally connected to the Internet and are collecting & exchanging their data. IoT Cloud solutions allow different objects to connect and integrate sensors to these objects to deliver digital intelligence over a Cloud platform. Digital intelligence enables these objects to carry out interactions between them without human involvement. The Internet of Things is crucial in making the modern world smarter by amalgamating digital and physical ecosystems.
Why is IoT Getting Important?
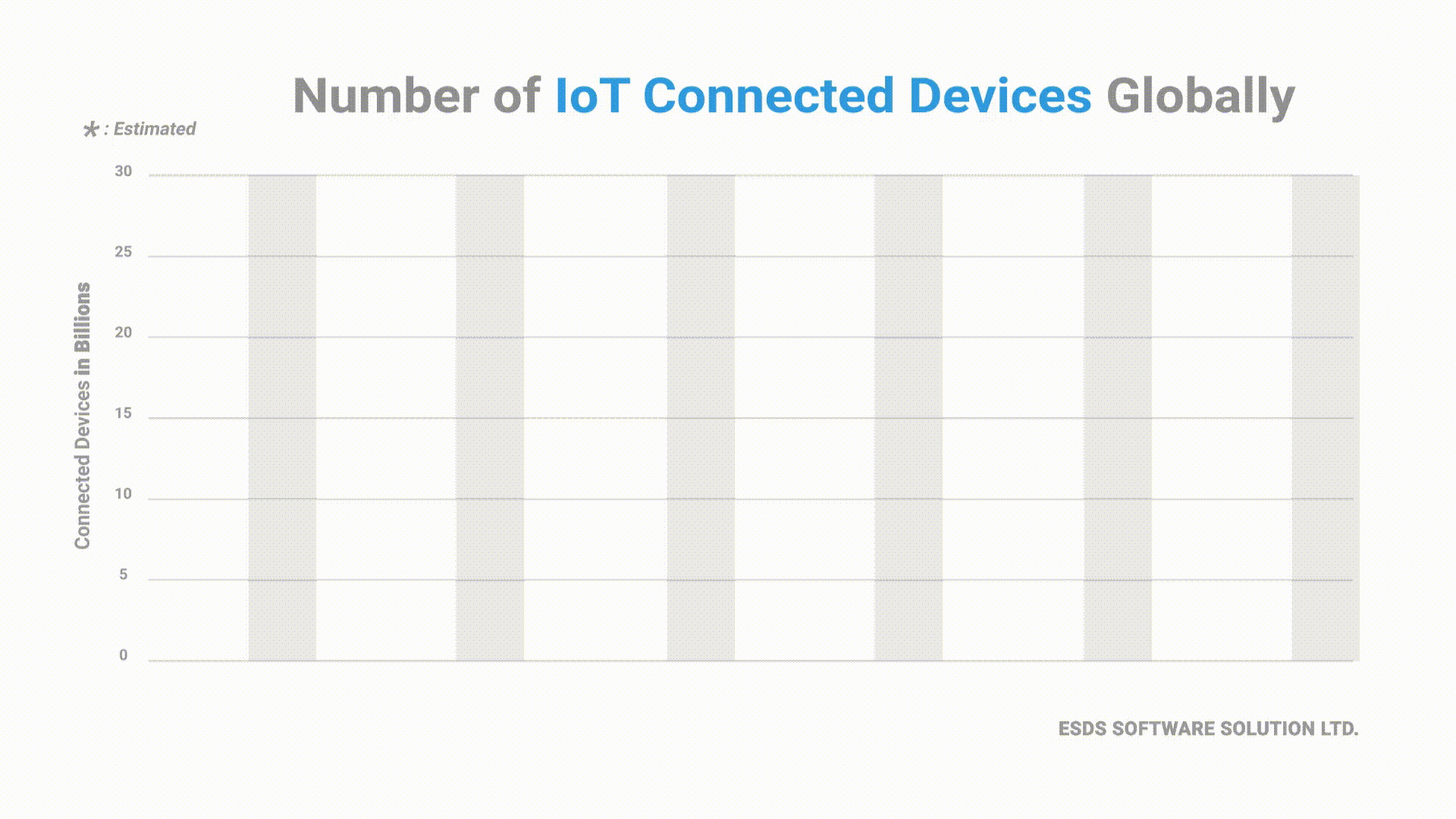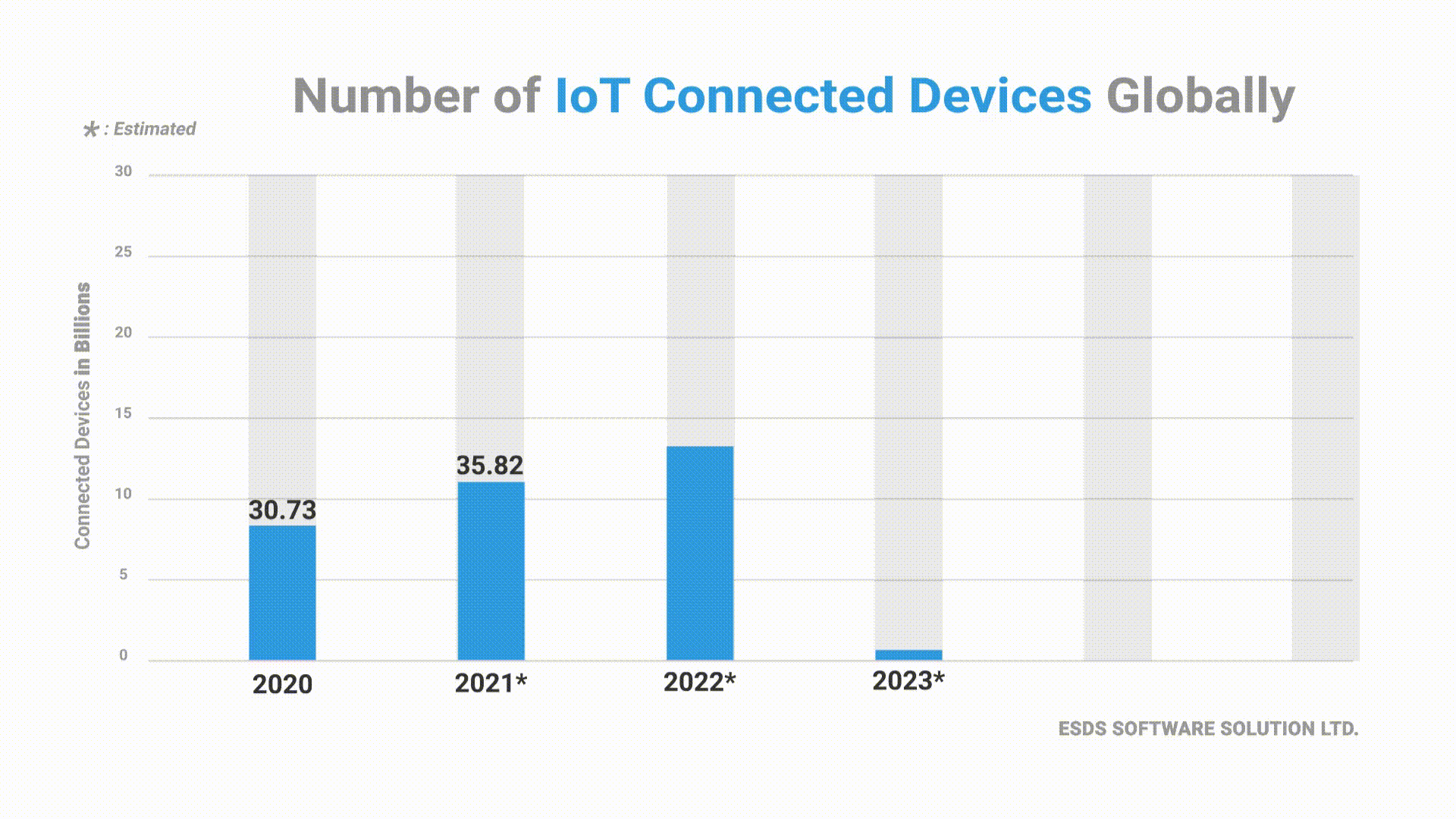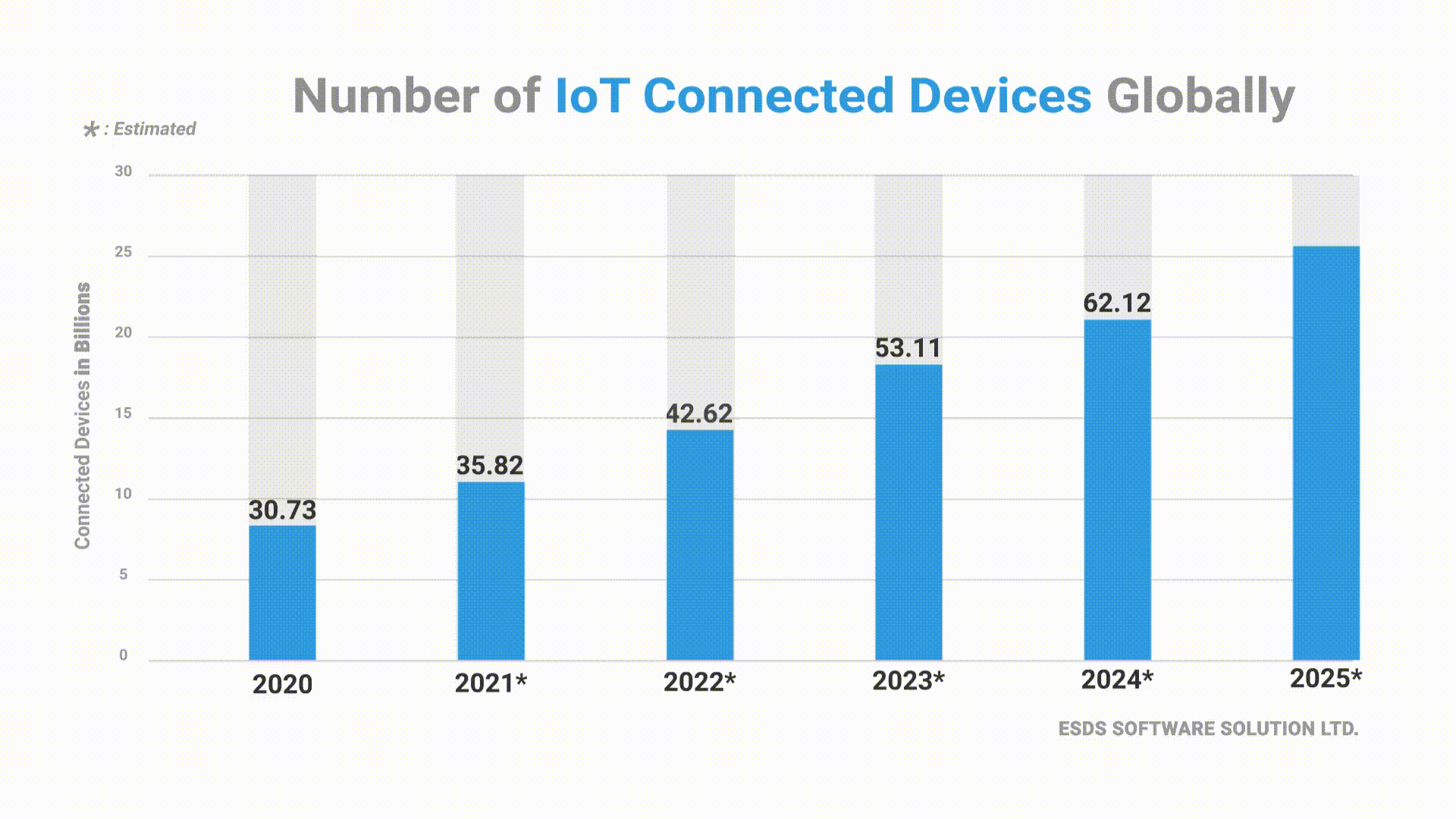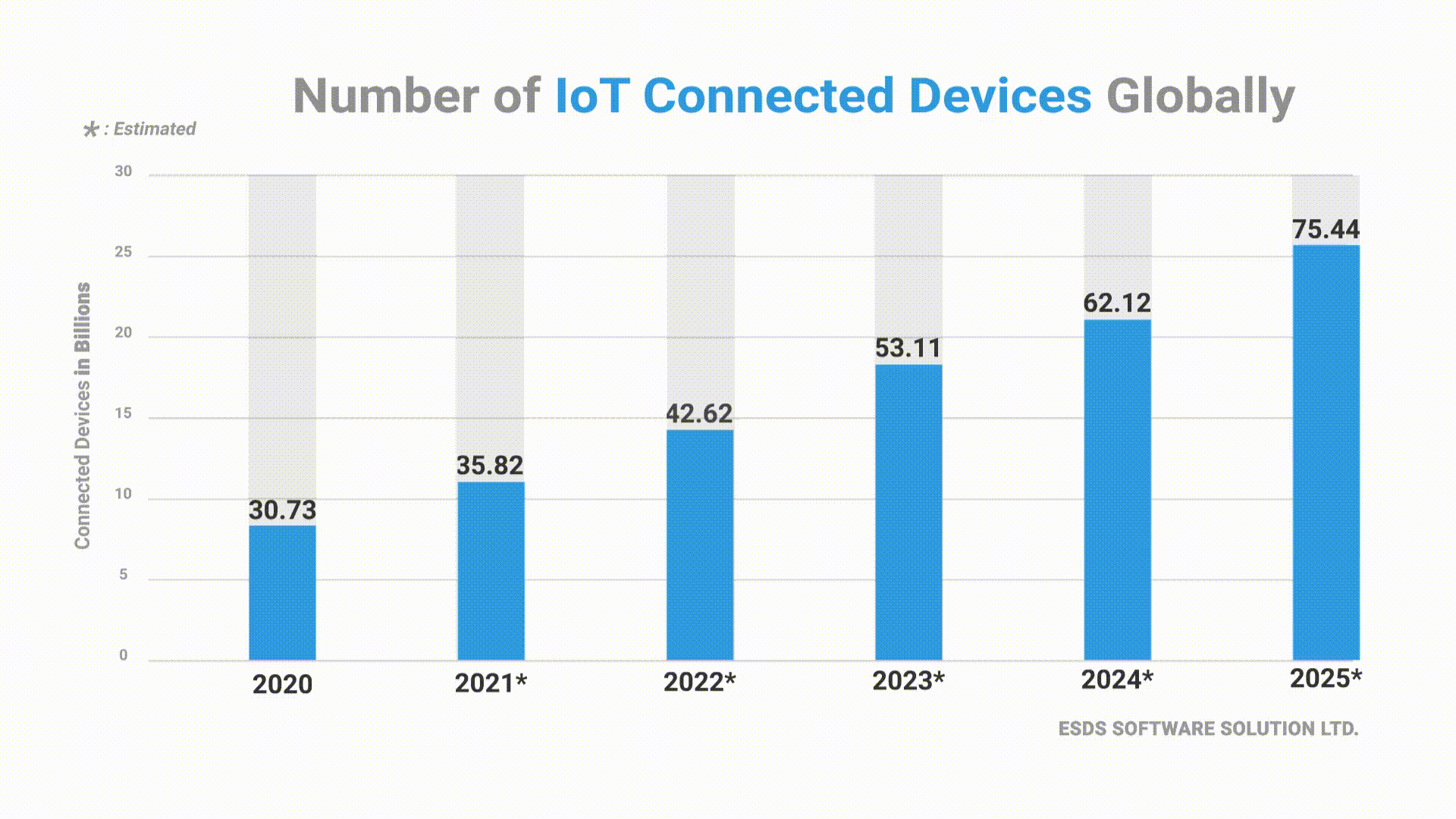
In recent years, after Cloud Computing, IoT has been one of the most significant and emerging technologies of this century. Every day, there have been many IP-connected devices being developed and connected to the Internet. This increased number of connected devices does bring in many benefits to enterprises, but at the same time, they also attract numerous risks.
What Should CIOs Know About IoT Security?
As a CIO or CISO of an enterprise, one should clearly understand what IoT Security means. IoT Security includes the physical device security and network security, impacts, the processes, and necessary steps required to protect IoT devices & networks. IoT device security protects systems, networks, and data from a wide range of security attacks. These security attacks are usually focused on the following major vulnerabilities.
- Communication attacks taking place on the data transmitted between IoT devices
- Lifecycle attacks on IoT devices while getting transferred from user to maintenance
- Attacks taking place on the device software
- Physical attacks that directly target the device
Why IoT Security?
An IoT Security plan allows the users to protect their devices against all forms of vulnerabilities when deploying the best security levels as per their applications. Techniques like cryptography play a significant role in countering communication attacks. Security services from a trusted provider like ESDS protect the IoT platforms against various forms of lifecycle attacks. The devices in an IoT ecosystem are connected to the Internet, which makes them vulnerable to multiple cyberattacks.
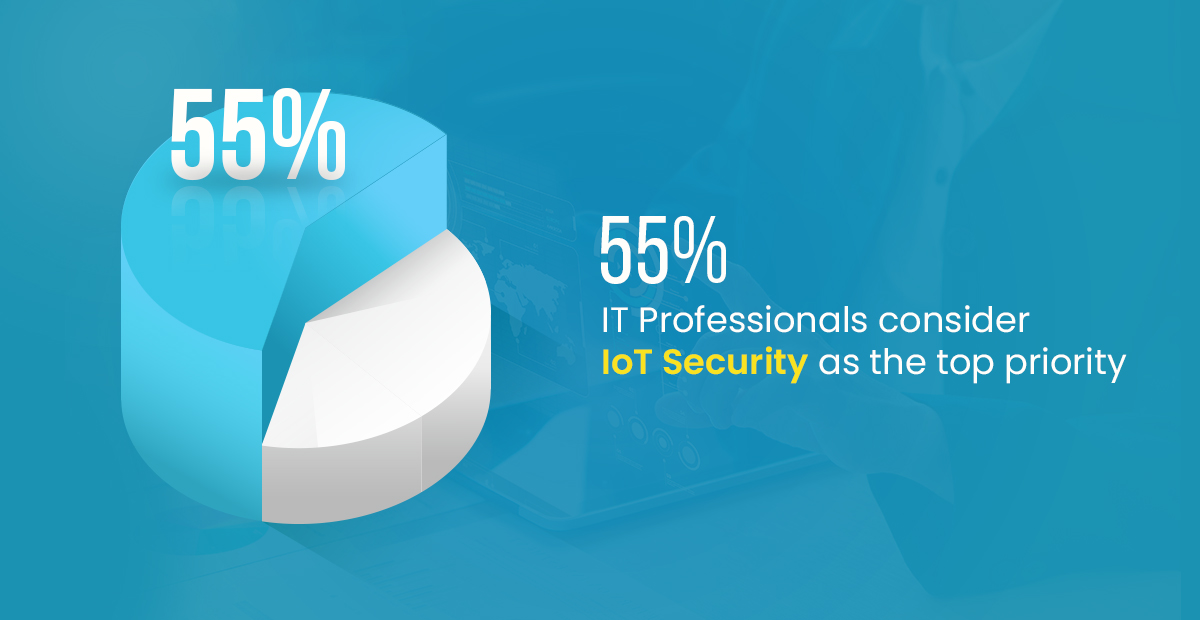
As per online research, about 55% of IT professionals consider the security of their IoT Platforms as the top concern. Cyber attackers continuously look for malicious techniques for exploiting critical information across multiple points in an IoT ecosystem, from servers to cloud platforms.
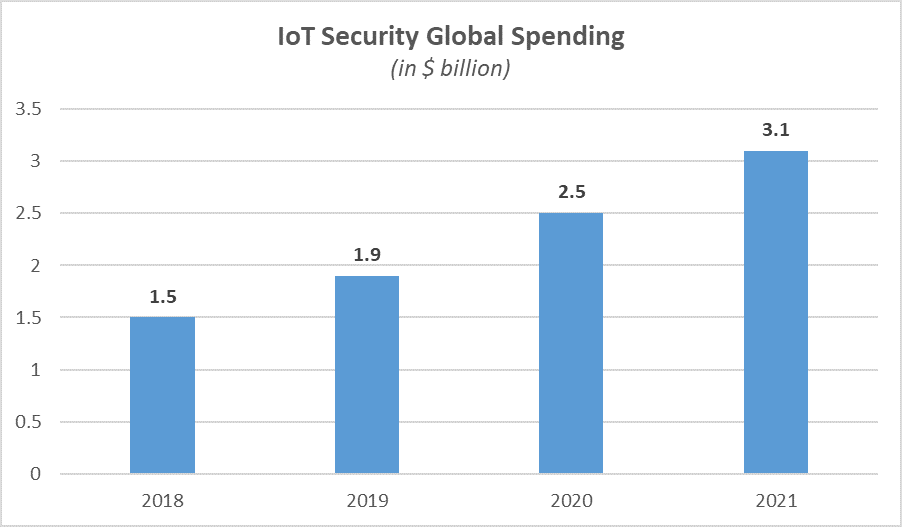
In the past 3 years, spending on IoT Security has doubled. In 2018, the expenditure was worth $1.5 billion, and by 2021, it is expected to increase to $3.1 billion, growing at a CAGR of 27.4%.
Common IoT Security Challenges
Manufacturers are continuously competing to deliver the best & latest devices to their end-users. While manufacturing, they often tend to neglect the due considerations of security issues that might be directly related to the IoT devices, which hamper the IoT-connected devices.
The following are some common security challenges that are associated with IoT devices-
1. Lack of Testing & Updating
Most of the manufacturers don’t carefully handle these devices & their associated security risks. As a result, they don’t get sufficient updates. The security of devices gets compromised with time and can eventually become the potential target for hackers & other security issues.
2. Brute-Forcing & Default Passwords
Reports suggest that manufacturers are selling their IoT devices with preset & default credentials. If a manufacturer uses weak credentials and login details, it makes the IoT devices vulnerable and exposed to hacking and brute force attacks.
3. IoT Malware & Ransomware
With the number of IoT-connected devices increasing, there will be a parallel increase in the malware & ransomware that will exploit these devices. Traditional ransomware attacks use encryption for locking the users out of their devices; however, modern-day malware & ransomware combine different forms of attacks.
4. Data Security & Privacy Concerns
Data privacy and security concerns have been the largest issue in the modern-day digital, interconnected world. Large volumes of data are being transmitted, processed, and stored by enterprises having diversified IoT devices. This might contain critical information whose breach or lapse can cause substantial losses, resulting in privacy and data security violations.
5. Difficulty in Identification of Smaller IoT Attacks
For an enterprise, one must understand that the smaller attacks also hold the same threat level as that of the larger ones. The larger IoT attacks can be easily detected through modern-day security tools. However, there are chances that the smaller attacks go unidentified. Through these small-scale attacks, hackers can leak out critical information rather than gaining access to large data volumes in one go.
How Can IoT Security Protocols Help?
IoT Security protocols define a set of standards designed to ensure secure communications between network-connected devices. IoT devices’ communication can take place in two different methods, either through long-distance communication (over Internet protocol-based network) or short-range communication (through non-IP-based protocols). With IoT Security Protocols in place, devices can communicate through a centralized channel, ensuring their communication takes place securely. These centralized channels run as a service on Cloud platforms, and Cloud hosting providers must deploy these IoT security protocols to avoid data breaches and leaks to cybercriminals.
Concluding Words
Presently, IoT and Security are not exactly co-related and are not present at the same levels. With the number of IoT-connected devices increasing every day, more security-based complex challenges are bound to emerge. There has to be a defined standardization that ensures security at various places since many commonly used objects hold user information and are also connected to the Internet. These Internet-connected devices serve as the base for any cyberattack in the absence of security mechanisms. Hence, for any enterprise, it is now inevitably important to make their devices smarter and at the same time ensure their security also.
- Considering Data Centers in India to Overcome Economic Conditions - May 10, 2022
- Determining Why Your Organization Needs Web Application Security - February 11, 2022
- How Does a Business Benefit with Managed Services - January 21, 2022