Determining Why Your Organization Needs Web Application Security
If you are a CIO or a key decision-maker of your organization, having a well-defined web security mechanism can be extremely beneficial. Web application security depicts an array of processes, technologies, and methods implemented for protecting an end-user’s web servers, web applications, and web services from all forms of online threats & malware. Having a robust web application security mechanism in place becomes essential for enterprises. This security technique protects users’ and enterprises’ data from all forms of data theft and obstacles that hinder business continuity.

Understanding Web Application Security
Web application security is a broad term, and it encapsulates an array of methods and strategies for securing web browsers and applications. The techniques help secure an organization’s digital assets against various cyber threats. Most web application security threats arise due to exploited weaknesses by pushing vulnerabilities through these weaknesses. Cybercriminals deploy malicious techniques to determine these ‘loopholes’ in security mechanisms & get away with user-critical data to have personal gains.

Some common targets of these web-based attacks initiated by cybercriminals include content management system tools, database administration tools, along SaaS applications. These systems are often targeted because these hold high business, and a single cyberattack can lead to substantial monetary & non-monetary losses.
Common Web Application Vulnerabilities
Web application vulnerabilities occur in the absence of defined inputs/outputs that cybercriminals exploit for manipulating source codes or gaining illegal access to sensitive data. These vulnerabilities open the scope for an array of attacks, comprising of the following.
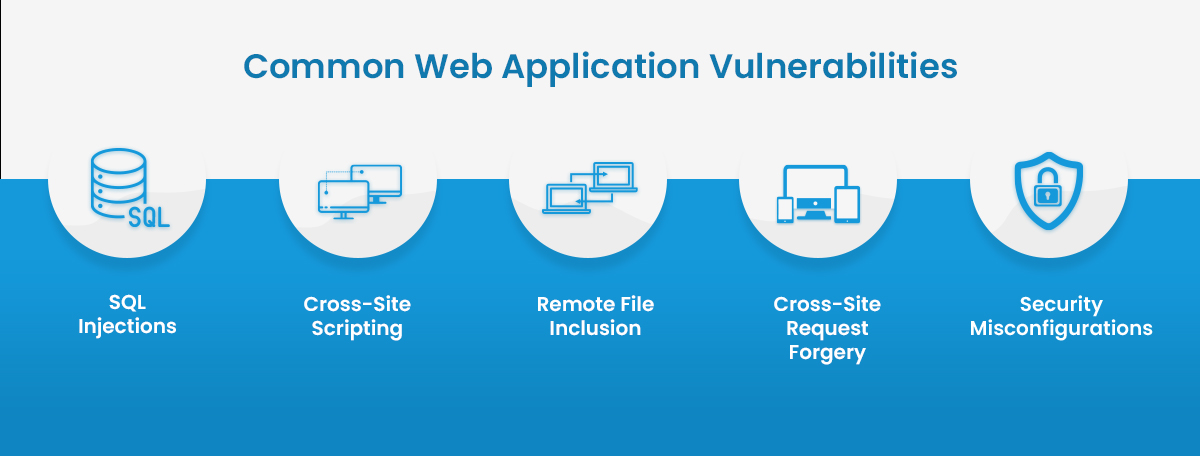
1. SQL Injections
This attack occurs when cybercriminals use a malicious SQL code to manipulate the backend databases. Consequences of an SQL injection include an unauthorized view of lists, deletion of databases & getting unprivileged access to critical data.
2. Cross-Site Scripting (XSS)
Cross-Site Scripting attacks take place when a cyber attacker injects client-side scripts into a webpage for either accessing information or tricking the user into revealing his essential information.
3. Remote File Inclusion (RFI)
This attack form is used to inject a file into a web application server remotely. This vulnerability can cause the execution of malicious scripts or codes inside an application, along with data theft or manipulation.
4. Cross-Site Request Forgery (CSRF)
This attack takes place when a malicious web application allows a user’s web browsers to perform unwanted actions on a website that he has logged on.
5. Security Misconfiguration
Security Misconfigurations include various forms of vulnerabilities focused on lacking maintenance to a web application configuration. A secure configuration needs to be deployed for different applications, frameworks, application servers, web servers & platforms.
The above are only some of the common web-based attacks denting web applications. Using tools such as WAF & website vulnerability scanners can be extremely handy for countering web application attacks.
It is important to understand that eliminating or cleaning up vulnerabilities might not be feasible, considering many applications are in a constant development phase. Also, applications are continuously integrated to create a complex coding environment.
But Why Web Application Security Remains a Growing Concern?
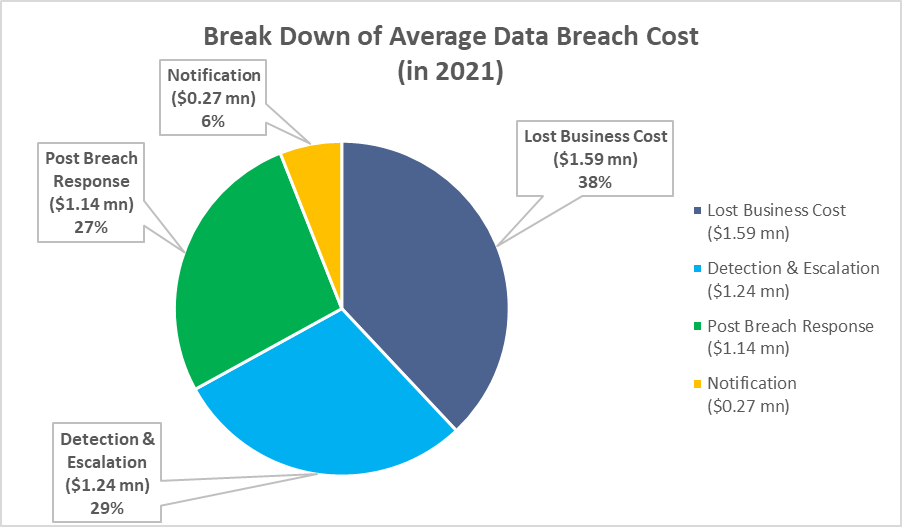
It is worth noting that in 2021, the average cost of a data breach rose to $4.24 million from $3.86 million in 2020.
The following illustration shows the break down average data breach cost, amounting to $4.24 million (in 2021)
These web application attacks are unforeseen & can’t be determined beforehand. The pandemic outbreak in 2020 has been a prominent factor in various cyberattacks. The lockdown forced various companies to adopt the ‘new normal.’ The absence of a technical expert team opened chances for hackers & criminals to exploit open security threats & vulnerabilities. Vulnerabilities within web applications bring in multiple security concerns that further evolve into large-scale attacks.
Preventing Web Application Security
Enterprises can prevent online attacks and ensure web server security if they have a reputed application penetration testing tool with the security team. An enterprise’s in-house security teams need to be equipped with web application tools to ensure overall protection against any form of security incidents. Website penetration testing tools deeply analyze security exploits and provide solutions to mitigate these threats. Organizations must also ensure they have security applications like web application scanners and application security tools to avoid all forms of data breaches.
How Application Security Reduce Risks
With the world rapidly adopting the pace of digitalization, web application security can be compromised by an array of concerns. Various forms of web vulnerabilities such as OWASP Top-10, Cross-Site Scripting, SQL Injections are some common attacks used by cyber attackers that can cause serious implications on either a single application or the organization. Managed Security teams of an organization can develop mitigation control mechanisms of an attack through detailed identification of online vulnerabilities. Evaluating the impact of these attacks against each application can be used to set the priorities of application security testing.
Types of Web Application Security Testing
For achieving the highest security levels, organizations have now started focusing on deploying security practices during the development & after the development phase. Security testing is usually classified into the following categories.
1. Static Application Security Testing (SAST)
SAST or Static Application Security Testing relies on the application’s actual code. It is a type of white-box testing. It can be easily installed on a security system to any existing server, involving various elements to implement successfully. SAST can detect multiple issues in the source code and determine issues like input validation, numerical errors, and path traversals. SAST can also be used across compiled codes; however, it requires binary analyzers.
2. Dynamic Application Security Testing (DAST)
DAST or Dynamic Application Security Testing checks for all forms of online vulnerabilities when an application is run-time. It depicts a form of black-box testing, where the security testers have no idea of the application’s underlying architecture. Users can perform DAST checks over various components such as scripting, sessions, data injections, authentications, responses & requests.
3. Interactive Application Security Testing (IAST)
Interactive Application Security Testing or IAST tools combine the common approaches of SAST & DAST. Tools deployed in interactive application security testing check whether the common vulnerabilities can be exploited in a running application. IAST tools merge various testing techniques for creating multiple testing techniques to develop several advanced attack scenarios through pre-collected information regarding the data and application flow. These tools repeatedly perform dynamic analysis, and these cycles ensure IAST tools continue to understand the application.
4. Manual Application Penetration Testing
Manual Application Penetration Testing is used for simulating cyberattacks against a running application. Various tools usually carry out penetration testing like a website vulnerability scanner, including both DAST & SAST tools. This form of testing is the most common excepted security technique for ensuring overall web application security. In the cybersecurity domain, OWASP is an organization that looks after web application security testing.
Concluding Remarks
Web applications today can be hindered due to various online threats & vulnerabilities. Hence, the security of these applications becomes mandatorily important for the business & IT heads of organizations. There are various practices to ensure the safety of applications, such as different forms of testing (as discussed in the blog) or deploying tools like website vulnerability scanners or even application security scanners.
- Considering Data Centers in India to Overcome Economic Conditions - May 10, 2022
- Determining Why Your Organization Needs Web Application Security - February 11, 2022
- How Does a Business Benefit with Managed Services - January 21, 2022
