Top 10 types of cyber-attacks that can compromise an organization’s security
Cyber-attacks are a growing threat to organizations of all sizes, and it is critical for companies to understand the various types of attacks they may face. Here are the top 10 types of cyber-attacks that can hamper an organization’s security:

Top 10 types of cyber-attacks
Phishing:
This type of attack is used to steal sensitive information or login credentials by tricking individuals into revealing their passwords or other personal information through fraudulent emails or websites.
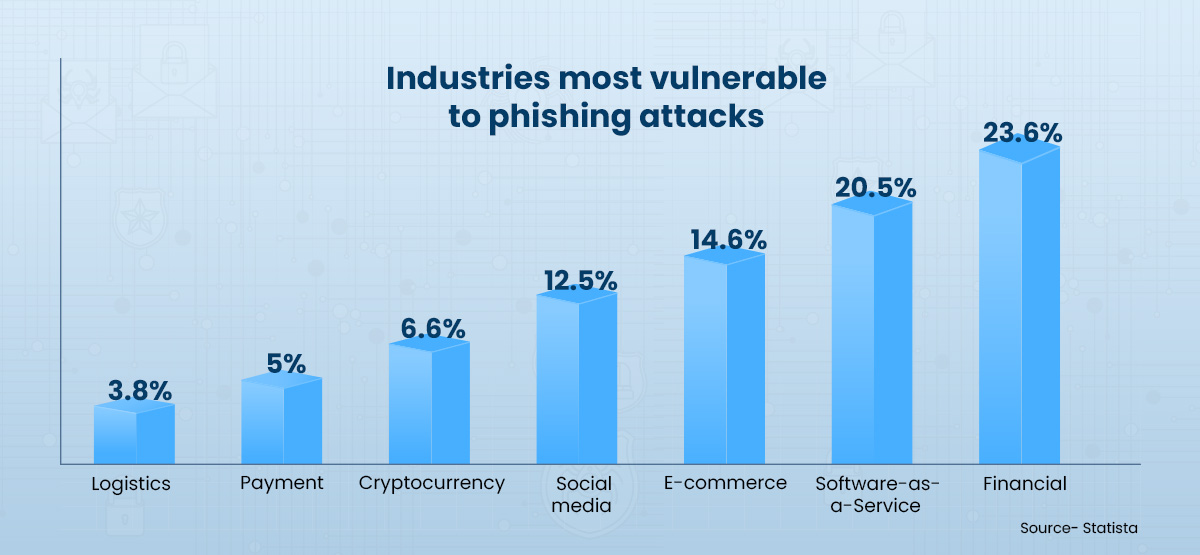
Here is a list of some key cyberattack statistics as per IBM’s 2022 Cost of Data Breach Report-
- With 16% of breaches, phishing was the second most common cause, costing $4.91 million.
- During this year, 19% of data breaches used stolen or compromised credentials as their main attack vector.
- Averaging $4.5 million, breaches brought on by lost or stolen passwords.
- With a 243-day identification period and an 84-day containment period, this type of breach had the longest life cycle.
- The average amount of time taken to find and contain a data breach is 16.6% longer than this amount of time.
- With a 16% frequency and a cost of $4.91m, phishing was the second most frequent reason for breaches.
Ransomware
In a ransomware attack, hackers encrypt an organization’s data and demand a ransom payment for its release. These attacks can cripple an organization’s operations and result in significant financial losses. In 2022, ransomware remained the most common type of malware. As a result of its capacity to extort large amounts of money, it has grown in popularity among cybercriminals. Cybereason. Ransomware attacks surged dramatically in 2022, with 25% of all breaches involving ransomware attacks, according to Verizon’s 2022 Data Breach Investigations Report.
Malware
Malware attacks involve introducing malicious software into an organization’s systems to steal data or disrupt operations. Common types of malware include viruses, Trojans, and spyware. Viruses are spread more widely by employees with infected machines. 61 percent of organizations experienced malware spread by employees in 2020. By 2021, it had risen to 74 percent; by 2022, it had reached 75 percent – the highest infection rate since the SOES survey began in 2016.
Denial of Service (DoS)
DoS attacks are used to overload a network or website to make it unavailable to users. These attacks can result in significant downtime and lost revenue. Additionally, it makes it challenging for the host to recognize and defend itself against the real source of the attack. Legitimate users cannot access network resources like information systems and devices. That’s terrible news for hosts and their clients. Unfortunately, that’s also the primary security feature many of the best web hosting providers take pride in preventing DDoS attacks from disrupting services.
It is relatively easy to launch a DDoS attack and extremely difficult to mitigate it. DDoS attacks are often too massive to handle, even with some quality CDN providers. Here are some important cyberattack statistics related to DoS attacks
- In 2022, the YoY DDoS growth is 109%.
- In Q2 of 2021, the average DDoS attack lasted 30 minutes; a year later, they averaged 50 hours.

SQL Injection
In an SQL injection attack, hackers manipulate a database through user input on a website to access sensitive information. These attacks can result in the theft of sensitive data, such as financial information or intellectual property.
Man-in-the-Middle (MitM)
MitM attacks involve intercepting communication between two parties to steal data or alter the information being transmitted. These attacks can occur on unsecured Wi-Fi networks or through email or instant messaging.
Cross-Site Scripting (XSS)
XSS attacks involve injecting malicious code into a website to steal user data or execute unauthorized actions. These attacks can result in the theft of sensitive information, such as login credentials or credit card numbers. More than 60% of web applications are thought to be vulnerable to XSS assaults, which together make up more than 30% of all web application attacks. Even the well-known OWASP Top Ten list includes XSS issues as one of the serious dangers to online application security.
Advanced Persistent Threat (APT)
APT attacks are long-term, targeted attacks by state-sponsored actors to steal sensitive information. These attacks are designed to go unnoticed for extended periods of time and can result in significant damage to an organization’s operations and reputation.
Password Attacks
Password attacks are attempts to crack passwords through brute force, dictionary, or rainbow table attacks. These attacks can result in unauthorized access to sensitive information and systems. According to Verizon, 80% of hacking incidents are caused by stolen and reused login information. Every 39 seconds, hackers try to guess usernames and passwords using scripts, according to WebsiteBuilder.org’s 2021 report.
Insider Threats
Insider threats can come from employees or contractors who have access to an organization’s systems and data. These individuals can cause significant damage by intentionally or unintentionally exposing sensitive information or disrupting operations.
According to the 2022 cyberattack statistics for Cost of Insider Threats: Global Report
- 62% of all incidents are caused by negligent insiders.
- 25 % of all incidents are caused by negligent insiders with stolen credentials.
- 14% of all incidents are caused by malicious insiders.

It is essential for organizations to be proactive in their defense against cyber-attacks. This includes implementing strong security measures, such as firewalls, anti-malware software, and two-factor authentication, as well as regular security training for employees. By understanding the top types of cyber-attacks, organizations can better protect themselves and reduce the risk of a successful attack.
Want to secure your digital assets? Get Cloud Security! Know more about Cloud Security here: Cloud Security Basics: What You Need to Know to Keep Your Digital Assets Safe
Grow resilience against Cyberattacks with ESDS Security Solutions
ESDS Security Solutions can help organizations grow resilience against cyberattacks by providing a comprehensive set of security services and solutions. These services can help organizations protect their digital assets and prevent data breaches through measures such as data encryption, firewalls, access controls, and others. The company’s security experts can also help organizations detect and respond to cyber threats in real-time, minimizing the damage caused by attacks and ensuring timely recovery. With ESDS Security Solutions, organizations can reduce the risk of cyberattacks and ensure the continuity of their business operations in the face of potential security incidents.
Here is a List of Security Solutions by ESDS
- SOC-as-a-Service: A team delivering 24/7 security monitoring services to detect, prevent, investigate, and respond to cyber threats.
- eNlight WAF: An intelligent, cloud-hosted Web Application Firewall
- eNlight WebVPN: Cloud-based clientless VPN with a built-in WAF for providing Layer 7 security
- VTMScan: A complete website security audit tool for enhanced protection against malware, Trojans, and other OWASP Top-10 vulnerabilities.
Be Vigilant. Talk to our security experts for Complete digital protection.
- Top 5 Data Center Trends for 2024 - October 11, 2023
- Top 15 Cloud Computing Trends 2024 - October 4, 2023
- What is Infrastructure Monitoring and Why Infrastructure Monitoring Tool is Important for Your Business? - September 20, 2023
