Solving Five Key Challenges with a Security Operations Center (SOC)

Your current cyber security environment, your requirements, the nature of your company, and where your organization stands on the security maturity graph will all affect whether a Security operations center (SOC) is the best choice for you. However, if your cyber security team is having similar issues, you might want to think about using a Security operations center (SOC as a service).
Five Key Security Challenges and a Security operations center (SOC)’s Solution –
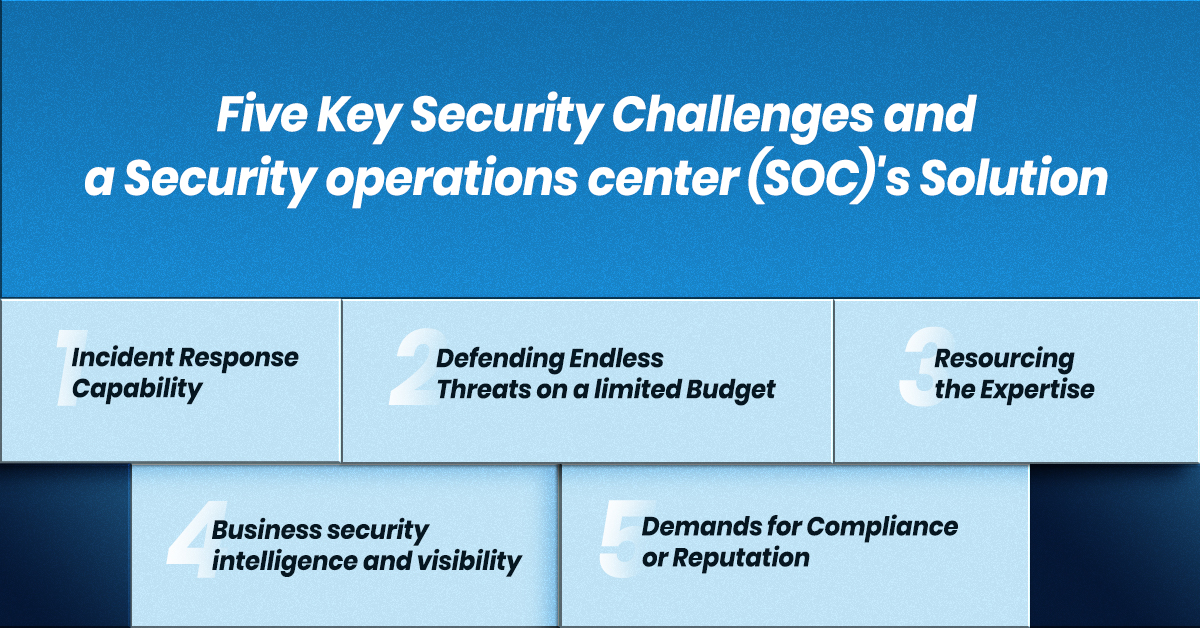
1. Incident Response Capability
The Problem
As security experts, we are aware that security incidents will happen despite our best efforts. When incident response is sluggish, inconsistent, or unreliable, there should be a worry. No matter how well-prepared your security is, if you can’t guarantee a quick response to incoming attacks, you’re exposed.
A Security Operations Center (SOC)’ Response
For the vast majority of cyberattacks, the commercial damage is mitigated the faster the reaction is. Security operations center (SOC)’s have the ability to use powerful defence tools, frequently combining automation, round-the-clock monitoring, and containment with on-site qualified professionals to give a quick incident reaction – the human factor.
2. Defending Endless Threats on a Limited Budget
The Problem
Tools for monitoring, detection, assessment, and correction are expensive. There may be pressure to keep investing in security solutions if your business is expanding, going through a digital transformation, or facing other substantial changes (to operations, regulatory duties, or compliance). This is to ensure that your organization keeps up with developments and stays secure.
A Security operations center (SOC)’s Response
When compared to the cost of deploying the same solutions and hiring the employees required to administer them efficiently internally, Security operations center (SOC)’s can offer access to a wide range of top-notch technologies. This reduces the danger of vendor sprawl and its related difficulties, helping to stabilize costs.
3. Resourcing the Expertise
The Problem
budgetary restrictions play a large role, but not only. With a 3.4 million+ workforce deficit, the worldwide cybersecurity business is now dealing with an alarming skills gap. This dearth of skilled expertise is making it difficult to find and keep employees, leaving security teams with worrying knowledge and resource gaps—something the bad guys are all too aware of.
A Security operations center (SOC)’s Response
A good Security operations center (SOC) should function as an extension of your current security team, giving you dependable access to the knowledge you lack on staff without having to worry about keeping in-demand employees or adding additional team members should your security stack grow.
4. Business security intelligence and visibility
The Problem
Most cyber security risks are caused by unintentional activity, system abuse, and improperly designed controls. These threats must be recognised and mitigated before they may pose a problem in order to maintain a secure enterprise security posture – visibility and contextually aware intelligence are essential.
A Security operations center (SOC)’s Response
When a Security operations center (SOC) is given complete visibility, analysts can get a bird’s-eye view of your security stack and (increasingly through a combination of granular analysis and machine learning) identify risk behaviors and potential configuration errors to target threats at the source, providing proactive rather than reactive security.
5. Demands for Compliance or Reputation
The Problem
Industry-specific rules require a more thorough security provision than is viable or feasible in-house for many firms.
A Security operations center (SOC)’s Response
A Security Operations team (SOC) as a service is frequently the best option for companies worried about reputational harm following a potential breach or those required to achieve compliance criteria that are beyond the capacity of in-house staff. While your company might only need a small staff of IT specialists for day-to-day operations, there might be tight guidelines regarding, for instance, data security. In these circumstances, a Security operations center (SOC) is a great method to outsource the task to satisfy your unique requirements.
Team up with ESDS’ Security operations center (SOC)
Amidst the ever-evolving landscape of security challenges, considering a transition to a SOC service can prove to be a highly worthwhile decision. With cyber threats becoming increasingly sophisticated and persistent, having a dedicated Security Operations Center (SOC) is essential for safeguarding your organization’s critical assets.
ESDS’ Security Operations Center (SOC) services provide an all-encompassing solution to address your security needs. With our assistance, you gain the ability to proactively detect and respond to previously unknown dangers, enabling swift neutralization of threats that may otherwise evade traditional security measures. By integrating ESDS‘ Security Operations Center (SOC) services into your security strategy, you can free your organization from the burden of time-consuming security procedures. This allows you to focus on your core business functions while benefiting from a strengthened security posture that ensures your data and digital assets are safeguarded against the ever-present cyber risks.
- Why does your business need Endpoint Detection and Response (EDR)? - May 15, 2024
- Are your business endpoints completely secure? - March 26, 2024
- Is Colocation key to transforming your data center management strategy? - March 22, 2024
