Guarding Your Business’s Core: The Vital Role of Privileged Access Management (PAM)

Businesses face an ever-growing array of cyber risks in today’s hyper connected digital landscape. The risk of improperly handled privileged access stands out among them. Because they provide access to sensitive data and vital systems, privileged accounts are often targeted by cybercriminals looking to gain unauthorized access. We’ll discuss the significance of Privileged Access Management (PAM) and the many advantages provided by ESDS PAM solutions in this blog.
The Growing Threat Landscape
Cyber dangers are growing in sophistication and scope as businesses depend more and more on digital infrastructure to spur innovation and growth. Cybercriminals are always coming up with new strategies to take advantage of weaknesses and obtain unauthorized access to vital systems and sensitive data. Privilege accounts, which have higher permissions and unfettered access to important resources, are among their favourite targets. The ramifications of unapproved access, whether it be via insider threats, stolen credentials, or unpatched vulnerability exploitation, can be disastrous for businesses of all kinds.
The Role of Privileged Access Management (PAM)
Privileged Access Management (PAM) is a cybersecurity practice that centers on regulating, overseeing and safeguarding access, to accounts in a company. These accounts, usually owned by IT admins, service accounts and other privileged individuals come with heightened permissions that give them control over IT assets. If not managed correctly these accounts could serve as an entry point, for cyber attackers to breach networks, data and disrupt business activities.
PAM solutions address this risk by implementing robust controls and mechanisms to govern privileged access. These include:
- Access Control: Enforcing the principle of least privilege by granting users only the permissions necessary to perform their duties.
- Session Monitoring: Recording and analyzing privileged sessions in real-time to detect anomalous behavior and potential security threats.
- Password Management: Securely storing, rotating, and vaulting privileged account passwords to prevent unauthorized access.
- Audit and Compliance: Generating comprehensive audit trails and reports to demonstrate compliance with regulatory requirements and industry standards.
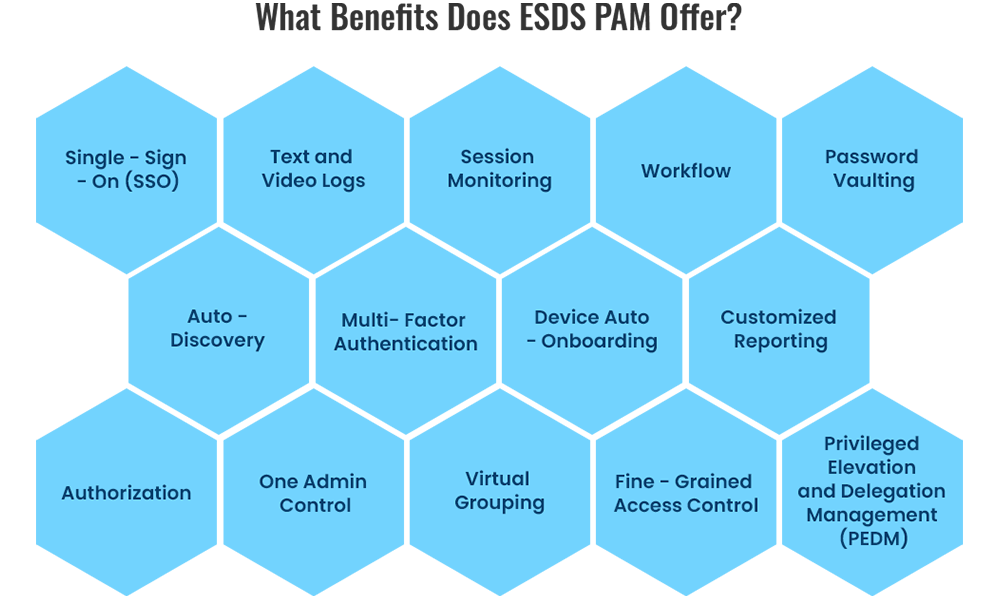
- Single-Sign-On (SSO): Improve ease and security by streamlining access control by giving users a single login experience for a variety of apps and systems.
- Text and Video Logs: To provide thorough audit trails for compliance and forensic analysis, keep thorough records of privileged access activities in both text and video forms.
- Session Monitoring: Keep an eye on privileged sessions constantly in order to quickly identify and address any suspicious activity or unauthorized access attempts.
- Workflow: To increase operational effectiveness and decrease human labour, automate and optimize privileged access management workflows.
- Password Vaulting: To avoid unauthorized access and credential theft, securely manage and store passwords for privileged accounts in a centralized vault.
- Auto-discovery: Provide thorough coverage and visibility by automatically locating and onboarding privileged accounts and devices within the IT environment.
- Multi-factor authentication: Reduce the possibility of unwanted access by adding an extra degree of protection to access control with multi-factor authentication.
- Device Auto-onboarding: Easily integrate new devices into the PAM system while enforcing security standards-maintaining access regulations and controls.
- Customized Reporting: To obtain insights and successfully satisfy regulatory obligations, provide customized reports on privileged access activities and compliance status.
- Authorization: To reduce the possibility of privilege abuse, define and implement granular permissions and access limits based on roles and responsibilities.
- One Admin Control: To improve visibility and control, centralise privileged account administration and management under a single administrator interface.
- Virtual Grouping: Organize privileged accounts into logical groups for easier management and access control, improving scalability and efficiency.
- Fine-Grained Access Control: Specify precise permissions and privileges for individual users or groups, ensuring a granular level of control over privileged access.
- Privileged Elevation and Delegation Management (PEDM): Facilitate secure privilege escalation and delegation processes, enabling authorized users to perform privileged tasks while minimizing risks.
- Why does your business need Endpoint Detection and Response (EDR)? - May 15, 2024
- Are your business endpoints completely secure? - March 26, 2024
- Is Colocation key to transforming your data center management strategy? - March 22, 2024
Comprehensive benefits of ESDS PAM Solution
ESDS offers a comprehensive suite of Privileged Access Management solutions tailored to the unique needs of modern businesses. Our PAM offerings provide a wide range of benefits, including:
Conclusion
In today’s world of increasing cyber threats, Privileged Access Management (PAM) has become essential, than an option—it plays a crucial role in any robust cybersecurity plan. ESDS provides top notch PAM solutions with features to assist companies in protecting their valuable assets from unauthorized access and malicious actions. By teaming up with ESDS for PAM services companies can reduce risks bolster security measures and uphold the confidentiality and integrity of their data and systems.
Secure your company’s core with ESDS Privileged Access Management (PAM)solutions . Get in touch with us today to discover more about our security solutions and safeguard your organizations future, in the era.
