Why Privileged Access Management Matters Now More Than Ever

If the past year has taught IT and security teams anything, controlling privileged access should be the business’s top priority. When a large section of the workforce started working remotely, there was a rush to expand access so people could do their jobs from home. However, this may have accidentally resulted in staff having incorrect access levels. This is especially troublesome if the organization’s access levels are elevated or privileged.
Privileged accounts access important data and are frequently used to run any program, collaboration tool, or transaction, generally with little tracking or oversight. Hundreds of privileged accounts are often discovered within businesses, and they may have no control, making them more vulnerable to exploitation or misuse.
According to the 2020 Verizon Data Breach Investigations Report, two primary sources of data breaches for enterprises during this disruptive environment were compromised credentials, which might be lost or stolen, and privilege abuse, caused by willful activities by internal personnel. The average cost of a data breach today is $3.86 million, according to the Cost of a Data Breach Report, so the consequences of a data breach will likely continue for years.
Some Privileged Access Management Details:
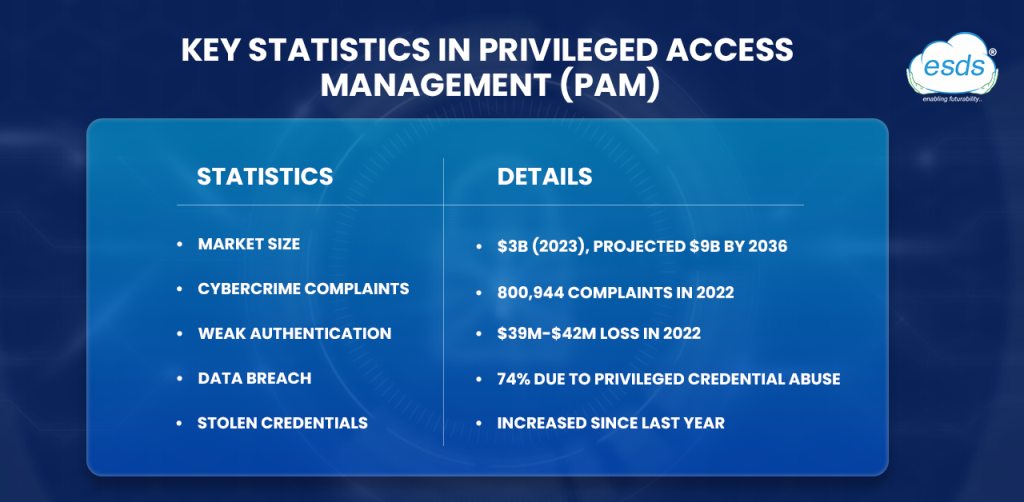
With compromised credentials being a primary source of breaches, companies cannot afford to overlook the need for privileged access management (PAM). Companies are increasingly seeking more effective and economical methods to secure their data with PAM solutions.
This article will examine several types of privileged accounts, explain why privileged access management is important, and provide some best practices for managing privileged access.
What Kinds of Privileged Accounts Are There?
Within your IT environment, privileged accounts hold the ‘keys to the kingdom.’ While they are seldom associated with specific persons, these accounts may be used to accomplish almost anything with little or no monitoring. Elevated rights include the ability to change system settings, install or uninstall software, and create, delete, or edit user accounts. Elevated privileges might sometimes just mean access to sensitive information.
There are three distinct types of privileged accounts:
- Root/Administrator Accounts: These accounts have complete access to a server’s services and data. They are regarded as the most lucrative targets for threat actors.
- System Accounts: These accounts are responsible for performing operating system services and can change the appropriate files and configurations. They are often included with the operating system.
- Service/Application Accounts: These accounts execute processes and programs via automated, frequently unattended actions. They frequently possess or have access to data, resources, or configurations inaccessible to non-privileged individuals.
Why Is Privileged Access Management Important?
Privileged access management is a vital security control that allows enterprises to simplify the definition, monitoring, and administration of privileged access across their IT systems, applications, and infrastructure. PAM systems consolidate administrator profile management and enforce least privileged access, allowing people to access what they need.
Privileged access management systems decrease or eliminate the need to exchange passwords by restricting access to authorized users and allowing for better authentication mechanisms. They also combat insider threats and privilege misuse by enforcing the concept of least privilege, which requires people to have the necessary access to perform their job tasks. Linking access to job roles and individual accounts reduces the requirement for superusers with global access.
Best Practices for Privileged Access Management
Managing privileged accounts may initially appear overwhelming, but some best practices may help businesses properly manage these higher-level accounts.
1. Centralized management across all physical and virtual servers: allows you to monitor and audit which users have access to which devices.
2. Integrate with Existing Corporate Directories: With different corporate directories and identity management systems, privileged account management must work smoothly to automatically associate team and group identities with the appropriate systems, applications, and data.
3. Ensure Contextual Authentication: Contextual authentication allows enterprises to provide strong authentication to certain servers and roles that pose a higher risk.
4. Impose Secure Keystroke Recording: For sensitive sessions, you must also be able to adapt to impose complete keystroke recording, which allows administrator activities to be recorded in detail.
5. Implement Granular Access Control: Rather than enabling functional accounts like ‘root’ or’ sysdba’ to log in, you must have enforceable permission rules requiring specific and auditable user accounts. Implement fine-grained security controls to specify and enforce who has enhanced privileges, when, how, and from where.
6. Consolidate Audit Logging: Protecting privileged accounts entails consolidated audit logging that fully records user activity. Effective PAM systems should provide unified audit logs and reports from all server domains, which should be stored in a separate security domain.
Conclusion
ESDS’s Privileged Access Management (PAM) solution assists businesses in protecting their assets against unauthorized access and criminal activity. PAM is a cybersecurity approach for managing access to systems, processes, and privileged accounts. ESDS’s PAM solution provides a variety of functions, including single sign-on (SSO), session monitoring, password vaulting, MFA, and fine-grained access control.
Privileged elevation and delegation management (PEDM) can assist enterprises in reducing the attack surface, limiting the extent of a breach, preventing malware infection, and improving operational performance. PAM systems limit access to the least privileged user and centralize administrative duties. They also utilize technical barriers to limit access to approved users.
- Why Do You Need Vulnerability Assessment and Penetration Testing? - March 13, 2025
- How to Choose the Right Private Cloud Service Provider in 2025? - February 27, 2025
- Why Cloud Migration is Essential: Benefits, Challenges, and Expert Tips - February 24, 2025
