A Comprehensive Business Guide to SOC Services
$3.92 million– yes, that was the average amount of a data breach in 2019! With businesses getting dependent on technologies & cybersecurity attacks always on the rise, this cost of a data breach is expected to rise further. Companies also perceive Cloud-based security as a significant threat if they don’t have dedicated security staff. However, on an optimistic note having a Security Operations Center (SOC) is helping the companies of all sizes to manage their cybersecurity risks effectively.

What is SOC?
SOC represents a team of cybersecurity professionals that are proactively dedicated to preventing all kind of data breaches as well as other cybersecurity threats. The final goal of SOC is to monitor, detect, investigate, and respond to all the potential forms of cyber threats at all times.
The team members present in a SOC team deploy various technological solutions along with processes. These include- security information and event management (SIEM) systems, firewalls, detection of breaches, and intrusions. The SOC teams also deploy various tools for performing vulnerability scans in the network against possible threats and weaknesses.
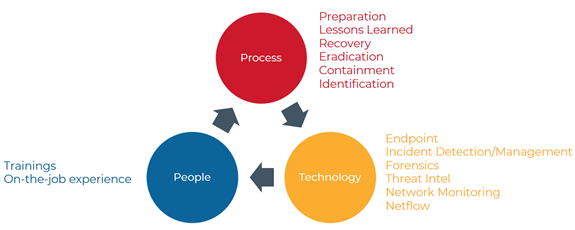
Benefits of Using SOC-as-a-Service
A business can get the following benefits when they deploy SOC-as-a-Service in their organization
- Preparing the organization for all forms of advanced cyberattacks
- A cost-effective solution as most of the companies fail to hire cybersecurity experts and the required software & hardware for mitigating cyberattacks
- In-house expertized team of cybersecurity professionals for monitoring and mitigating cybersecurity threats
- Proactive defense management by gathering and generating alerts through a continuous monitoring
- Adhering to all major compliances as well as regulatory guidelines like- RBI, GDPR, PCI-DSS, HIPAA
Pillars of Modern SOC Operations
Companies have a choice to either build an in-house SOC or outsource to a managed security service provider that will offer SOC services. For smaller businesses that have a crunch of resources for developing an in-house team, outsourcing to a reputed SOC provider can emerge as a cost-effective option.
By capitalizing on the following pillars of security operations, businesses can have a detailed approach towards cybersecurity and its threats.
- Creating Awareness of Business Assets
The first objective in any modern SOC is the discovery of business assets like tools, technologies, hardware, and software. These assets are different for any company and thus, it is essential to create a comprehensive awareness of these assets that are available for identifying and preventing the security issues.
- Preventive Security Monitoring
In any cybersecurity attack, prevention is considered to be more effective than reacting. Instead of responding to threats every time, the SOC team is dedicated to monitoring the business network at all times. By having continuous monitoring of the network, the SOC teams can identify all forms of malicious activities and preventing them beforehand, so that the severity of damage is reduced.
- Maintaining Activity and Communication Logs
During any security-related events, the analysts present in the SOC team need to track the activity and communications that took place on a network the loopholes that would have existed in these events. Thus, the analysts in the SOC team are assigned the task of performing comprehensive log management for all the activities that took place on the network and report back.
- Prioritizing Security Alerts
When security incidents take place, the incident response team present in the core SOC team is responsible for deciding the order and severity of the cybersecurity incident. This allows the SOC to pay attention to focusing on preventing and responding to higher security alerts that can prove to be dangerous for businesses.
- Altering Defence Mechanisms
An effective cybersecurity strategy is a constant process of improving defense mechanisms. To address the forever changing dynamics of cybersecurity threats, the SOC works continuously towards adopting and modifying the network’s defense mechanisms as in when needed.
- Maintaining Compliance
Every calendar year, more and more compliance regulations are being added in the cybersecurity domain owing to the data security of the users. Besides maintaining and aligning to the compliances, SOC also shields the business organization against all legal formalities so that these businesses always remain compliant with the latest regulations.
SOC Models
The SOC models, whether deployed in-house or outsourced, don’t fall under the same business model. The SOC processes and procedures differ on various factors that might include some of the unique security needs of a business.
Various SOC models can be classified into the following categories.
- Internal SOC
An internal SOC is a business’s in-house team that comprises of security and IT professionals that work within the business organization. Internal SOC members are present across other business departments.
- Internal Virtual SOC
The internal virtual SOC comprises of ad-hoc security professionals that are working remotely. The team members in this SOC model are responsible for reacting to security as an alert is received in the network.
- Co-Managed SOC
The co-managed SOC model comprises of security professionals who work closely with a cybersecurity service provider. This SOC model combines a partial in-house team of security experts along with a third-party SOC provider to achieve a co-managed approach towards cybersecurity.
- Command SOC
The Command SOCs play a pivotal role in coordinating the other SOCs present inside the organizations. They are generally found in those organizations that can accommodate multiple in-house SOC services.
- Fusion SOC
A fusion SOC is the SOC model that oversees the efforts of the business’s bigger IT security team. The main objective of a fusion SOC model is to guide and assist the internal IT team on security grounds.
- Outsourced Virtual SOC
An outsourced virtual SOC comprises of team members that work from remote locations. An outsourced virtual SOC is more of a third-party service offering that provides security services to those organizations that are not able to manage the in-house SOC team.
ESDS SOC Services’ Offerings
ESDS has two offerings under its SOC Services, namely- Security Insight Services and Eagle Eye Services.
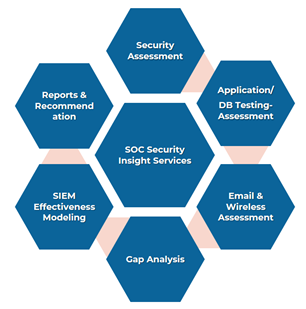
- Security Insight Services
Security Insight Services is a one-time assessment offered by ESDS. ESDS also provides consultation on procedures for enhancing the security of the organization by mapping their needs with Security Insight Services.
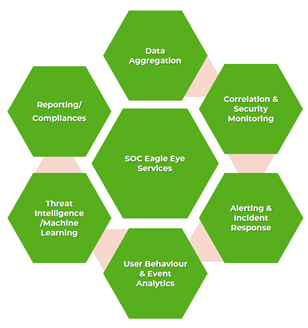
- Eagle Eye Services
Eagle Eye Services is a continuous SOC monitoring assessment offered under ESDS’ SOC Services. Under the Eagle Eye Services, there are two plans from which the customer can choose from as per his needs, namely Standard Plan and Gold Plan.
Concluding Remarks
Businesses today face constant threats of growing cybersecurity. Thus, with a managed and trusted SOC-as-a-Service provider, companies can leverage various benefits that can be extremely helpful for improving the overall cybersecurity posture. By having an expert team of dedicated information security professionals, they can proactively monitor the incoming alerts on the business network and take action accordingly. The SOC services also strengthen defense mechanisms for a business securing their crucial data.
- Considering Data Centers in India to Overcome Economic Conditions - May 10, 2022
- Determining Why Your Organization Needs Web Application Security - February 11, 2022
- How Does a Business Benefit with Managed Services - January 21, 2022
