Best Security Operations Center (SOC) Practices for your organization
Security ratings are increasingly important in security operations centers (SOC). To effectively contribute to the development of organizational-wide security culture, security analysts must learn to read, analyze, and report security ratings. Here, we go over how analysts may create a security operations center that effectively uses ratings to assess and reduce cyber threats.

Security Operations Center and its working –
A security operations center serves as the focal point for an organization’s monitoring, detection, response, and analysis of cyber threats. The SOC constantly keeps an eye on everything, including internal network traffic, desktop PCs, servers, endpoint devices, the Internet of Things (IoT), databases, and other things.
SOC team members often aren’t focused on creating the security strategy itself; instead, they’re there to put that strategy into action, which includes putting defensive measures in place as needed and assessing the fallout after an incident. Teams employ technology to collect data, check endpoints for vulnerabilities, and verify regulatory compliance while protecting sensitive data.
A clearly defined security strategy that is in line with corporate objectives forms the basis of the SOC’s activity. From then, a variety of tools, features, and functions must be used to build and maintain your infrastructure to deploy and support the plan.
Your Best Practices for a Successful Security Operations Center
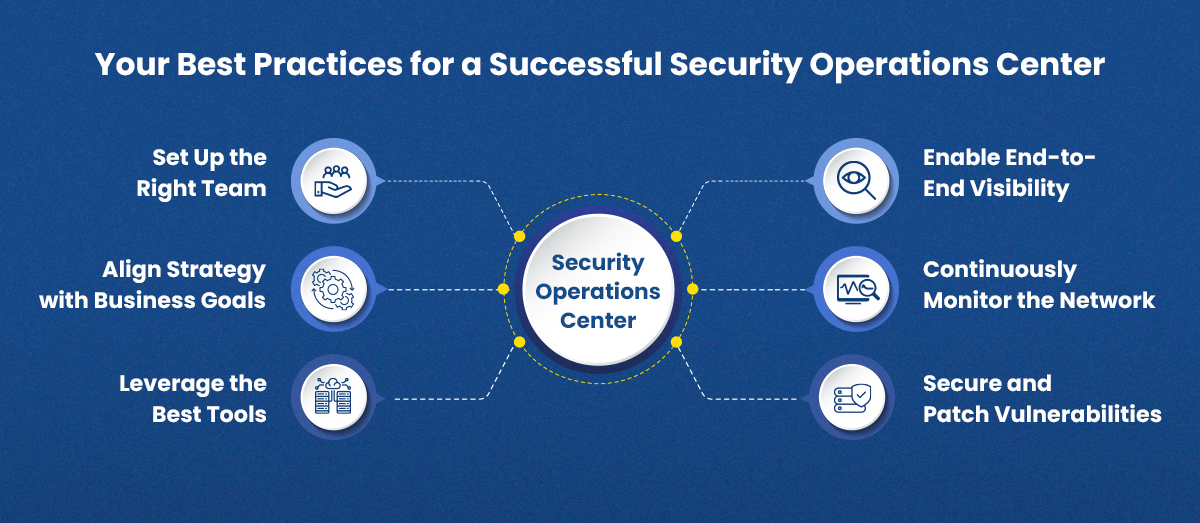
The security operations center’s position in an organization is crucial since the threat landscape is constantly changing and growing. In order for the security operations center to fulfill its role of safeguarding business assets against cyberattacks, it must be efficient and well-organized. Here, we list the top 7 ways to build up a successful security operations center.
- Set Up the Right Team
In order to prevent a skills gap, the ideal team should contain members with a variety of skill sets. The following abilities should be present in a good SOC team:
- Monitoring of systems and intelligence
- Alert control
- Analyzing incidents
- incidental reaction
- Threat assessment detection of intrusions
In addition to having highly talented and well-trained team members from the start, remaining current also necessitates allocating funds for regular staff training. A good leader who can keep everyone on task and understand the broad picture is also essential for the team, especially when an immediate threat is present. ESDS‘ professional experts form the perfect team for you so that your business is safe and sound.
- Align Strategy with Business Goals
Business objectives and an organization’s cybersecurity posture should always be compatible. This implies that it must be evident to business stakeholders why SOC investment is crucial in terms of the value the security operations center team generates.
An assessment of each’s current state throughout the entire firm is the first step in aligning the SOC strategy with business objectives. This kind of risk assessment offers the chance to list current assets and find any holes or prospective risks. The company can then decide what measurements and KPIs security operations center analysts should monitor in order to keep a clear picture of its continuous contribution to corporate goals.
In order to direct the security operations center team, it’s a good idea to establish a clear set of policies and procedures. However, these processes should allow for ongoing reflection and optimization in order to keep on top of changing risks.
- Leverage the Best Tools
There is a big ocean of security tools and technologies, and they range widely in terms of compatibility, quality, and cost. Remember that the best instruments only offer the best protection if they don’t leave any holes, and you can keep an eye on and retain control over all parts. Because of this, it is important to do extensive research on which tools are appropriate for your team before making a purchase.
Common implements are:
- Endpoint security programs
- software with firewalls and antivirus
- Automatic application security that is intelligent
- Tools for Security Information and Event Management
- Asset tracking and discovery programs
- tools for data monitoring
- tools for threat intelligence
- Security scores solutions for monitoring compliance
The likelihood of missing a breach or being unable to react fast is decreased by high interoperability across your chosen tools, which also guarantees improved coverage. Budgets for security operations centers are frequently constrained; therefore, it is important to spend money on tools in a wise way that maximizes functionality, compatibility, and future-proofing.
- Enable End-to-End Visibility
The security operations center team needs complete insight into cyber risk management, systems, and real-time data across the company to offer the greatest protection available. Silos make it more difficult for the security operations center team to monitor particular assets or prevent them from being monitored at all. This makes it easier to miss an active threat and harder to neutralize it in a timely manner.
Only what the security operations center team can see can be protected. Lack of visibility can have serious repercussions in a threat environment when network security can be compromised by just one device. The team must be able to centrally identify all digital assets and combine all monitoring and data into its analysis.
- Continuously Monitor the Network
Security lapses can occur at any time and are continually changing. Organizations must regularly monitor their networks to keep ahead of dangers. Continuous monitoring enhances risk management, enabling quick identification and reaction, and gives real-time data on crucial activities.
This is frequently accomplished using automated technologies that provide security alerts whenever there is questionable activity. For instance, early warning systems lower the danger of assaults by facilitating quick action. Analysts can use the data that continuous monitoring software can aggregate to examine issues and enhance network security in the future. Additionally, it offers user behavior insights that may be used by teams to assess the effects of updates and changes.
- Secure and Patch Vulnerabilities
It’s standard practice for computer networks to have vulnerabilities. The security operations center team requires a plan for providing frequent security updates and fixes in order to prevent exploitation. If vulnerabilities are not patched as soon as they are found, the network is left widely exposed to data theft, malware installation, and other types of potential harm.
Patching is an essential component of good security operations center procedures since it assists in fixing bugs as soon as they are found. Patches should be quickly distributed with complete insight into detected vulnerabilities and what each patch fixes, and they should be prioritized based on risk across the whole network.
Our Verdict
The security rating platform from Security Scorecard gives security operations centers access to cybersecurity threats throughout their whole ecosystem. Teams can quickly assess risk using our A-F rating scale, enabling them to take preventative action as necessary. The platform prioritizes alerts and continually monitors across ten risk categories. This shortens the time it takes security analysts and teams to triage and qualify warnings and streamline operations and response.
ESDS’ SOC services enable the scores may also be readily incorporated into reports for leadership or the board, making it simpler for security operations center teams to convince corporate stakeholders of their worth and, as a result, to obtain the funds and resources required to continuously stay one step ahead of threat actors.
- Why does your business need Endpoint Detection and Response (EDR)? - May 15, 2024
- Are your business endpoints completely secure? - March 26, 2024
- Is Colocation key to transforming your data center management strategy? - March 22, 2024
