22
Jul
Things You Should Know Before Migrating To Cloud Hosting Solutions
If you go into a cloud environment, above all, prepare a checklist for a successful transition into the clouds. Without a doubt, the cloud has became a hot topic all over the world because of the mobility and flexibility at lower cost. Cloud Infrastructure is the next-generation platforms that can provide tremendous value to any... Read More
18
Jul
IDC, A Technology To Map Customers
Knowing the profile of customers has always been a competitive edge, even in past times. However, the dynamism of the modern market demands much more than that old custom of being personally greeted by the owner of the company at the door of the establishment. In times of major mergers and acquisitions, organizations are faced... Read More
18
Jul
10 Ingredients Of Outsourcing IT Services And A Little More
Many outsourcing companies that are associated with the loss of control of information and critical business activities. The fact is that, if outsourcing can be well executed and in accordance with the real needs of those contracts, the benefits can be seen in a short time. In this sense, I chose 10 ingredients for outsourcing... Read More
09
Jul
Differences Between Linux and Windows Dedicated Server Hosting
Until a few years ago, the Linux and Windows server hosting services were radically different. Today’s systems platform compatibility of the companies hosting these differences will reduce dramatically. The way to access the server is one of the main differences between the two types of services. Both allow access via FTP, a protocol for transferring... Read More
07
Jul
What Are The Famous Robots Of Google?
The robots, crawlers or spiders are small programs sent by Google to investigate, analyze and scan millions of web pages, and are usually one or the other, linked through the links that pages offer. What Does This Mean? More all, ranging from the network for documents, once the first one, continuing their search and indexing... Read More
05
Jul
What Version Of Apache / MySQL / PHP Are You Using?
As far as we are handling Apache, MySQL, and PHP, they fall into the category of “Application of repute” to support and upgrade security at their latest stable versions, but all of them and at some point in time their respective projects, may have experienced more vulnerable periods from high or low. If you are... Read More
05
Jul
How To Know That Joomla Site Is In Danger Of Intrusion?
It is very common nurtured false belief that “to summon a website, simply install Joomla! and ready ” . While Joomla has been engineered to provide facilities to a wide range of users, including those with little or no programming knowledge level websites, this does not mean at all that maintain safety on our sites... Read More
02
Jul
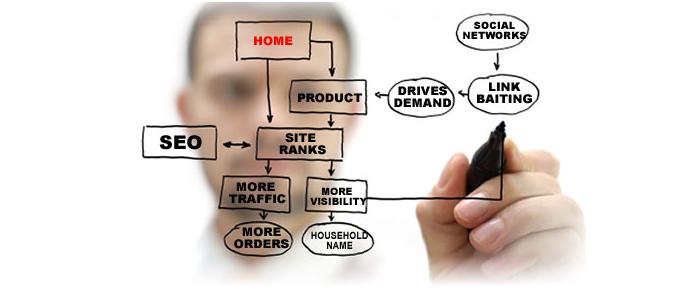
Search Engine Optimization (SEO): What is it?
You probably already have heard of Search Engine Optimization (SEO). It is a set of actions to improve the positioning of your site in search engines, that is, when the user types a keyword in Google , the goal of SEO is to make one or several of the pages on your website , appear... Read More
01
Jul
Cloud Hosting Defined
Cloud Hosting, also called clustering is a hosting service that operates a network of servers that are connected permanently. As a shared hosting is limited to the resources like disk space, bandwidth, memory, processing speed of a single machine, the cloud servers provide access to a virtually infinite infrastructure and do not necessarily need to... Read More
29
Jun
Web server with CentOS + Apache
In this brief article we will cover the installation and configuration of Apache on CentOS and some other functions required in today’s web servers. Although there are already plenty of material about it, a simple Google search returns a number of texts already, I decided to write about it because it is something simple that... Read More