31
May
Phishing – ESDS VTMScan
Introduction Phishing is a method used by attackers to trick you into disclosing personal information such as username, password, credit card and banking information. The goal for the attacker is to steal your information and/or your money. The information gathered can be used to open fraudulent accounts in your name or make purchases using your... Read More
31
May
Link Crawling
Introduction Link crawling is the process of capturing all the pages (URLs/links) present on a website. It helps us know how many and which pages are there in our website. Site owners can also crosscheck whether these page are legitimate or not. ESDS VTMScan Technique We crawl all the pages which are present on a... Read More
31
May
Banner Grabbing
Introduction Banner Grabbing is collection of the information related to your website such as webserver information, header information and open ports. Banner grabbing is a technique used to gain information about a computer system on a network and the services running on its open ports. An intruder can use banner grabbing in order to find... Read More
31
May
Content Change Monitoring Scan.
Introduction Content Change Monitoring (CCM) is a webpage service which monitors the changes made in web pages of the website. ESDS VTMScan instantly sends alerts if there is any change takes place in the content of the concerned web page. It helps in dealing with hacking and zero-day attacks quickly and efficiently. It is important... Read More
31
May
GHDB – Google Hacking Database
Introduction The Google Hacking Database (GHDB) is a categorized index of Internet search engine queries designed to uncover interesting, and usually sensitive, information made publicly available on the Internet. In most cases, this information was never meant to be made public but due to any number of factors this information was linked in a web... Read More
31
May
Malware Scan
Introduction Malware is short for ‘malicious software’ that performs unwanted action on websites and webservers and steals sensitive data such as credit card numbers or other personal information (identity theft). Malware can actually affect your livelihood if you use your website for business. Think about it, if you visit a site once and you see... Read More
31
May
Domain Reputation
Introduction Domain reputation is reputation of domain in World Wide Web. If the domain is suspected of containing malicious code, harmful programs, or is a suspected phishing site then it gets blacklisted. If the domain is blacklisted then Google will keep that domain away from people and the will affect the SEO of that domain.... Read More
31
May
Content Management System Scan
Introduction CMS is a Content Management System that is used to develop websites/blogs. Some of the most popular CMSs are WordPress, Joomla, and Drupal. Multiple themes and plugins are used in CMS to develop a website and many times these themes and plugins are vulnerable. If you’re using the vulnerable plugins and themes then your... Read More
30
May
Proactive Approach: The key to drive success
Proactive & Reactive Approach For many businesses, the default approach to customer service is to respond to clients/events after a problem arises. This reactive method might satisfy the customer and solve the problem temporarily, but it won’t surprise or delight them. Instead, imagine if you could solve problems even before customers have to call you.... Read More
23
May
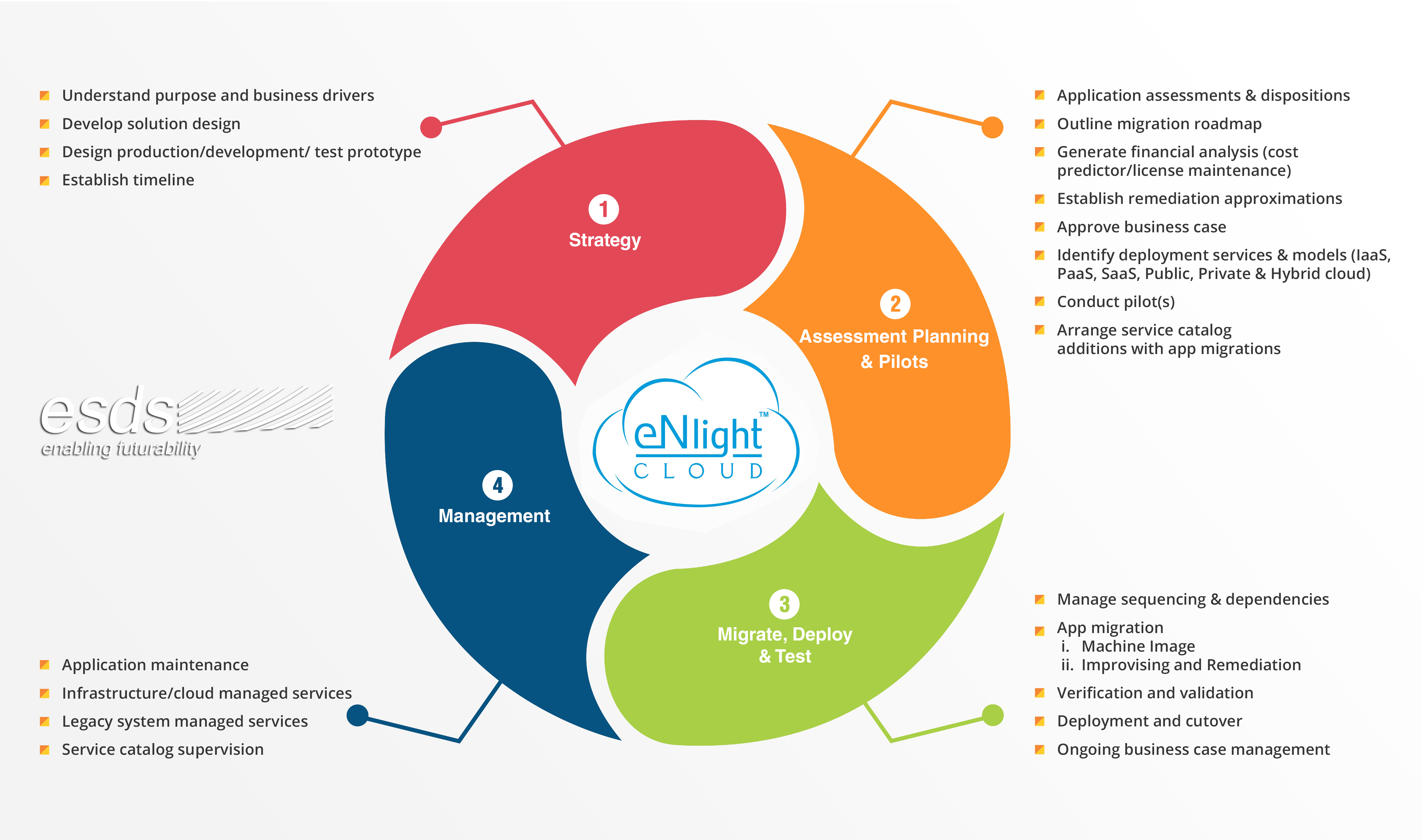
Guaranteed Seamless Migration from any cloud to ESDS
Seamless Migration from any cloud to ESDS Seamless Migration is the process of moving user’s server data and configuration from virtual machines to virtual machines and servers to servers across Data centers by Cloud service providers. Enterprises can accelerate their cloud migration journey with eNlight Cloud as it not only integrates with legacy systems and... Read More