Cloud Computing Security Questions
 Companies that think about moving their websites or applications to cloud computing, think about the most important part and that is security issue. But not everyone knows that selection of cloud services can improve the level of protection of their data. As it turns out in practice, the provider offers a higher security level than the one that you can provide within your own infrastructure. The fact is that, the solution of problems is related to security and the service providers. Serving businesses with a turnover of billions of dollars, cloud providers are doing their utmost to ensure the safest possible environment. Nevertheless, cloud computing are a host of new risks to potential users.
Companies that think about moving their websites or applications to cloud computing, think about the most important part and that is security issue. But not everyone knows that selection of cloud services can improve the level of protection of their data. As it turns out in practice, the provider offers a higher security level than the one that you can provide within your own infrastructure. The fact is that, the solution of problems is related to security and the service providers. Serving businesses with a turnover of billions of dollars, cloud providers are doing their utmost to ensure the safest possible environment. Nevertheless, cloud computing are a host of new risks to potential users.
Before you trust cloud, you should make sure that you really ensure a level of reliability required for the safe handling of applications and data storage in the cloud. Fortunately, the increasing competition in the market of cloud computing services has improved the level of service for the users that is more flexible and provides organizations with the best security for cloud computing services.
But before we dive into cloud computing, the client must define a complete list of requirements for the computing platform, including the level of security. In this case, you can ask your question, and ask for the platform that meets your requirements. In order to not make the wrong choice, it is important to decide the questions and ask for the satisfactory answers that you are looking from the provider.
Who is on your side?
To date, the best experts in the field of security is cloud computing security Alliance (CSA). This organization has produced a guidance, including a description of hundreds of recommendations that should be taken into account when assessing the risks of cloud computing. The manual includes 76 pages, but you don’t need to read this document because we have selected the most important recommendations and tried to make a series of questions that a potential provider of cloud computing services should be asked in the first place.
Cloud computing: Questions and Answers
The following points are key questions that you need to ask the cloud computing service provider whose services you plan to use.
Each issue is one of six specific areas, as shown in Figure.
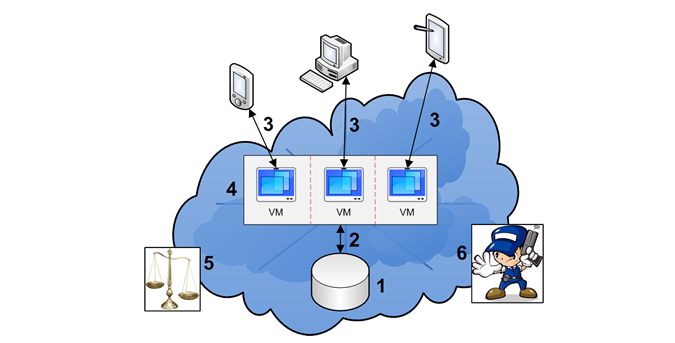
Before addressing the issues you must understand the benefits of using the solutions that are based on standards. And this applies to all areas of security. Proprietary systems are less trustworthy than systems based on standards, as the market players, government agencies, and standards bodies agree with this. That is why the widespread Advanced Encryption Standard (AES) and Transport Layer Security (TLS) have implemented such standards. They have undergone years of analysis and improvement. Moreover, using standards-based security system, the customer receives an additional advantage – if necessary, the customer will be able to change the service provider, as most service providers support the standardized solution.
Another thing that stands clear: how to make sure that the provider performs the data they promise? This will help you to conclude the Service Level Agreement (SLA), or contract on a written document, which will be clearly stated commitment by the cloud service provider. Thus, a series of questions from general to specific, that you need to ask potential providers of cloud computing services, begins here.
1. Preservation of stored data.
Does the service provider ensure the safety of stored data?
The best measure of protection located in the data warehouse is the use of encryption technology. The provider should always encrypt the customer information stored on their servers for preventing unauthorized access. The provider must also permanently delete the data when they are no longer needed and not required in the future.
2. Protecting data in transit.
How a cloud service provider ensures data integrity during transmission (within the clouds and on the way from / to the cloud)?
Transmitted data must always be encrypted and available for the user after authentication. This approach ensures that data is not changed or read by any person, even if it is accessible to them through unreliable nodes in the network. Mentioned technologies were developed during the “thousand person-years led to the establishment of reliable protocols and algorithms (such as TLS, IPsec and AES). Providers should use these protocols, rather than inventing their own.
3. Authentication.
Does a provider know the authenticity of the client?
The most common method of authentication is password protected. However, service providers offer higher reliability, more powerful tools, such as certificates and tokens to their customers. Along with the use of more reliable means to breaking the authentication, providers must be able to work with standards like LDAP and SAML. This is to ensure interaction with the system provider’s user identification and authorization of the client in determining the powers that are granted to the user.
Worst-case scenario – when a customer of the ISP is in the concrete list of authorized users. Typically, in this case, when an employee leaves or is moved to another position may be difficult.
4. Isolation of users.
How data and applications are separated from one customer data and applications from other clients?
Best option: when each client uses an individual Virtual Machine (VM) and virtual network. Separation between the VM and, consequently, between the users, provides a hypervisor. Virtual networks, in turn, are deployed by using standard technologies such as VLAN (Virtual Local Area Network), VPLS (Virtual Private LAN Service) and VPN (Virtual Private Network).
Some providers put data from all clients into a single software environment and due to changes in its code, it try to isolate the customer data from each other. This approach is reckless and unreliable. First, an attacker could find a breach in a non-standard code that will allow him to gain access to data that should not be seen. Second, the error in the code can lead to what one customer accidentally “see” in others data. Therefore, to distinguish between user data, use different virtual machines and virtual networks for a smart move.
5. Legal and regulatory matters.
How the providers apply laws and regulations that are applicable to cloud computing?
Depending on the jurisdiction, laws, rules, and any special provisions may vary. For example, they may prohibit the export of data, require the use of well-defined measures of protection, the availability of compatibility with certain standards and the availability of auditing capabilities. Ultimately, they may require, if necessary, it could be access to government agencies and the courts information. Negligent treatment from the provider to these points may cause its customers a significant costs arising from legal consequences.
The provider is obliged to follow strict rules and stick to a single strategy in the legal and regulatory sectors. This concerns the security of user data, export compliance, auditing, retention, and deletion of data, as well as disclosure of information (this is especially true when a single physical server can store multiple clients). To find out, customers are urged to seek help from professionals, who will study the matter thoroughly.
6. The reaction to the incident.
How provider does responds to the incident, and how much is the involvement in the incident of clients?
Sometimes, not everything goes according to plan. Therefore, service providers are required to adhere to specific rules of conduct in the event of unforeseen circumstances. These rules should be documented. Providers must focus on identifying incidents and minimize their consequences, informing users about the current situation. Ideally, they should regularly provide users with information from the highest level of detail on the issue. In addition, clients themselves must assess the likelihood of problems related to safety and take appropriate action.
The Future of cloud computing security
Despite the fact that today we have a much broader set of tools for security than ever before, the work is far from over. In some cases, to bring to market a technology that helps to solve a new task takes time, even though it had already developed. Here are some of the latest technologies: the data with built-in (Intrinsically Safe Data) and trusted monitors.
Intrinsically Safe Data (self-protected data) – it’s encrypted data, which is integrated with security mechanism. Such mechanism includes a set of rules which may or may not meet the environment in which there is intrinsically safe data. When you try to access the data, the mechanism checks on for safety and disclose them only if the environment is safe.
Trusted Monitor – this software is installed on the provider’s cloud server hosting. It allows you to observe the actions of the provider and send the results to the user who can make sure that the company operates in accordance with the regulations.
When all the research and development of new technologies will be completed, the next step is to implement the service provider. When this happens, customers will be with great confidence that refers to the concept of cloud computing.
Resources:
- How Cloud Computing Is Changing The Labor Market - March 25, 2015
- Adopting Infrastructure as a Service Can be a Good Deal - March 17, 2015
- Will Virtualize? Take These Six Points Into Consideration - March 12, 2015
Cloud computing has been one of the most debatable subject. Cloud computing is a future of web, but it seems to be facing tough issues especially on security front. Good that you have covered some of them Mr. Pravin.