Cybersecurity in the Age of Remote Work: How Digital Hygiene Can Protect Your Company’s Future
As the world shifts towards remote work, cybersecurity has become a top priority for companies of all sizes. With the rise of digital communication and the increasing reliance on cloud services, businesses are now more vulnerable to cyber threats than ever before. Cybercriminals are constantly evolving their tactics, making it crucial for companies to maintain high digital hygiene standards to protect their valuable assets.

In this article, we’ll explore the importance of cybersecurity in the age of remote work and how digital hygiene can help safeguard your company’s future. We’ll discuss the top cyber threats facing modern businesses, the best practices for maintaining digital hygiene, and how to create a cybersecurity strategy that can keep your company safe from potential attacks. So, whether you’re a small business owner or a CEO of a large corporation, read on to learn how to protect your company’s digital assets and maintain a secure future.
Understanding the Top Cyber Threats Facing Modern Businesses
In today’s digital age, businesses are constantly under attack from cybercriminals. From phishing scams to ransomware attacks, cyber threats come in many forms and can cause significant damage to businesses of all sizes. One of the most common cyber threats facing modern businesses is phishing. Phishing is a type of social engineering attack that uses fraudulent emails or messages to trick individuals into giving away sensitive information. These emails often appear to be from a legitimate source, such as a bank or a company that the recipient does business with. Once the victim provides their login credentials or other sensitive information, the attacker can use that information to gain access to their accounts or steal their identity.
Another common cyber threat facing modern businesses is ransomware. Ransomware is a type of malware that encrypts a victim’s files and demands payment in exchange for the decryption key. Ransomware attacks can be devastating for businesses, as they can lead to the loss of valuable data and significant downtime. Other common cyber threats facing modern businesses include malware, DDoS attacks, and insider threats.
What is Digital Hygiene?
Digital hygiene refers to the practices and habits individuals adopt to maintain their online health and well-being. In today’s hyper-connected world, we spend a significant amount of our time on digital platforms. As we navigate the virtual world, we expose ourselves to various risks like cyberbullying, identity theft, phishing attacks, and more. Digital hygiene aims to protect us from such threats by promoting responsible and safe online behavior. So, what is digital hygiene, and why is it essential? To put it simply, digital hygiene involves everything from securing your passwords to being mindful of the content you consume online. It is similar to personal hygiene, where you take measures to keep yourself clean and healthy. In the same way, digital hygiene involves taking steps to keep your online identity and data secure.
Importance of Digital Hygiene in Cybersecurity
Maintaining good digital hygiene is crucial for protecting your company’s assets from cyber threats. Digital hygiene refers to the practices and routines that individuals and organizations use to keep their digital devices and data safe from cyber threats. Good digital hygiene can help prevent cyber-attacks, reduce the risk of data breaches, and protect your company’s reputation. Some of the best practices for maintaining good digital hygiene include using strong passwords, keeping software up to date, and regularly backing up data.
Using strong passwords is one of the most important aspects of digital hygiene. Passwords should be at least eight characters long and should include a combination of uppercase and lowercase letters, numbers, and symbols. Passwords should also be changed regularly, and password reuse should be avoided. Keeping software up to date is also crucial for maintaining good digital hygiene. Software updates often include security patches that can help protect against known vulnerabilities.
Best Practices for Maintaining Digital Hygiene
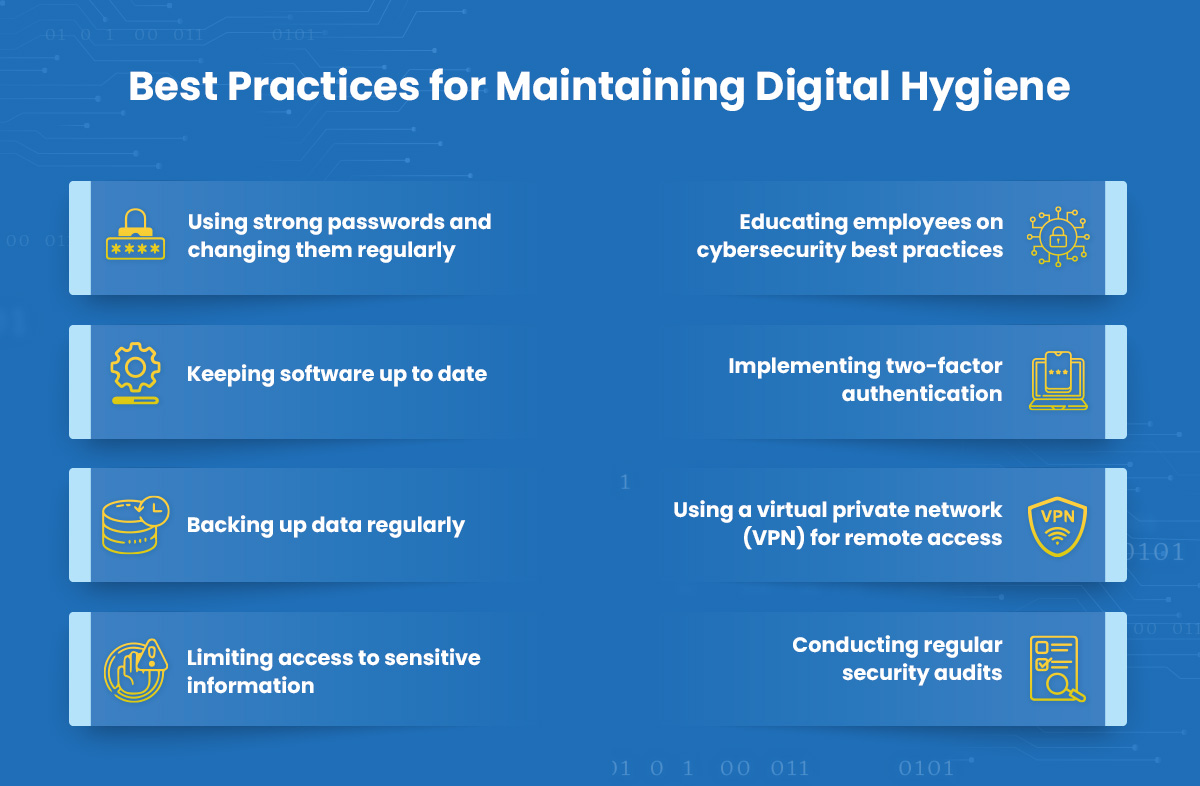
Maintaining good digital hygiene is an ongoing process that requires regular attention and effort. Some of the best practices for maintaining digital hygiene include:
- Using strong passwords and changing them regularly
- Keeping software up to date
- Backing up data regularly
- Limiting access to sensitive information
- Educating employees on cybersecurity best practices
- Implementing two-factor authentication
- Using a virtual private network (VPN) for remote access
- Conducting regular security audits
By following these best practices, you can help reduce your company’s risk of cyber-attacks and protect your valuable assets.
Creating a Cybersecurity Strategy for Your Company
Creating a comprehensive cybersecurity strategy is crucial for protecting your company’s future. A cybersecurity strategy should be tailored to the specific needs of your company and should include a range of measures to protect against cyber threats. Some of the key components of a comprehensive cybersecurity plan include:
- Identifying potential threats and vulnerabilities
- Assessing the risks associated with each threat
- Developing policies and procedures to mitigate those risks
- Implementing technical controls, such as firewalls and intrusion detection systems
- Conducting regular security testing and vulnerability assessments
- Providing cybersecurity training for employees
- Developing an incident response plan
By taking a proactive approach to cybersecurity, you can help protect your company’s future and safeguard your valuable assets.
Key Components of a Comprehensive Cybersecurity Plan
A comprehensive cybersecurity plan should include a range of measures to protect against cyber threats. Some of the key components of a comprehensive cybersecurity plan include:
Risk assessment: A risk assessment is an essential first step in developing a cybersecurity plan. This process involves identifying potential threats and vulnerabilities and assessing the risks associated with each threat.
Policies and procedures: Policies and procedures should be developed to mitigate the risks identified in the risk assessment process. These policies should address issues such as password management, data backup, and remote access.
Technical controls: Technical controls, such as firewalls and intrusion detection systems, can help protect against cyber threats. These controls should be implemented based on the risks identified in the risk assessment process.
Security testing and vulnerability assessments: Regular security testing and vulnerability assessments can help identify weaknesses in your cybersecurity defenses. These assessments should be conducted by a qualified third party.
Cybersecurity training: Providing cybersecurity training for employees is crucial for maintaining good digital hygiene. Employees should be educated on topics such as phishing scams, password management, and social engineering attacks.
Incident response plan: An incident response plan should be developed to address potential cyber-attacks. This plan should include procedures for identifying and containing an attack, as well as steps for recovery and remediation.
By including these key components in your cybersecurity plan, you can help protect your company’s assets and maintain a secure future.
Cybersecurity Training for Employees
Cybersecurity training is crucial for maintaining good digital hygiene and protecting your company’s assets from cyber threats. Employees should be educated on topics such as phishing scams, password management, and social engineering attacks. Training should be conducted regularly, and employees should be encouraged to report any suspicious activity to the IT department.
Tools and Technologies for Improving Cybersecurity
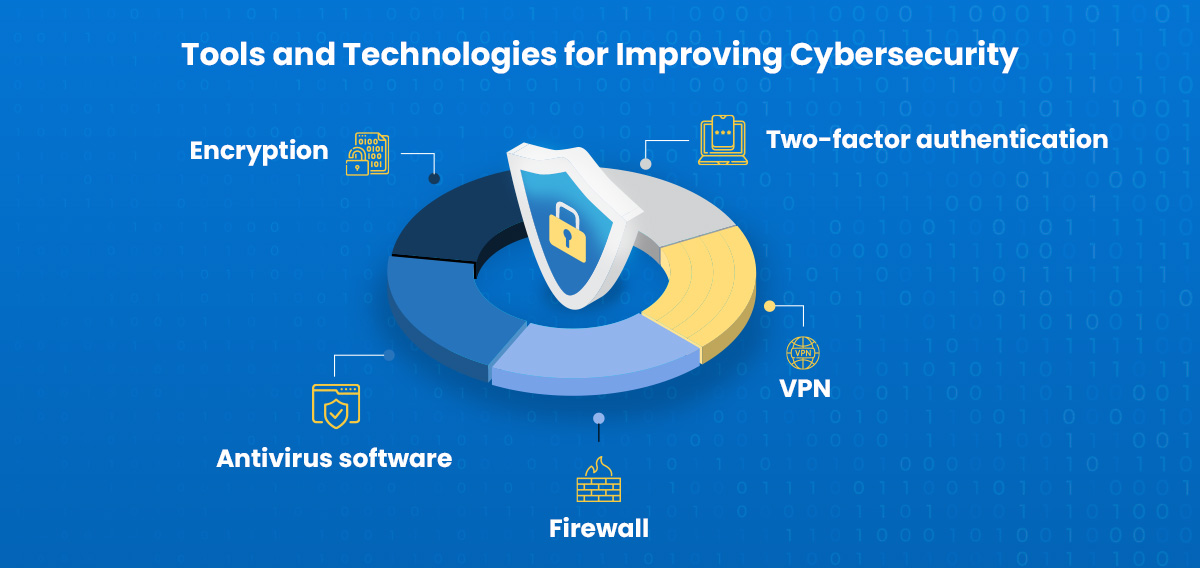
There is a range of tools and technologies available to help improve cybersecurity. These tools can help protect against a range of cyber threats, including malware, ransomware, and phishing scams. Some of the most common tools and technologies used to improve cybersecurity include:
Antivirus software: Antivirus software can help protect against malware and other types of cyber threats.
Firewall: A firewall can help prevent unauthorized access to your networks and devices.
VPN: A VPN can help protect against unauthorized access to your networks and devices when accessing them remotely.
Two-factor authentication: Two-factor authentication can help prevent unauthorized access to your accounts by requiring a second form of authentication, such as a text message or email.
Encryption: Encryption can help protect data from unauthorized access by encrypting it before it is transmitted over the internet.
By using these tools and technologies, you can help improve your company’s cybersecurity defenses and protect against a range of cyber threats.
Cybersecurity Services for Businesses
There is a range of cybersecurity services available to help businesses protect their valuable assets from cyber threats. These services can include everything from risk assessments and vulnerability testing to incident response and remediation. Some of the most common cybersecurity services for businesses include:
- Managed security services: Managed security services provide ongoing monitoring and management of your cybersecurity defenses.
- Incident response services: Incident response services provide support in the event of a cyber-attack or data breach.
- Penetration testing: Penetration testing involves simulating a cyber attack to identify weaknesses in your cybersecurity defenses.
- Cybersecurity consulting: Cybersecurity consulting can provide expert guidance on developing a comprehensive cybersecurity plan.
By using cybersecurity services, you can help improve your company’s cybersecurity defenses and protect against a range of cyber threats.
Conclusion: Protecting Your Company’s Future with Digital Hygiene
In conclusion, cybersecurity is a top priority for businesses of all sizes in the age of remote work. By maintaining good digital hygiene, creating a comprehensive cybersecurity plan, and using the right tools and technologies, you can help protect your company’s assets from cyber threats. Cybersecurity is an ongoing process that requires regular attention and effort, but by taking a proactive approach, you can help maintain a secure future for your company. So, whether you’re a small business owner or a CEO of a large corporation, take the steps necessary to protect your company’s digital assets and maintain a secure future.
- Top 5 Data Center Trends for 2024 - October 11, 2023
- Top 15 Cloud Computing Trends 2024 - October 4, 2023
- What is Infrastructure Monitoring and Why Infrastructure Monitoring Tool is Important for Your Business? - September 20, 2023
