Cybersecurity in The Cloud: Here’s What It Means
Today, the adoption of cloud computing technology has grown tremendously by enterprises. Various leading cloud service providers such as ESDS have expanded their managed cloud services for protecting their existing cloud infrastructure. The customer, along with his cloud provider, is responsible for implementing the right cybersecurity service in the cloud for securing the data present on the cloud.

Despite several benefits, consumers often face certain psychological barriers when protecting their critical data against external vulnerabilities, with data is hosted in a public cloud setup. An online survey revealed that the primary concern of the businesses rests with the data loss and leakage followed by legal and exposure challenges to the data.
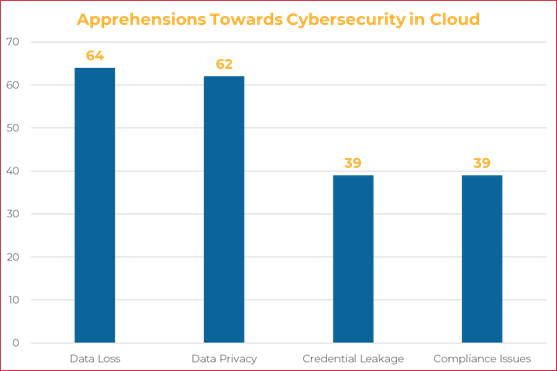
Consumer Apprehensions Towards Cloud Security
- Loss/Theft of Intellectual Property:
Consumers often fear the loss or theft of intellectual property (IP) when moving to the cloud. Online data states that over 3.3 million patent applications were filed in the year 2018. The IPs depict the competitive advantages of the holding companies. Loss or theft of IP can create significant damage to the parent company as various other businesses in the same domain can imitate products as well as processes for much cheaper rates.
- Regulatory Compliance Violations:
Today, every business organization follows specific compliance guidelines defined in its industry. A trusted & reputed cloud service provider, however, ensures that its cloud computing services align to the defined compliance standards that an organization needs to follow—not adhering to these guidelines cause compliance-related violations in the cloud computing security.
- Minimal Visibility of the Cloud Ecosystem
One of the key concerns that businesses often face with a cloud computing solution is that their CSPs do not give them complete visibility into the cloud environment. When businesses opt for an IaaS or PaaS-based solutions from their CSP, these problem gets reduced significantly since the user can himself configure and manage the cloud environment.
- Reduced Control of Cloud Environment Settings
Besides reduced visibility, businesses often tend to face lesser control over their cloud computing environments when using the cloud. Similar to the visibility aspect, the settings can be enhanced more with the IaaS and PaaS-based solutions.
- Lateral Spreading of Attacks
Businesses also fear that if a cloud computing environment fails to have a robust defense controls, then it becomes easier for a cyber-attacker to spread the attack from one resource to another hosted on a cloud. This results in rapid lateral spreading & quick compromise across several databases and applications hosted on the cloud in breach-related events.
Best Practices in Cloud Cyber Security
Businesses should follow some of the best practices mentioned below for leveraging cloud computing in a secured way
- Having a Strong User Access Control/Least Privilege
Much like the traditional security software, the business admins must use strong user access control mechanisms for defining who all can and to what limit they have access to the data. Having restricted access will make sure that only authorized users have access to the data present in the cloud. Also, by implementing the least privilege model ensures that only the authorized users can access that data only that they require for completing their due tasks.
- Using SSH and Securely Store Keys
With the help of Secure Socket Shell (SSH) keys, one can establish secure server connections with private and public key pairs. As these keys are used for accessing sensitive data and perform critical tasks, it becomes compulsorily crucial for businesses to manage and securely store these SSH keys. Companies should implement policies related to cloud computing and ley management for monitoring how these keys will be created, managed, and removed when these keys reach their expiration.
- Using Encryption in Cloud
Having data encryption in the cloud assures businesses that their data that is moving in and out of the cloud remains encrypted and secured. When selecting a cloud service provider, companies must know their security needs when deploying cloud services. Today, most of the CSPs offer encryption services, and these encryption services, when combined with other security protocols, allow the businesses to comply with regulatory policies like PCI DSS and GDPR.
- Performing Routine Penetration Tests
Performing cloud penetration tests helps in identifying security vulnerabilities present in the cloud infrastructure. In the case of cloud computing, penetration testing often come as a shared responsibility, i.e., both- the business organization and cloud service provider can perform pen tests for determining vulnerabilities in the cloud.
- Using Multi-Factor Authentication
By using multi-factor authentication (MFA), it allows the companies to secure their data and its account data using several authentication methods like- OTP, biometrics, security questions, etc. When an MFA is used in a cloud computing setup, it helps in restricting access to the data present in the cloud only to the authorized users and averting risks of lost, stolen, or even compromised login credentials.
Concluding Remarks
Cloud computing comes with several benefits and challenges for its end-users. Maintaining cybersecurity in the cloud is a joint responsibility of the cloud service provider along as well as the end-user. Misuse or lack of knowledge about the cloud environment can have quite severe implications, so one should make sure that strong cloud computing security policies are implemented to make sure that data present in the cloud remains secure at all times.
- Considering Data Centers in India to Overcome Economic Conditions - May 10, 2022
- Determining Why Your Organization Needs Web Application Security - February 11, 2022
- How Does a Business Benefit with Managed Services - January 21, 2022
