Different Cloud Models That Defy Security Professionals
More and more companies migrate to the cloud computing model. For the most part, seek to generate savings for organizations. In part, too, are concerned to have more efficient processes.
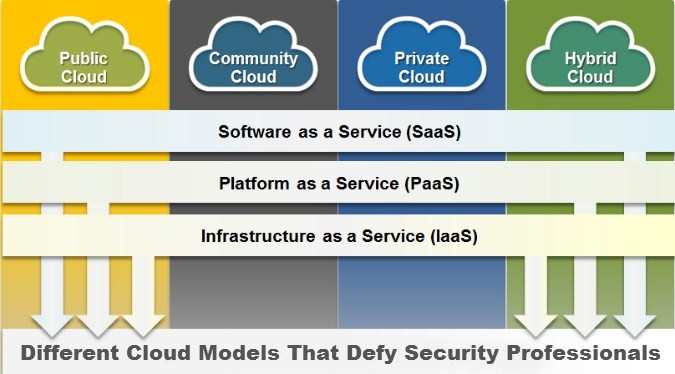
Just so, the different models of cloud, need to be evaluated carefully. When defining the cloud model to be adopted, the organization must be familiar with the differences and similarities between them, especially with regard to security aspect.
For example, the model SaaS (Software as a Service), designed to provide access to applications, groups and user policies which can only be used to ensure that certain users have access to selected information on organization’s CRM database.
In relation to the PaaS (Platform as a Service), whose main objective is data protection, is magnified when used in conjunction with virtual data storage, and in cases of unavailability of other cloud, it plans and calculate safety for balanced distribution of services for the platform at the time of any outages, and study of the appropriate encryption mode for account safety.
In the case of IaaS (Infrastructure as a Service) model, the CSO (Chief Security Officer) have to worry about arranging a corporate governance framework within which the transactions occur.
To assist CSOs to how to deal with different models, the following list enumerates challenges linked to each form of work in the cloud:
Challenge # 1:
Protect personal information before transmitting them to the cloud. There are many laws and many policies that prevent sensitive data which is transmitted to third-party systems – such as the cloud case. So the very cloud providers suggest that packages with sensitive information is sent in encrypted form or is removed. At that time, the question arises on how to perform encryption or deletion of data before sending them to the provider.
It is known that the encryption process is an operation that consumes valuable CPU resources. An alternative for this is to hire a broker to do the encryption of data between workstations and the provider. Optimize confidential data identification process at the time of shipment.
Challenge # 2:
No need to create hundreds of mirrors of sites in the cloud. There is no need to duplicate the data unnecessarily, large companies with thousands of employees all over the place have a dilemma that they need to create hundreds of mirrors of sites in the cloud.
The ability to allow access is based only on local platforms logins to ensure connection to the cloud-hosted services, eliminates this need. The problem increases when there are multiple credentials / passwords for each user. This situation generates significant costs and risks for companies and can thwart the organization. Just calculate the work involved in managing passwords for ten thousand different employees and anticipate that each of them forget the password at least once a year.
Enable single sign for local systems and the cloud platform can help you to mitigate associated risks and costs. After all, it is easier to remember just one password. It also generates less work for IT in time to stop a user from access – an operation will only make it impossible to login with such credentials in local platform and cloud.
Challenge # 3:
Conduct audits and take cloud platform with on-demand contracts (pay as the cloud platform is used) means to deliver financial executives a form of control of investments. This tool is usually provided by the provider itself, but in cases of external audits or disputes with service providers, it is worth keeping monitoring indoors.
To account monitoring, companies can hire an intermediary, as proposed in the matter of data encryption (above). The service should actively monitor the allocation of resources and aid organizations to stay within the rules and regulations of governance.
- How Cloud Computing Is Changing The Labor Market - March 25, 2015
- Adopting Infrastructure as a Service Can be a Good Deal - March 17, 2015
- Will Virtualize? Take These Six Points Into Consideration - March 12, 2015