From Risk to Resilience: Implementing Effective Privileged Access Management
One of the most effective places to exploit security breaches is through privileged accounts. Cyber insurance companies implement PAM solutions, as effective privileged access management is currently more crucial than ever. Risk management and security leaders should utilize this research to compare their efficiency.

Most passwords can be cracked in far less time than you might think with only a few dollars, some effort, and an intelligent brute-force guessing algorithm. In less than 60 minutes, 59% of the 193 million actual passwords were cracked, and in less than 60 seconds, 45% of them, according to a recent analysis.
Brute-force attacks are popular because they are so easy to use but are still not the best for password-cracking algorithms. Adding dates, names, dictionary words, and keyboard sequences to the guessing game mixture speeds up the process significantly since most passwords used daily share similar characteristics. For better implementation of PAM solutions, ESDS has given an overview of best practices for PAM implementation.
Importance of implementing a privileged access management solution
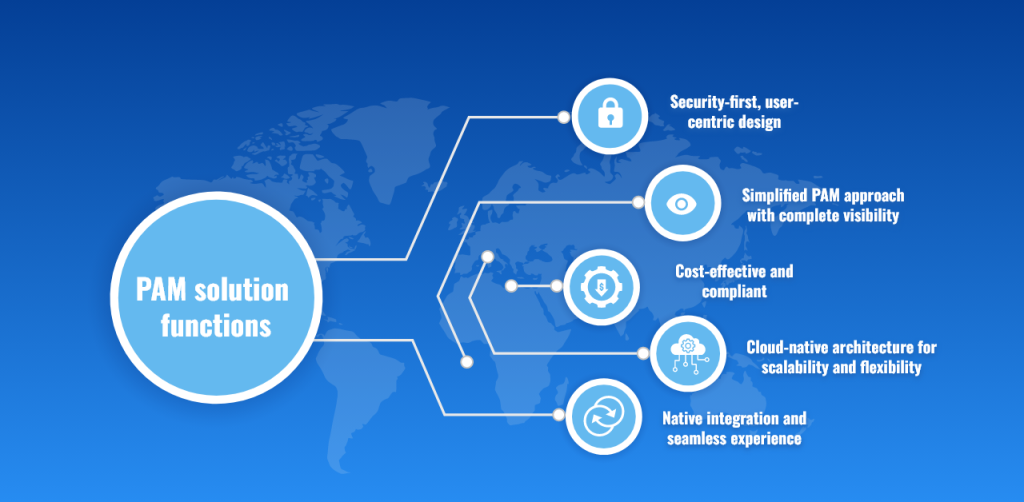
Security-first, user-centric design
Effective implementation of PAM protects important assets and ensures usability by combining robust security with a user-friendly interface. It offers access controls and privileged sessions to stop illegal access and data breaches.
Simplified PAM approach with complete visibility
ESDS provides a simplified PAM solution by eliminating unnecessary complications and infrastructure expenses. It helps with proactive threat identification and mitigation by offering complete visibility into privileged access activities.
Cost-effective and compliant
PAM is an affordable solution that helps businesses comply with legal requirements and compliance standards. It meets the criteria for cyber insurance by lowering the need for expensive infrastructure.
Cloud-native architecture for scalability and flexibility
The ESDS PAM solution’s cloud-native architecture provides scalability, flexibility, and simple cloud service integration. It facilitates secure, anytime, anywhere access to vital systems for remote employees.
Native integration and seamless experience
By integrating with access management applications, PAM improves security and simplifies management tasks. This integration increases overall operational efficiency.
How does privileged access management work?
A PAM solution defines the policies that apply to the individuals, procedures, and technology that need privileged access. Administrators should be able to automate creating, editing, and removing accounts, and your PAM solution must support the policies you set (such as multifactor authentication and automatic password management). Additionally, your PAM solution needs to constantly monitor sessions so you can provide reports that help you find and investigate anomalies.
The two main use cases in privileged access management are compliance and preventing credential theft.
When a threat actor obtains login credentials, they commit credential theft. Once signed in, they can access higher-level systems, install malware on multiple devices, and obtain organizational data. Effective implementation of the PAM solution can reduce this risk by ensuring just-in-time and just enough access and multifactor authentication for all admin identities and accounts.
For sensitive data, such as payment or health information, a least-privilege policy is probably necessary, regardless of the compliance regulations that apply to your company. You can also prove your compliance with a PAM solution by obtaining reports on privileged user activity, which includes who is accessing what information and why.
Additional use cases include:
- Recording and monitoring privileged accounts.
- Restricting access from third parties.
- Safeguarding remote access.
- Automating the user lifecycle.
One cybersecurity risk that can seriously and extensively harm an organization is the misuse of privileged access. Robust features in a PAM solution let you remain ahead of this risk.
- Give users instant access to vital resources; Enable safe remote access by substituting encrypted gateways for passwords.
- Keep an eye on private meetings to assist with investigative audits.
- Provide reports on privileged user access and activity;
- Analyze anomalous privileged activity that could harm your company.
- Record privileged account events for compliance audits and Secure DevOps with integrated password security.
ESDS PAM solution: a guardian against cyber-attacks
ESDS has introduced a Privileged Access Management (PAM) solution to improve the security of financial institutions, with a focus on privileged users. PAM secures privileged access in on-premises, cloud, and hybrid setups to defend against cyber-attacks.
A feature-rich privileged access security solution, ESDS PAM includes Endpoint Privilege Management, Application Password Management, Remote Access / Remote Session Management, Privileged Account Management, and Password Vaulting, all in one convenient package.
IT departments can use it to automate, safeguard, and securely store all highly privileged account passwords, keys, and identities. It lowers the risks associated with privileged access by allowing IT managers to centrally manage, audit, monitor, and record all access to vital IT assets.
ESDS PAM offers a strong barrier against potential breaches and unauthorized access, serving as a proactive defense against the more advanced cybercriminals. In addition to centralizing controls that support organizational security by preventing unwanted access attempts and potential data breaches, the solution provides detailed control and monitoring of access to privileged accounts.
ESDS can be set up on an on-premises server in only a few minutes or hosted on private cloud instances. Try it now.
- SaaS Is Transforming the Way Companies Scale - April 28, 2025
- Why no backup plans even after repeated global IT failures? - February 25, 2025
- Can BFSI community cloud solve data security challenges in banks? - February 3, 2025
