How Much Should You Spend on Cybersecurity?
Cybersecurity occasionally gets cut when businesses are searching for ways to save money. These services might not appear necessary to businesses that have been lucky enough to never experience a serious cybersecurity breach. Why should I pay for something I won’t use?
Once a breach occurs, the answer to this question is definitely known.
For startups or small- to medium-sized organizations in particular, data breaches can have potentially disastrous outcomes. 60 percent of small businesses fail within six months of suffering a data breach or cybercrime, according to Cybercrime Magazine.
Just last year, an IBM Security analyzed and indicated that the cost of data breaches has increased to a level not seen in 17 years, much alone the harm done to intangibles like client confidence. All too frequently, businesses that choose not to invest in cybersecurity nevertheless pay a steep price.
For businesses of all sizes, security has to be a top priority, but it can be challenging to know where to begin for smaller businesses. Making a budget for cybersecurity is a crucial first step, but there isn’t a straightforward method to choose the appropriate amount.
The good news is that cost-effective cybersecurity protection is available. And you may prevent the types of breaches that result in significant fines and lost revenue by taking practical precautions today to safeguard your business.
Setting Your Budget for Cybersecurity
How much do you value your data is the first step in determining how much to spend on cybersecurity. Then, question as to how much information an attacker could access if only one person’s credentials were stolen.
Compare the worth of your data to the expense of a data breach, which was $4.24 million as per IBM just two years ago. Given that the cost of recovering the data is not included, that estimate is probably conservative. In light of this viewpoint, security is frequently a “pay now or pay later situation”.
Let’s consider an example, where you want to cross the Indian Ocean, you can buy a plane ticket for a few thousand bucks. You could also kayak, but it simply wouldn’t be practical. Think of cybersecurity spending the same way— while putting security first may cost more money up front, it will ultimately result in time and money savings down the road.
Some businesses base their cybersecurity budget on a percentage of another budget. For instance, some people may opt to spend 10% of their IT budget. While this approach might work for some businesses, choosing a budget isn’t always just picking a percentage.
Look into your budget as its own data component, driven by how much you value your data and your overall security goals. One of the biggest errors businesses make when deciding on a security budget is considering the budget as the price to comply with regulations.
If you’re only spending what it takes to check the box, you’re not thinking about your customer. For product-based businesses, the consumer is everything, and spending money on security demonstrates your concern for the privacy and data of your clients. Compliance can offer you a perspective, but it’s not one size fits all.
The Models of Threat
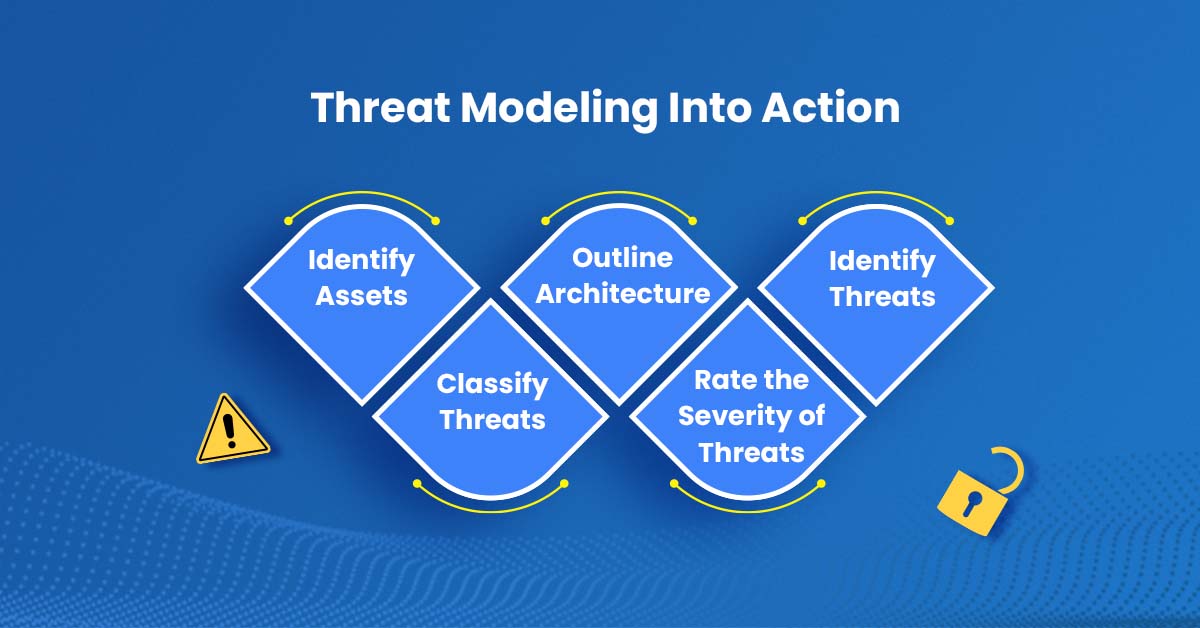
Any budget for cybersecurity must be driven primarily by threat modeling. An organization may identify, evaluate and mitigate possible threats to their network by using threat modeling. Assets, attack surfaces, and prospective attackers, including internal, external, and potential attackers, are all considered in a threat model. It arms businesses with a comprehensive view of potential risks, enabling them to prioritize threats as necessary, set security goals, and choose how to allocate their resources to achieve those goals. Without threat modeling, you’re spending without understanding why.
By removing any guesswork from the budget-planning process, the threat modeling process aids businesses in planning their budget around the most prevalent and pertinent threats to their particular industry and company size.
Communication of cybersecurity priorities to the C-suite and other stakeholders must also include threat modeling. Threat modeling is directly linked to the value of a company’s data, creating an opportunity to directly communicate on how each threat effects the threat models for your particular firm, even though it has been simpler to talk about cybersecurity since it is top of the news.
Essentially, businesses need to know the worth of their assets, the extent of their attack surfaces, the level of risk that they’re ready to take, and take into account variables like regulatory obligations and where they are in the security journey. Businesses should conduct a risk analysis to ascertain the extent of their assets.
What makes up a cybersecurity budget?
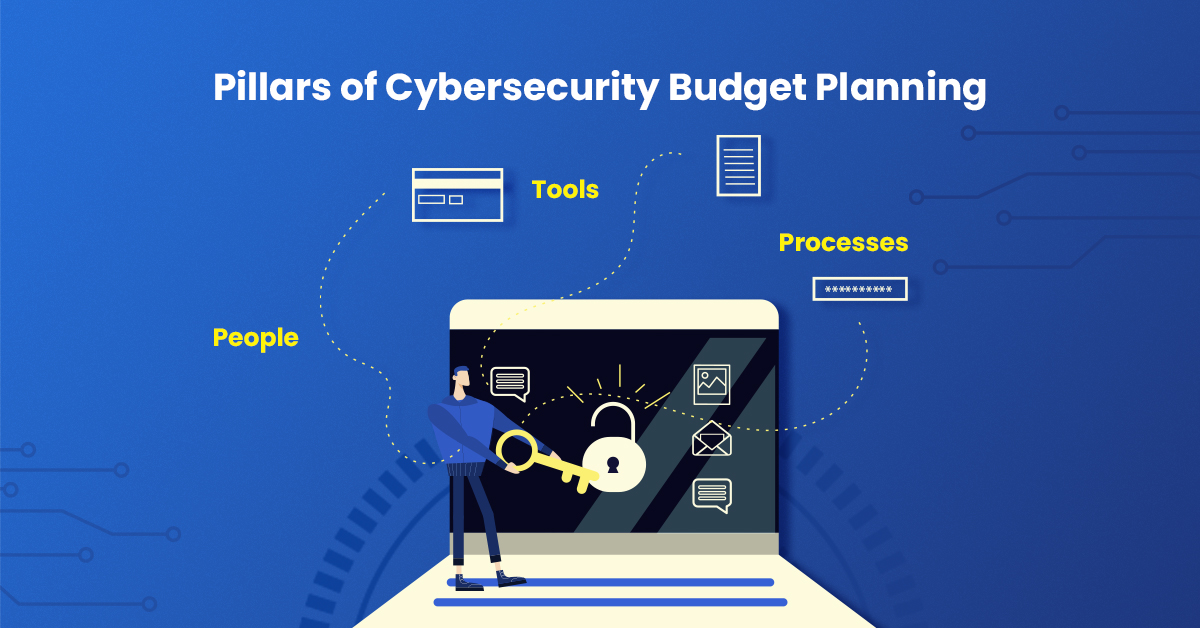
To emphasize, every cybersecurity budget should account for three essentials: people, processes, and tools. Let’s take a further look at what these essentials entail:
People
Companies should budget for at least one internal security hire. Companies can delegate everything related to security except accountability, thus having one person “own” the security is crucial. Outside expertise is also a part of the “people” component; it’s not cost effective to think you can have all the expertise in house, so you want to partner with security experts in a meaningful way.
Organizations may establish, maintain, and grow their cybersecurity strategies with the aid of security partners like ESDS.
Processes
The cost of security awareness training for the entire business is included in the budget for procedures. With compromised credentials being the leading cause of breaches, people in the organization should essentially participate in security culture, whether or not their role doesn’t involve handling private data.
Risk and vulnerability assessment are two additional process costs. Outsourcing these operations is a crucial step, much like outsourcing the human component of cybersecurity costs. It can be tempting for many firms to perform assessments on their own to save the expenses, but this lacks the objectivity necessary to produce reliable or insightful results.
Tools
Today, even hackers are automating their attacks, therefore businesses must automate their security procedures too. That’s where the automation tools can help. Even if it’s only automation for provisioning, it’s important to set aside some money for security tooling. Spending on tooling can make complicated security jobs simpler, especially for businesses operating in cloud settings. There are always extras to make life simpler, and when it comes to security, they might be well worth the cost.
Enabling Your Business Growth With ESDS’s SoC-as-a-Service

It is simpler to set a budget and decide how to spend resources for businesses with smoothly running oiled security teams and established security plans.
To determine a budget for startups and small to medium-sized organizations, you must be aware of your security goals and what you hope to accomplish with your security expenditures.
If you don’t know where to start, we’re here to help you figure it out.
When choosing SOC, ensure the SOC you choose is scalable for your company. At ESDS, we help you identify security flaws, detect advanced threats, and respond to them. Learn more about ESDS SOC-as-a-Service, by reaching out to us today. The holistic security solutions we provide answer your business’s safety concerns because your business deserves top-notch security!
Are you interested in learning more about creating a cybersecurity?
Call us right away.
- 6 Ways AI Reinvents the Security Landscape - January 9, 2024
- Top 6 Current Cybersecurity Trends For 2024 - January 9, 2024
- What Have We Learned from The Recent Cybersecurity Incidents? - January 3, 2024
