How to Perform a Cybersecurity Risk Assessment in your organization?
Using cybersecurity risk assessment, organizations may better identify, manage, and mitigate all types of cyber risk. It is an essential part of data protection and risk management strategies. If you work in information security, whether you like it or not, you are in the risk management sector. Risk assessments are nothing new. However, the digital risk threat landscape grows as businesses rely more on information technology and information systems to do business, exposing ecosystems to new, serious threats.

What Is Cyber Risk?
Cyber risk is the possibility of negatively disrupting sensitive information, money, or business activities online. Cyber risks are frequently associated with circumstances that could result in a data leak.
Security dangers can also relate to cyber concerns.
Examples of cyber risks include –
- Ransomware
- Data leaks
- Phishing
- Malware
- Insider threats
- Cyberattacks
You may take doable steps to lower your cybersecurity risk assessment risk. Although they are sometimes used synonymously, cyber hazards and vulnerabilities are distinct. A cyber risk is the likelihood that a vulnerability will be used to gain unauthorized access to a network. Exposure is a weakness that can be used to do this.
Cyber threats are divided into four categories: zero, low, medium, and high. The following three elements affect vulnerability assessments:
- What is the danger?
- How susceptible is the architecture?
- What would happen if the security were to be?
- Compromised or the service rendered unavailable?
Consider evaluating the danger of a cyberattack compromising a specific operating system. Your danger is more significant if your office needs physical security. Your vulnerability is modest if you have competent IT employees who can spot holes and upgrade the operating system.
Very few items pose no risk to an information system or business process, and risk entails uncertainty. It’s not a risk if it is assumed to occur. It is a component of everyday business activities.
What Is a Cyber Security Risk Assessment?
Cybersecurity risk assessments are used to scrutinize, evaluate, and prioritize risks to people, assets, and other organizations, the nation, and organizational operations coming from the usage and operation of information systems.
A cybersecurity risk assessment’s main objective is to inform stakeholders and promote appropriate actions for hazards that have been identified. In order to help executives and directors make informed security decisions, they also provide an executive summary.
The following inquiries are addressed by the information security risk assessment process:
- What are the most critical information technology resources for our company?
- Which data breach, whether caused by malware, a cyberattack, or human error, would significantly impact our business?
- Consider client data.
- Can every source of a possible threat be located?
- What potential degree of severity does each threat that has been identified have?
- What are the interior and exterior weaknesses?
- What if those were shortcomings exploited against us?
- What are the odds of getting taken advantage of?
- What flaws in the company’s security, online threats, or attacks could endanger its ability to operate?
- How much risk is considered acceptable by my organization?
- If you can answer those questions, you can choose what to safeguard. This implies you can create data security plans and IT security controls for risk mitigation.
- Nevertheless, before you can accomplish that, you must respond to the following queries:
- What kind of risk are you reducing?
- Is this the security concern that requires the most attention?
- Am I reducing the risk in the most practical way?
Why Perform a Cybersecurity Risk Assessment?
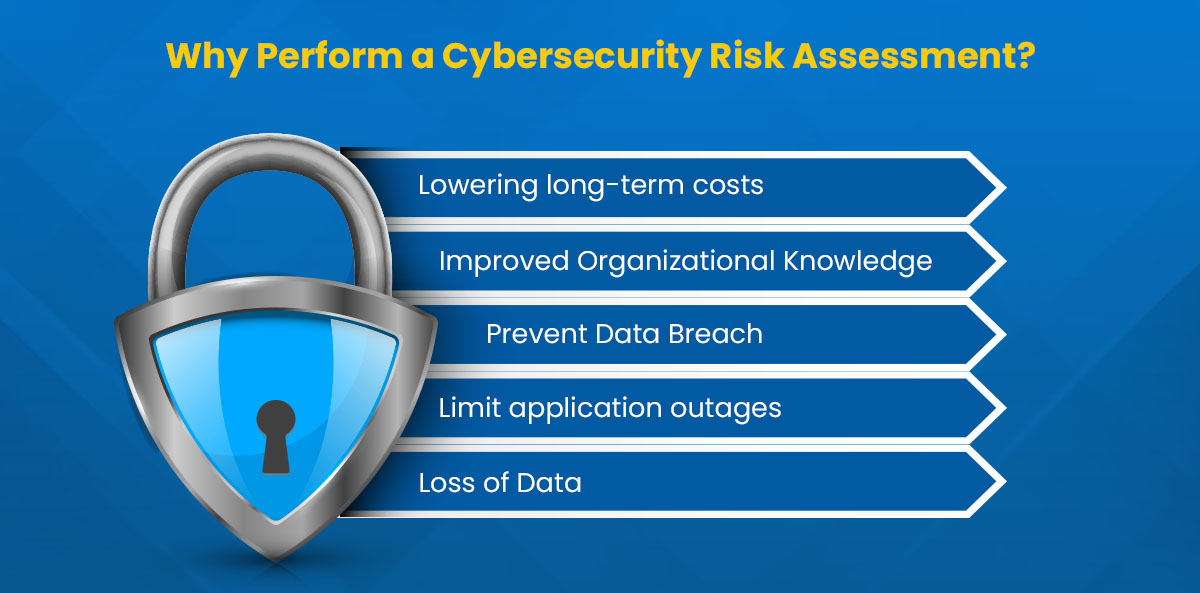
You should conduct a cybersecurity risk assessment for several reasons, as well as for a few others. Let’s go over each one:
Lowering long-term costs
In the long run, preventing or reducing security events can save your business money and reputational damage by identifying risks and vulnerabilities and mitigating them. Provides a template for the future of cybersecurity risk assessment. Solid first turn will enable repeatable procedures even with workforce turnover. Cybersecurity risk assessments are one process that needs constant updating.
Improved Organizational Knowledge
Understanding your organization’s weaknesses helps you identify areas for improvement.
Prevent Data Breach
Any firm could suffer severely from a data breach in terms of finances and reputation.
Limit application outages
For employees and customers to perform their duties, internal or customer-facing systems must be accessible and functional.
Loss of Data
You can lose business to rivals if trade secrets, software, or other crucial information assets are stolen.
Cybersecurity risk assessment analyses are also essential to information risk management and any organization’s overall risk management plan.
How to Perform a Cybersecurity Risk Assessment?
Following a high-level overview, the following sections will go into greater detail about each phase. You must be aware of the data you have, the infrastructure you use, and the importance of the data you are attempting to safeguard before you can begin risk assessment and mitigation.
Starting with an examination of your data to provide answers to the following inquiries
- How do we gather data?
- How and where are these data being stored?
- How can we safeguard the data and record it?
- How long are the data stored?
- Who has access to the data both internally and externally?
- Is the location where the data is being stored appropriately secured?
How to determine cyber risk assessment:
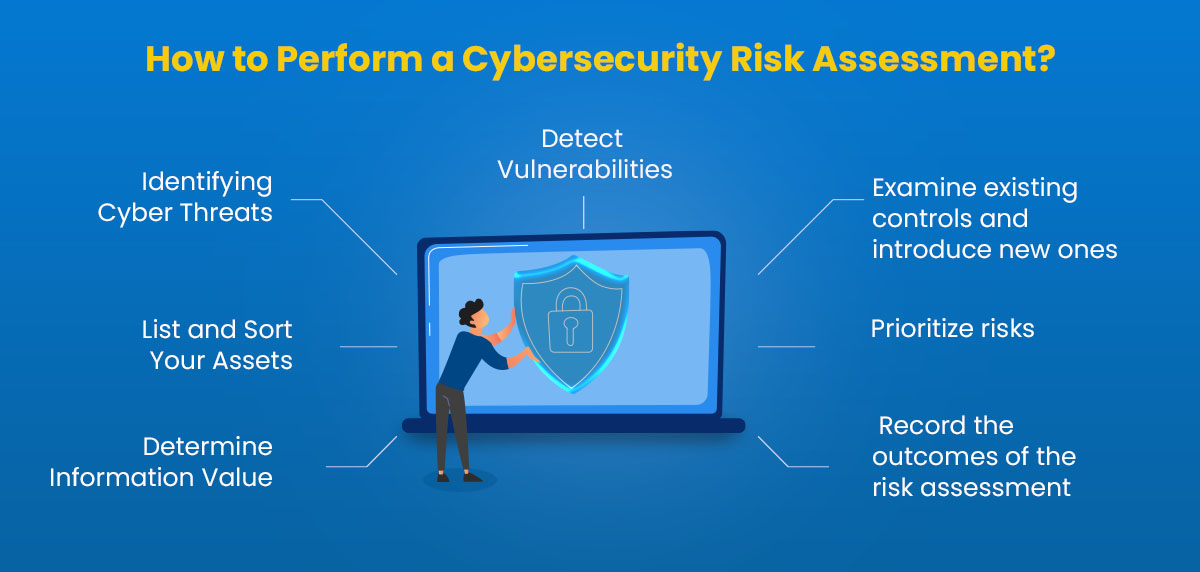
Determine Information Value in Step 1
It is best to focus your scope on the business’s most critical assets because most firms have a limited budget for information risk management.
Spend some time creating criteria for assessing the value of an asset to avoid wasting time and money later. Organizations typically consider asset value, legal standing, and business importance. Use the standard to categorize each purchase as critical, principal, or minor when adequately incorporated into the company’s information risk management policy.
Step 2: List and Sort Your Assets
Finding assets to evaluate and deciding on the assessment’s parameters come first. This will help you determine which assets to assess first. You might not wish to evaluate every office space, worker, piece of electronic data, trade secret, car, and piece of office equipment. Keep in mind that not every asset has the same worth.
Identifying Cyber Threats in Step 3
A cyber threat is any weakness that could be used to compromise security, hurt your firm, or steal its data. In addition to the obvious risks like malware, hackers, and other IT security concerns like system failure, human error, and hostile attacks, there are other dangers.
Detect Vulnerabilities in Step 4
It’s time to switch from what might happen to what is likely to happen. A vulnerability is a flaw that a threat can use to compromise security, hurt your business, or steal confidential information. Some techniques used to detect vulnerabilities include vendor data, incident response teams, the vulnerability database maintained by the National Institute for Standards and Technology (NIST), and software security analysis.
Step 5: Examine existing controls and introduce new ones
Examine the safeguards in place to reduce or do away with the possibility of a threat or vulnerability. Technical controls include hardware, software, encryption, intrusion detection systems, two-factor authentication, automatic upgrades, and continuous data leak detection. Nontechnical controls include security rules and physical access methods like locks and keycards.
Prioritize risks in Step 6 based on the value of information vs. the cost of prevention.
Determine senior management’s or other responsible individuals’ responsibilities for mitigating the risk using the amount of risk as a guide.
The following are some general principles:
High-immediate development of corrective actions is required.
Medium: Adequate measures were created in a timely manner.
Low – choose to accept or reduce the danger.
Step 7: Record the outcomes of the risk assessment reports.
The last step is to create a report on the risk assessment to aid management in making decisions about the budget, policies, and processes. The report should outline the risk, vulnerabilities, and values associated with each threat, including the effect, likelihood of occurrence, and suggestions for control.
Threats to Your Organization: Identify Them
Cybersecurity risk assessment is a crucial process that organizations must undertake to identify and mitigate potential cyber threats. It involves a comprehensive analysis of an organization’s IT infrastructure, including hardware, software, and network systems, to identify vulnerabilities that could be exploited by cybercriminals.
ESDS’ comprehensive security services identify vulnerabilities, prioritize risks, and implement necessary controls to safeguard your business assets and protect your business against cyber threats.
- Why does your business need Endpoint Detection and Response (EDR)? - May 15, 2024
- Are your business endpoints completely secure? - March 26, 2024
- Is Colocation key to transforming your data center management strategy? - March 22, 2024
