Incident Management: Your way to swift incident response and recovery

In today’s interconnected digital landscape, businesses face an ever-increasing number of cyber threats and incidents that can disrupt operations, compromise sensitive data, and damage reputation. Having a robust incident management process in place is crucial to ensure swift incident response and effective recovery. In this blog, we will explore the importance of incident management and discuss key strategies for implementing a successful incident management framework.
What is Incident Management?
Real-time monitoring, management, recording, and analysis of security threats or occurrences is known as security incident management. It aims to provide a strong and thorough overview of any security issues that may exist inside an IT system. An active threat, an attempted incursion, a successful compromise, or a data leak are all examples of security incidents. Security events include breaking rules and gaining unauthorized access to information like social security numbers, financial information, health information, and other personally identifiable information.
What makes Incident Management important?
Cybercriminals frequently assault businesses, often causing permanent harm.
We currently live in volatile, rapidly evolving times. The digitalization of the globe is advancing. Particularly in 2020, when an increasing number of people shifted their place of business to a home office, we saw this quite clearly. They transitioned from an IT-managed network to an office without corporate firewalls and perhaps without professional antivirus software to keep them safe. Businesses become easy targets for fraudsters in this position, which presents significant difficulties for IT teams.
How does your business manage an incident?
The Incident Management Process –
To make sure the IT environment is indeed secure, a multifaceted security incident management strategy needs to be put into place. Five steps are listed for security incident management, including:
- Prepare to handle occurrences.
- Monitor for potential security incidents and report any that occur.
- Assessing identified occurrences can help you decide what steps to do next to reduce the risk.
- Contain the event, look into it, and then resolve it
- Discover and record the most important lessons from each experience.
Best Practices for Incident Management
- Create a security incident management strategy and guiding policies that provide direction on how issues are found, reported, evaluated, and handled. Prepare a checklist of procedures based on the hazard. Update security incident management protocols as needed, especially given knowledge gained from past occurrences.
- Create an incident response team (also known as a CSIRT) with roles and tasks that are well-defined. Your incident response team should have representatives from the IT/security department as well as the legal, communications, finance, and business management or operations departments.
- Create a thorough training programme that covers all the aspects of the security incident management procedures. Use test scenarios to regularly put your security incident management plan through its paces and make necessary adjustments.
- Perform a post-event analysis after any security occurrence to learn from your successes and mistakes and, as necessary, make changes to your security programme and incident management procedure.
However, every employee has a responsibility to ensure IT security, so it is not just a worry of security experts.
What is your business’ incident recovery plan?
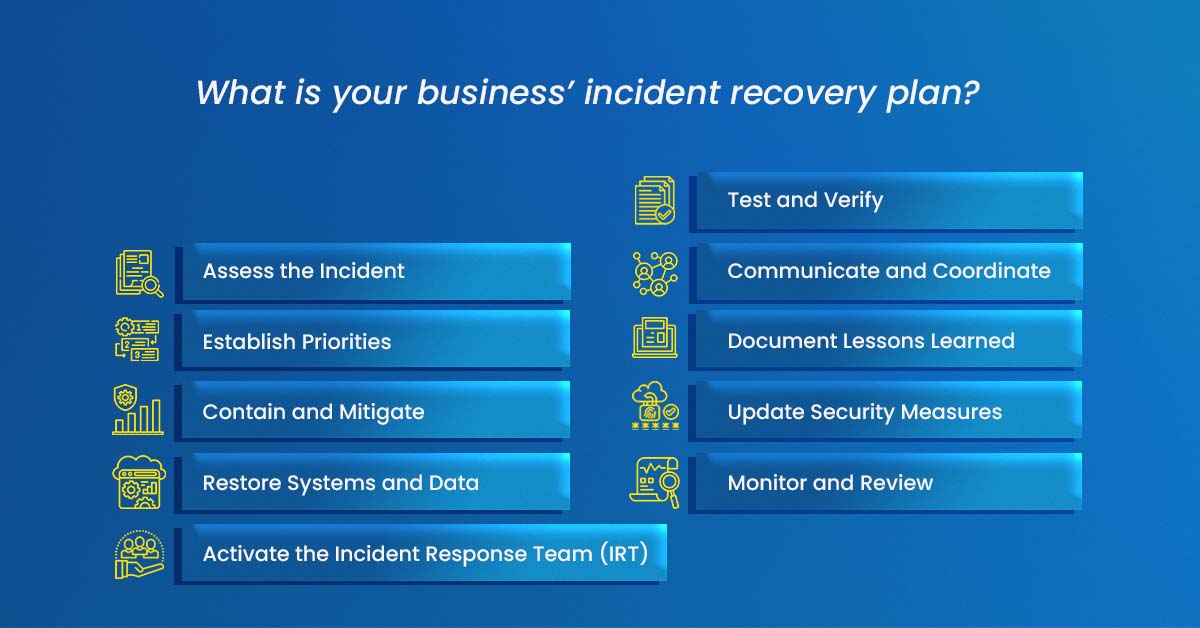
- Activate the Incident Response Team (IRT):
- Notify and assemble the designated incident response team members.
- Designate a team leader who will oversee the recovery process.
2. Assess the Incident:
- Gather all available information about the incident, including its nature, scope, and impact.
- Determine the affected systems, data, and any potential vulnerabilities or weaknesses that contributed to the incident.
3. Establish Priorities:
- Identify critical systems, applications, and data that need immediate attention for restoration.
- Define the order in which systems and services should be recovered based on their importance to business operations.
4. Contain and Mitigate:
- Isolate affected systems or networks to prevent the further spread of the incident.
- Apply necessary patches, updates, or security controls to address vulnerabilities or mitigate risks.
5. Restore Systems and Data:
- Use backup systems or redundant infrastructure to restore affected systems and services.
- Validate the integrity and functionality of restored systems before reconnecting them to the production environment.
6. Test and Verify:
- Conduct thorough testing to ensure the recovered systems are functioning correctly.
- Validate the effectiveness of security controls and patches applied during the recovery process.
7. Communicate and Coordinate:
- Maintain regular communication with key stakeholders, including internal teams, executives, customers, and regulatory bodies.
- Provide timely updates on the incident recovery progress, expected timelines, and any temporary measures in place.
8. Document Lessons Learned:
- Conduct a post-incident analysis to identify the root cause of the incident.
- Document lessons learned, including areas for improvement in incident response, security controls, or system resilience.
9. Update Security Measures:
- Implement necessary enhancements to security controls, policies, and procedures based on the incident findings.
- Train employees on any changes or improvements in security practices.
10. Monitor and Review:
- Continuously monitor systems and networks for any signs of recurring or new incidents.
- Conduct regular reviews of the incident recovery plan and update it based on lessons learned and changes in the threat landscape.
Conclusion –
At ESDS, we understand the critical importance of incident management and recovery in today’s digital landscape. We believe that a proactive and well-defined incident recovery plan is essential to minimize the impact of cyber incidents and swiftly restore normal operations. Our expertise in incident response and comprehensive solutions empower organizations to effectively navigate through incidents and emerge stronger.
Our security experts prioritize incident management and recovery to ensure the safety and resilience of your digital assets. Our dedicated team of experts, advanced technologies, and proven methodologies stand ready to swiftly respond to incidents, minimize the impact, and restore normal operations. Trust ESDS as your partner in incident recovery and together, we’ll navigate the challenges of cybersecurity, protecting your business and enabling its continued growth.
- Why does your business need Endpoint Detection and Response (EDR)? - May 15, 2024
- Are your business endpoints completely secure? - March 26, 2024
- Is Colocation key to transforming your data center management strategy? - March 22, 2024
