Make Your Endpoint Security A Reality
In the initial days of the internet, when companies newly started using computing technologies, the local network had a very rigid perimeter. Servers and repositories were physically present in the same office. Today, due to a massive shift to cloud hosting, SaaS, and the ongoing pandemic, the situation has turned 180 degrees. The organizational workforce, partners, and vendors are connected to enterprise networks remotely from their devices.

These remotely connected personal devices pose a cybersecurity risk that malicious attackers can take advantage of to rob corporate data. According to research by Check Point, throughout 2021, the weekly average of ransomware attacks focused on company networks expanded by 50% in comparison to 2020. It is now critical for businesses to deploy robust endpoint security solutions that protect their data stored across endpoints.
What Is Endpoint Security?
Endpoint security is the method of protecting endpoint devices such as desktops, laptops, mobile phones, and tablets from cyberattacks. These endpoints are the gate to access the organization’s network which can then be used by malicious attackers for cyberattacks.
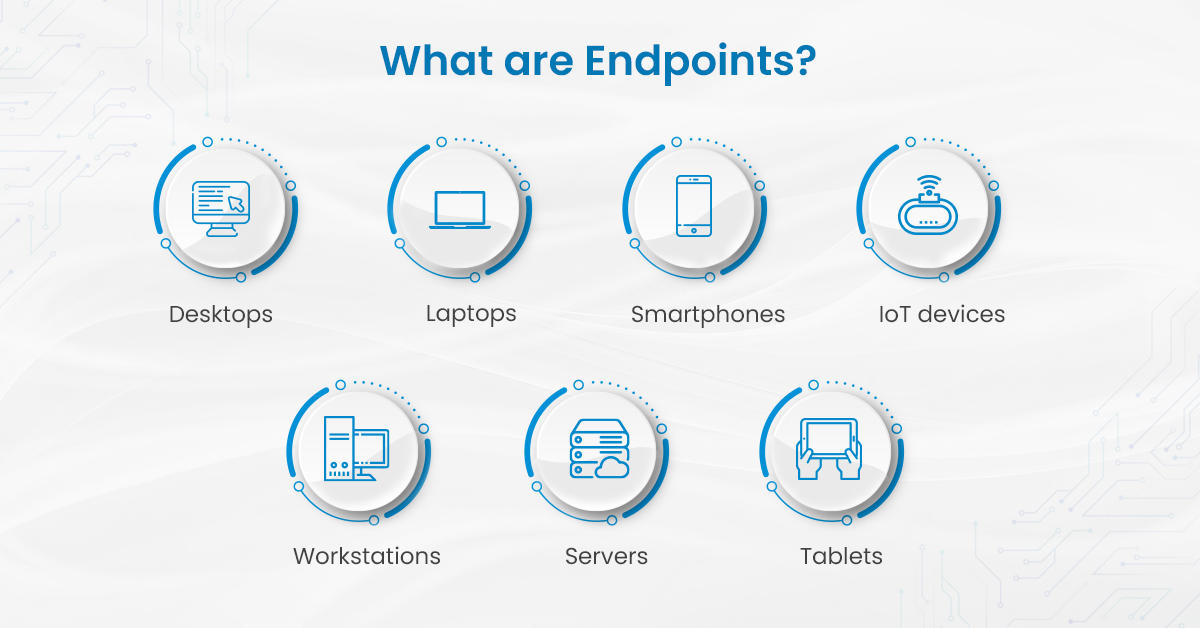
Endpoint security solutions help businesses to protect these endpoints or end-user devices connected to the organization’s networks or cloud from cyber threats. No matter how many new end-users are added to a company’s network, endpoint security ensures that it is secure at all times from any cyberattack.
Why Endpoint Security is important for businesses?
In this digital era, data is the most crucial asset for any organization. The malicious attackers know this, therefore, are always active to exploit the loopholes in an organization’s security. In the past, as the workforce was not remotely working, and cyberattacks weren’t frequent, centralized network protection was enough. However, due to many endpoints in today’s organization’s network, which only tend to grow, security parameters that have new layers of security to combat rising cyberattacks are essential. As per a study by the Ponemon Institute; the average cost of endpoint attacks has accelerated from an average of $7. 1 million to $8.94 million. Furthermore, 68% of the respondents registered that the frequency of attacks against endpoints has increased over the last year.
This is when endpoint security becomes of paramount importance that can analyze, detect, then block and contain cyber-attacks as they happen. Moreover, organizations also need technologies and security expertise that can anticipate threats and block them before happening.
How does Endpoint Security work?
To find the most workable endpoint security solution for your business, it is vital to know how endpoint security works and acts together with other security components. Here is how primarily endpoint security works, irrespective of the industry type
1. The first step is to study a company’s network thoroughly, to understand the number of endpoints and the vulnerabilities in the existing network. An analysis also needs to be done for Identity and Access Management (IAM) to clearly define who has access to which resource. Endpoint security analyses all the files that enter the organizations’ network and compares them against the threat information database stored in the cloud.
2. The second step is to arrange and sort all the endpoints on the network and choose a security solution for each layer depending on the technology. The security solution layers are based on components such as hardware, software, cloud, and network being used. However, certain endpoint security solutions providers cover your full range of needs.
3. The third step is about implementing the chosen solution and focusing on the network monitoring mode. A clear understanding of how each security layer is performing is needed to find the vulnerability in the network. If any vulnerability is detected, the entire process needs to be repeated.
What are the benefits of Endpoint Security?
All the home and personal devices such as desktops, laptops, tablets, and smartphones are prone to attacks from cybercriminals every minute of the day. Having an endpoint security solution can be beneficial in several ways to stop cyberattacks like a pro. The benefits of endpoint security include
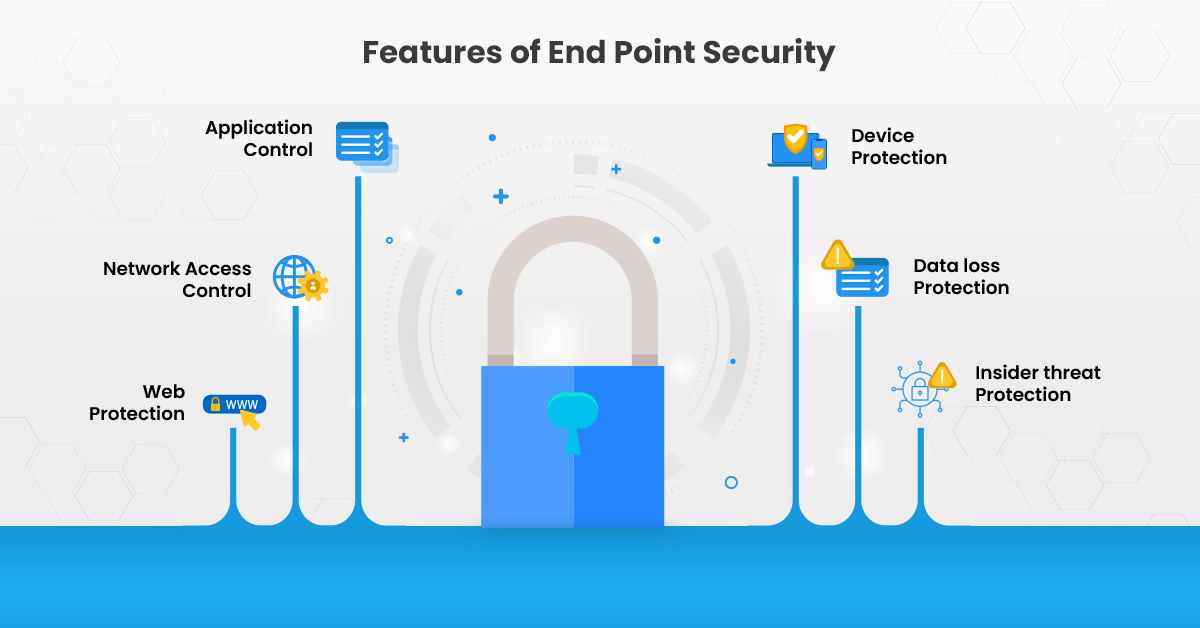
- Endpoint Device Protection
Endpoint Security Solutions and Software protects your corporate devices from malware like ransomware and Trojans, malicious applications, and investigate security incidents and alerts.
- Threat Detection
Endpoint security solution detects the threat in an organization’s network. Therefore, in case of unusual activity in the network, it notifies or sends alerts that prevent cyberattacks from happening.
- Cost-effectiveness
Cyber attackers target your money-making assets that include data, intellectual property, trades secrets. Protecting them ensures no financial loss. Also, deploying endpoint security solutions means you do not have to pay for manual data retrieval and troubleshooting that saves cost.
- Compliance
Industries such as Finance, Research organizations require compliance with data security regulations that demand endpoint security solutions.
How Endpoint Security is different from the firewall?
A firewall monitors incoming and outgoing traffic in a network to either allow or deny access. Whereas, Endpoint security protects the data on the endpoint device itself by monitoring the employees’ devices. A firewall is ideal in a situation when employees are not working remotely and are using a central network.
Endpoint Security and Antivirus: What’s the difference?
Endpoint security solutions are installed in the network to protect every endpoint device connected to it. It acts as a security solution for the entire organization. Antivirus is one part of endpoint security solution, that needs to be installed on individual devices to protect them from various malware activities. Antivirus periodically scans devices to locate an unusual pattern that matches a database of viruses and simply removes it.
Antivirus is adequate only if an organization is small with no central network architecture. An endpoint security solution is a must in the case of several workstations, connected machines, and increasing devices to its network.
Conclusion
The skyrocketing increase in cyberattacks and more employees working remotely through their devices and smartphones demand an effective endpoint security solution. Our expert team at ESDS can help organizations secure their network, eliminate the risk of cyberattacks and malicious attacks on their confidential business data. From mobile devices and tablets to laptops, ESDS is well-versed in securing all your endpoints through multi-layered security solutions.
Connect with ESDS to discover can how you can take control of all your devices with an endpoint security solution.
- Top 5 Data Center Trends for 2024 - October 11, 2023
- Top 15 Cloud Computing Trends 2024 - October 4, 2023
- What is Infrastructure Monitoring and Why Infrastructure Monitoring Tool is Important for Your Business? - September 20, 2023
