Safety of Public and Private Cloud Services
 According to studies, revenue in the area of “cloud computing” technologies in 2013 will amount to 150 billion dollars. Many businesses have already implemented the transfer of corporate data in the cloud, many more companies are going to do it soon, but a lot of people are worried about the security of data stored in the cloud. Of course, no one can guarantee absolute security in any computing environment, however, the transition to “cloud” technology can take certain measures to help in reducing the risk of data loss to a minimum. For example, when choosing cloud providers, it is important to look not only at firms’ pricing power, but also implemented its security protocols. It is important to understand that the transition to “cloud” technologies may be safer than the standard internal solutions as the industry has invested billions of dollars in information security.
According to studies, revenue in the area of “cloud computing” technologies in 2013 will amount to 150 billion dollars. Many businesses have already implemented the transfer of corporate data in the cloud, many more companies are going to do it soon, but a lot of people are worried about the security of data stored in the cloud. Of course, no one can guarantee absolute security in any computing environment, however, the transition to “cloud” technology can take certain measures to help in reducing the risk of data loss to a minimum. For example, when choosing cloud providers, it is important to look not only at firms’ pricing power, but also implemented its security protocols. It is important to understand that the transition to “cloud” technologies may be safer than the standard internal solutions as the industry has invested billions of dollars in information security.
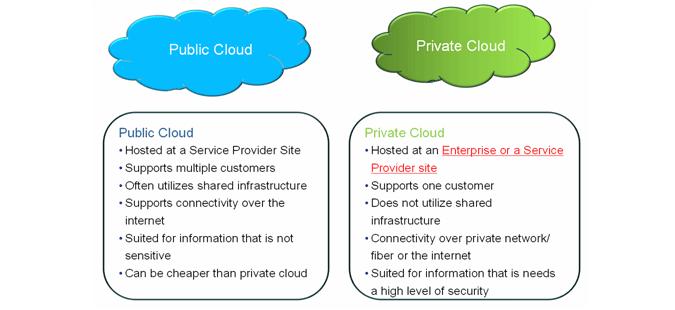
In public, the cloud system end-user has a high level of automation. Customers can place their applications in the cloud and manage all the user settings of your services. Public “cloud” has no such visibility as a private cloud has. If you are using a public “clouds” you give the placement of computing resources in to control. In particular the “cloud” resources are used by fewer people and they have a higher level of management. Depending on these differences to safety management in these environments, specific practices.
The first and most important step is the installation procedure of authorization. For the selection of the password, it requires randomization procedure and the need for strict adherence to protocols that create passwords for all staff. It’s amazing, but many people still use words like “password” or a combination of digits “12345” as a password to access key data sources. Application of the standard LDAP and administrator credentials you can really protect your information.
Having dealt with the internal procedures of authorization, you should pay close attention to outsourcing partners. Whether they are holding your security protocols and perform background checks, whether they are complying with any other measures that protect and control the transmission of information. Information sharing is crucial, especially in the case of public computing environments. Providers must use the best encryption tools to keep your information safe and in usable condition. They must also provide administration services to the highest level, including installing firewalls and advanced detection of network attacks.
Legal aspects of data storage in the cloud hosting
There are many legal problems connected with the storage of information, especially data identifying a person. Despite the fact that information is in the cloud, it is still somewhere to be placed and there are rules that govern its movement. In some countries, such as India, imposed very strict requirements for safety information, which limit the storage and movement of information. Choose a provider who is knowledgeable about these rules, and could, if necessary, too quickly move your information to comply with these requirements. According to a study, more than forty states have official regulations governing the methods of protection of personal data (PII). Should give preference to well-known providers of cloud services, which have systemic means of controlling the movement of PII under its “cloud” network.
Many cloud providers enter the market, not having sufficient experience in the field of human resources policies and technologies. That is why in order to obtain a comprehensive understanding of the work of a company, should ask more than a dozen issues. One of the most important – the question of who will have the right to access and transfer your information. Whether they will notify you about any breach of security, or just hide them.
Does this outsourcing company allow you to optionally create an emergency data center for disaster?
The contract may provide higher levels of encryption standards for data storage. In addition to this “cloud” provider should be familiar with the work of any other suitable provider of SaaS and its technologies. Your business depends on many different outsourcing companies, one way or another address with your information, so it is important that the information management system have no weak links.
Outsourcing companies need to adhere to certain standards, assigning passwords that reduce the likelihood of hacking. In the case of multiplayer “cloud” above average risk, and therefore cloud providers must show that they use management tools that provide separation to reduce the risks.
Conclusion
Achieving a high level of safety in public and private “clouds” requires confidentiality requirements and user access. New solutions for information storage and management come to market fairly quickly, and as these tools are introduced, users will get additional protection for their information.
- How Cloud Computing Is Changing The Labor Market - March 25, 2015
- Adopting Infrastructure as a Service Can be a Good Deal - March 17, 2015
- Will Virtualize? Take These Six Points Into Consideration - March 12, 2015