Security Operations Center (SOC) Services: A Measured Approach to Digital Threat Management

In today’s IT environments, the demand for structured cybersecurity solutions continues to grow. At the heart of this demand lies the Security Operations Center (SOC)—a centralized function designed to improve visibility, incident response, and continuous monitoring across IT assets. For enterprises dealing with large-scale data and critical operations, Security Operations Center (SOC) Services have become a core necessity rather than a peripheral function.
The SOC center is tasked with one primary goal: detecting, analyzing, and responding to cybersecurity incidents using a combination of technology, processes, and people. In some business models, this setup is fully internal. However, many organizations now choose to adopt managed SOC services or SOC as a service to manage costs, streamline operations, and maintain round-the-clock vigilance.
Understanding the SOC Security Operations Center Model
The SOC Security Operations Center operates as a centralized unit that houses security analysts, threat hunters, and incident responders. These professionals work with tools like SIEM (Security Information and Event Management), threat intelligence platforms, and endpoint detection and response systems to analyze anomalies and manage risks in real-time.
A security operations center may be configured to offer various levels of engagement — from basic monitoring and alerting to full-scale incident response and post-event analysis. The operating model depends on the organization’s internal capabilities and regulatory requirements. For instance, financial services, healthcare providers, and public sector entities often need customized SOC architectures with specific compliance layers.
SOC as a Service: Extending Capabilities Without Infrastructure Overload
For companies that want to deploy a SOC without building one from scratch, Security Operations Center as a Service presents a viable pathway. SOC as a service is essentially an outsourced model where a third-party provider manages the full scope of SOC functions. This setup eliminates the need for in-house teams to configure, manage, and upgrade complex security stacks.
With SOC as a Service, clients get access to:
- Real-time threat detection and response
- Compliance reporting
- 24x7x365 monitoring
- Access to security experts and automated remediation protocols
Organizations operating in high-risk sectors often find managed SOC services helpful in aligning their cybersecurity practices with regulatory and operational benchmarks.
How a SOC Center Operates in a Managed Service Environment
A SOC center delivered through a managed service model typically consists of the following components:
- Monitoring and Alerting—Collecting logs and telemetry data from endpoints, firewalls, and servers to monitor unusual activity.
- Correlation and Analysis—Using machine logic and analyst expertise to identify patterns indicative of a potential threat.
- Incident Handling—Classifying alerts, prioritizing incidents, and activating response protocols.
- Post-Incident Review—Root cause analysis and reporting to enhance future defense mechanisms.
The advantage of managed SOC services lies in their ability to deliver consistent security outcomes while maintaining operational agility. Because these services are centrally managed, they help reduce fragmentation in security implementation across hybrid IT landscapes.
Aligning SOC Services with Compliance and Reporting Needs
In regulated industries, where data sovereignty and governance frameworks are tightly defined, the role of the Security Operations Center is more than just operational—it is strategic. Audit trails, log management, and compliance checks become embedded into SOC workflows, enabling teams to meet requirements such as ISO/IEC 27001, PCI-DSS, or local data protection laws.
Organizations may integrate their SOC center with governance tools to ensure traceability and data integrity. This is particularly relevant for cloud-native enterprises and those working with sensitive customer information.
Integrating SOC into Existing IT Environments
One challenge that often comes up is integration. A SOC Security Operations Center needs to ingest telemetry from a variety of sources—cloud environments, on-prem systems, SaaS platforms, and more. This requires an architecture that is both scalable and vendor-agnostic.
Security Operations Center (SOC) services are built to support this kind of heterogeneity. Whether the deployment is in-house or via SOC as a Service, the objective is to provide coverage across the entire digital infrastructure. Providers offering managed SOC services typically support integrations with most commercial and open-source toolchains.
Moreover, continuous tuning of alert thresholds, correlation rules, and playbooks ensures that the SOC center remains aligned with the evolving threats. This level of adaptability is critical in avoiding alert fatigue and focusing analyst effort on credible threats.
SOC as a Value Enabler
While traditionally seen as a cost center, the modern Security Operations Center is increasingly viewed as a risk mitigation tool that enables continuity and resilience. In sectors where downtime can lead to regulatory violations or revenue loss, the presence of a mature SOC center supports business continuity objectives.
SOC as a service offerings often include value-added features like behavioral analytics, insider threat detection, and threat intelligence feeds, providing a more holistic approach to enterprise security. These features support strategic decision-making and improve the organization’s ability to maintain operational stability.
Key Considerations while Evaluating a SOC Partner
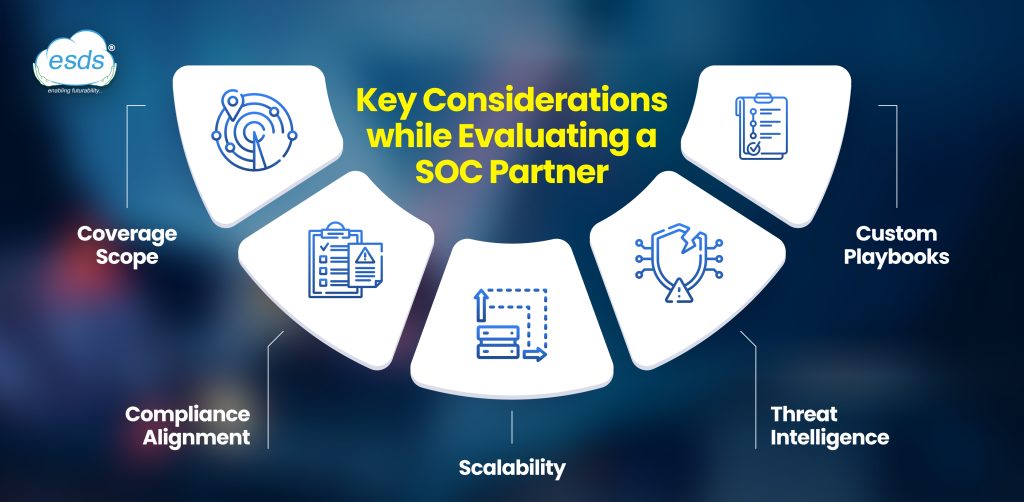
When choosing a managed SOC services provider, several evaluation points should be considered:
- Coverage Scope: Does the service cover cloud, on-prem, and hybrid infrastructure?
- Compliance Alignment: Can the SOC model meet internal audit and external compliance requirements?
- Custom Playbooks: Does the provider allow customization of response workflows?
- Threat Intelligence: Is there integration with real-time threat feeds?
- Scalability: Can the service scale with organizational growth or shifts in business models?
Understanding these parameters ensures that the selected Security Operations Center as a Service partner aligns with current and future security needs.
Conclusion
Security Operations Center (SOC) services continue to be a foundational element in enterprise cybersecurity. Whether deployed as an internal function or via SOC as a service, the SOC model offers a structured approach to risk mitigation, incident response, and infrastructure monitoring.
In an environment where threats evolve rapidly and compliance requirements grow stricter, having a dependable SOC center becomes crucial to maintaining operational control. Organizations that invest in the right mix of people, processes, and platforms through managed SOC services position themselves to maintain consistent oversight of their digital assets.
- Security Operations Center (SOC) Services: A Measured Approach to Digital Threat Management - April 11, 2025
- The Impact of AI on Colocation Services - February 13, 2025
- Colocation Data Centers the Backbone of Modern Business Data Management - November 12, 2024
