The Importance of Cybersecurity for Your Operational Technology Environment and How to Improve It

Operational technology (OT) plays a crucial role in many industries, from manufacturing and energy to transportation and healthcare. OT systems are used to control and monitor critical infrastructure, including power plants, oil rigs, transportation networks, and medical devices. As our reliance on these systems grows, so does the need to protect them from cyber threats. Cyber-attacks targeting OT environments can cause severe disruptions, including equipment failure, production downtime, and safety incidents. This blog will explore the importance of cybersecurity for your OT environment and provide actionable steps to improve its security posture. By implementing these best practices, you can safeguard your critical infrastructure from cyber threats and ensure its availability, integrity, and confidentiality.
Types of cyber threats facing OT environments:
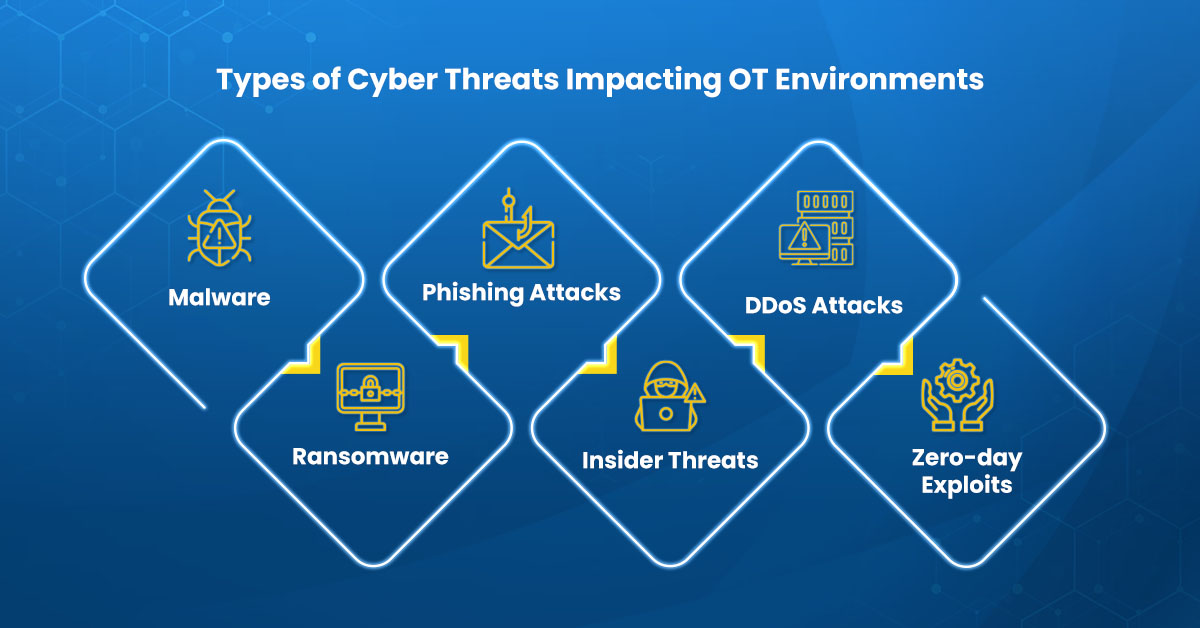
Operational technology (OT) environments are increasingly being targeted by cybercriminals due to their critical nature and potential for high-impact disruption. Here are some of the most common types of cyber threats facing OT environments:
Malware: Malware is a type of software designed to disrupt, damage, or gain unauthorized access to a computer system. Malware can enter an OT environment through email attachments, infected USB drives, or vulnerabilities in outdated software.
Ransomware: Ransomware is a type of malware that encrypts files or systems, effectively locking users out of their data until a ransom is paid. Ransomware attacks can cause significant disruptions to OT systems, leading to production downtime and lost revenue.
Phishing attacks: Phishing attacks are a type of social engineering attack that involves tricking users into giving up their login credentials or other sensitive information. Phishing attacks can be used to gain access to OT systems, compromise user accounts, or steal sensitive data.
Insider threats: Insider threats refer to threats posed by insiders, such as employees or contractors who have access to OT systems. Insider threats can be intentional or unintentional and can result from human error, negligence, or malicious intent.
Distributed Denial of Service (DDoS) attacks: DDoS attacks involve overwhelming a server or network with traffic, effectively rendering it unusable. DDoS attacks can be used to disrupt OT systems and cause significant downtime.
Zero-day exploits: Zero-day exploits refer to vulnerabilities in software or systems that are unknown to the vendor or security community. Zero-day exploits can be exploited by cybercriminals to gain unauthorized access to OT systems.
Understanding the types of cyber threats facing OT environments is critical to developing effective security strategies to protect against them. By implementing strong security controls, such as access control, network segmentation, and patch management, organizations can reduce their risk of cyber-attacks and protect their critical infrastructure.
Best practices for securing OT environments

Securing operational technology (OT) environments is critical to protecting critical infrastructure from cyber threats. Here are some best practices for securing OT environments:
Network segmentation: Segregate the OT network from other networks and implement network segmentation to limit the spread of malware and unauthorized access.
Access control: Implement strong access controls to limit access to OT systems and ensure that only authorized personnel can make changes.
System hardening: Apply security hardening measures to all OT devices to reduce their attack surface, including disabling unnecessary services, removing default accounts and passwords, and applying software updates.
Patch management: Keep all OT systems up to date with the latest software patches and security updates to reduce the risk of known vulnerabilities being exploited.
Monitoring and logging: Implement security monitoring and logging to detect and respond to security incidents in real time.
Regular vulnerability assessments: Conduct regular vulnerability assessments to identify vulnerabilities in OT systems and prioritize remediation efforts.
Incident response planning: Develop and test an incident response plan to quickly respond to security incidents and minimize their impact.
Training and awareness: Train all personnel who have access to OT systems on security best practices and provide ongoing awareness training to keep them informed about the latest threats and security trends.
By implementing these best practices, organizations can improve the security posture of their OT environments and reduce the risk of cyber-attacks. It’s essential to prioritize OT security and ensure that security measures are regularly reviewed, updated, and tested to keep pace with the evolving threat landscape.
Fortify the underlying technology infrastructure
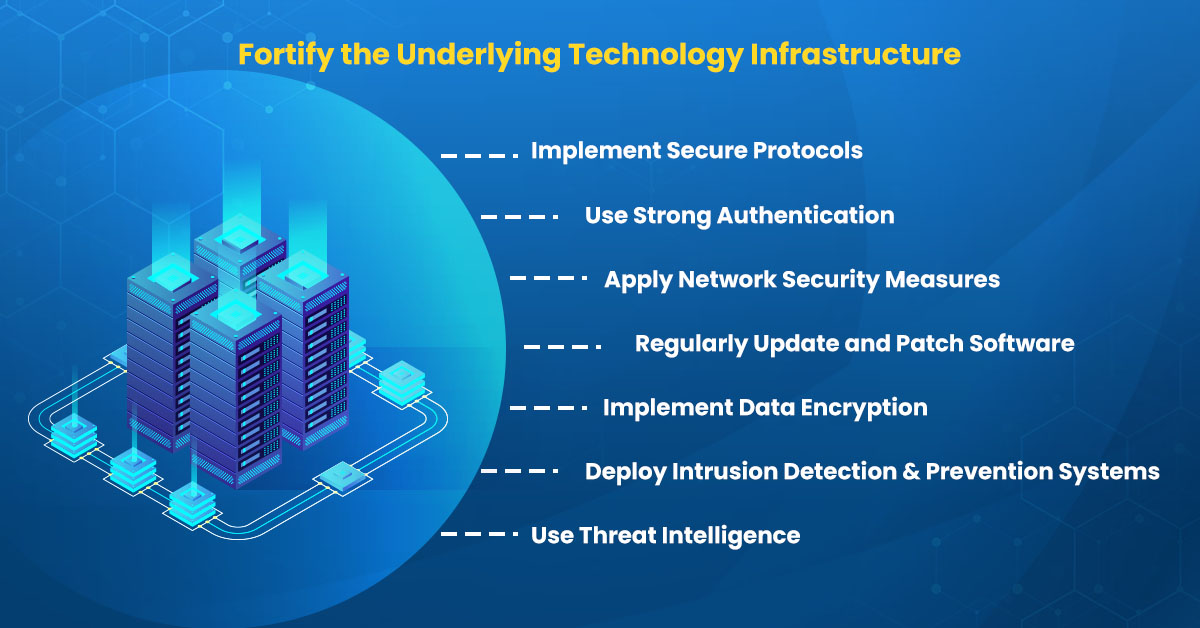
Fortifying the underlying technology infrastructure is a crucial step in securing operational technology (OT) environments. Here are some best practices for fortifying the underlying technology infrastructure:
Implement secure protocols: Ensure that all communication between devices and systems in the OT environment is encrypted using secure protocols such as SSL/TLS.
Use strong authentication: Implement strong authentication mechanisms such as multi-factor authentication (MFA) to prevent unauthorized access to OT systems.
Apply network security measures: Implement firewalls, intrusion detection, and prevention systems (IDPS), and other network security measures to monitor and control network traffic in the OT environment.
Regularly update and patch software: Keep all software up to date with the latest security patches and updates to reduce the risk of known vulnerabilities being exploited.
Implement data encryption: Encrypt all sensitive data at rest and in transit to prevent unauthorized access.
Deploy intrusion detection and prevention systems: Deploy IDPS systems that can detect and respond to malicious traffic and activity in real time.
Use threat intelligence: Use threat intelligence feeds to stay up to date on the latest threats and vulnerabilities and proactively identify potential risks.
By fortifying the underlying technology infrastructure of the OT environment, organizations can significantly improve their security posture and reduce the risk of cyber-attacks. It’s essential to continuously monitor and update the underlying technology infrastructure to keep pace with the evolving threat landscape.
Prioritizing value-driven approaches for operational technology (OT) operations

Prioritizing value-driven approaches can significantly benefit operational technology (OT) operations. By implementing a comprehensive asset management strategy, organizations can identify redundant or underutilized assets, reduce operational costs, and enhance efficiency. Predictive maintenance can help organizations avoid unplanned downtime and reduce maintenance costs by leveraging predictive analytics and machine learning algorithms. Real-time monitoring and analytics tools can help organizations identify operational inefficiencies, reduce energy consumption, and improve overall performance.
Integrating OT systems with business systems such as enterprise resource planning (ERP) and customer relationship management (CRM) platforms can improve supply chain management, streamline workflows, and enhance overall performance. Implementing a risk management strategy can help organizations identify, assess, and prioritize risks associated with OT operations, enabling them to develop and implement mitigation strategies to reduce the likelihood and impact of potential cyber-attacks and operational disruptions. Overall, prioritizing value-driven approaches for OT operations can help organizations optimize their operations, reduce costs, and enhance overall performance. It’s essential to develop a comprehensive strategy that aligns with the organization’s goals, leverages emerging technologies, and integrates with business systems to maximize value.
Importance of incident response planning:

Incident response planning is of utmost importance when it comes to securing Operational Technology (OT) environments. The criticality of OT systems such as power grids, water treatment plants, and transportation systems makes security incidents in OT environments a serious concern, as they can lead to potential harm to human life and safety. Moreover, the complexity of OT systems, consisting of various devices, sensors, and applications, makes it challenging to identify the source of security incidents and contain them without an incident response plan.
OT environments also face unique cyber threats like ransomware attacks, DDoS attacks, and supply chain attacks, which require a tailored incident response plan. Regulatory requirements in industries using OT environments, such as energy, transportation, and healthcare, make incident response planning a necessity for compliance. Having an incident response plan tailored to OT environments can help organizations respond quickly and effectively to security incidents, minimize damage and downtime, protect critical infrastructure, and comply with regulatory requirements.
Conclusion:
It is clear that cybersecurity is a crucial aspect of Operational Technology (OT) environments, and organizations must take proactive steps to secure their systems against potential cyber threats. By prioritizing value-driven approaches such as asset management, predictive maintenance, real-time monitoring and analytics, integration with business systems, and risk management, organizations can optimize their OT operations, reduce costs, and enhance overall performance. Additionally, incident response planning tailored to OT environments can help organizations respond quickly and effectively to security incidents, minimize damage and downtime, protect critical infrastructure, and comply with regulatory requirements. By implementing these strategies, organizations can ensure the safety and efficiency of their OT environments and stay ahead of emerging cyber threats.
