Top 5 PAM Trends You Can’t Ignore in 2025

Today, the ever-changing cyber-threat environment in which organizations operate is becoming more complex than ever. Sensitive data and critical systems are becoming popular targets, with privileged accounts often being the sources for many attackers to compromise these resources. Privileged Access Management (PAM) has become the bedrock of robust cybersecurity strategies meant to empower organizations to enable security control and monitoring of their most sensitive assets. As we enter 2024, several trends are reshaping the future of PAM, underscoring a need for organizations to stay ahead in bolstering their security measures.
What is privileged access management?
The term “privileged access management,” or PAM, describes the procedures, guidelines, and equipment used to regulate and monitor who has access to private information inside a company. Because privileged accounts frequently can access sensitive data or make system-level modifications, they can do serious harm if they fall into the wrong hands. PAM solutions allow businesses to control who has access, monitor how it is used, and respond in case of strange or risky activity.
How does PAM work?
PAM is the security process of locking up, managing, and auditing privileged accounts. The product uses different methods, such as least privilege access, session monitoring, and credential management, to enforce strict controls on access to sensitive resources. Solutions for PAM usually involve tools, such as password vaults, where the privileged credentials are stored safely, and session management systems, which track and record all privileged activity. Machine learning and behavioural analytics might be part of PAM, especially advanced access, that detects anomalies for added sophistication.
Why do businesses need PAM?
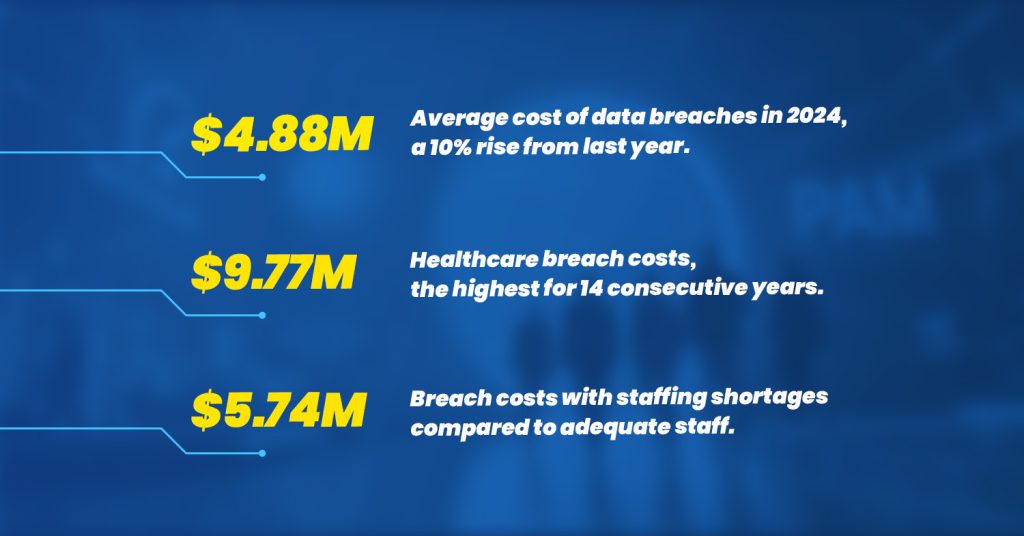
Privileged accounts are the most sought-after target for cybercriminals as they gain access to high-level systems and sensitive information. Organizations are in danger of facing unauthorized access, data breaches, and compliance if they do not use PAM. With strict controls on access and continuous monitoring, PAM can prevent attacks from the inside and the outside. Thus, PAM remains a fundamental requirement in any proper cybersecurity strategy. PAM protects data and systems and supports regulatory compliance, as many industry standards mandate strong privileged access controls.
Top 5 pam trends you can’t ignore in 2025
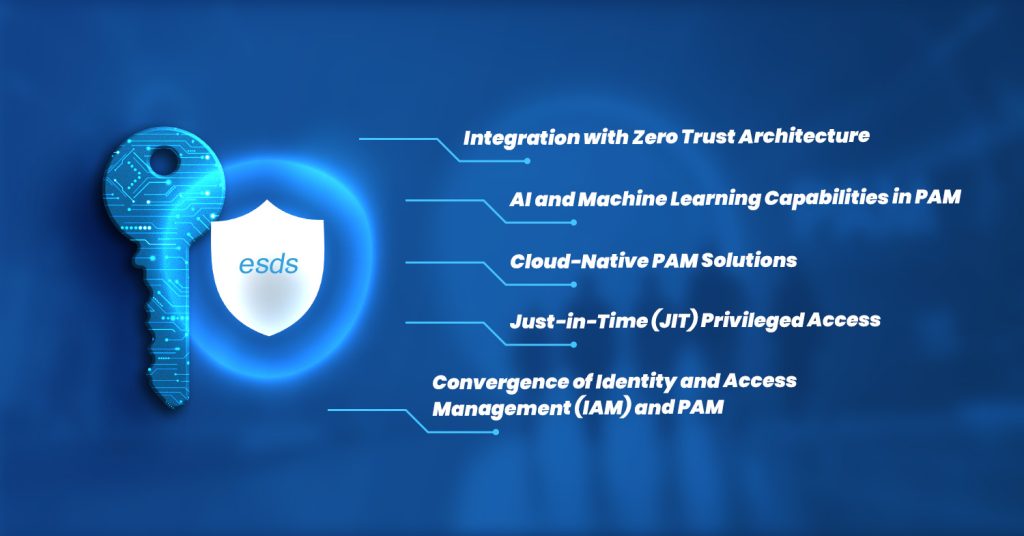
1. Integration with zero trust architecture
One of the most popular trends in cybersecurity is zero trust, which is currently included in PAM solutions. The foundation of Zero Trust is the principle that no system or user, internal or external, should be trusted by default. Because PAM enforces strict access controls over privileged accounts, it is a crucial enabler of the model that access requests are validated and authenticated before being granted.
By aligning with Zero Trust, PAM solutions can enforce the “least privilege” principle, granting access only when necessary. In 2024, more organizations are expected to adopt Zero Trust PAM solutions, providing granular control and visibility into who accesses sensitive resources and when. This trend will help businesses quickly detect and respond to potential threats while reducing the likelihood of access misuse.
2. AI and machine learning capabilities in PAM
Since compromised privileged credentials are involved in about 80% of security breaches, PAM is critical in defending sensitive data from cyberattacks. PAM is not an exception to how AI and ML are revolutionizing cybersecurity.
These technologies allow PAM solutions to identify potentially dangerous actions, evaluate user behavior patterns in real time, and alert users to potential security breaches. AI-powered PAM systems, for example, can identify “normal” user behavior and highlight discrepancies, allowing security teams to proactively take corrective action.
By 2024, abnormalities will be detected, responses automated, and AI and ML in PAM will be more advanced. This feature allows PAM systems to handle big datasets and adjust to new threats. It also uncovers hidden patterns that can point to security vulnerabilities. By predicting and preventing risks, AI-driven analytics help enterprises strengthen their defenses against cyberattacks.
3. Cloud-native PAM solutions
Cloud-native PAM solutions replace on-premises PAM systems as more companies go to the cloud. Because 10% of advanced cyberattacks target privileged credentials to obtain access to a company’s most sensitive data and systems, secure privileged accounts are crucial. Scalability, flexibility, and lower infrastructure costs are just a few of the benefits that make cloud-native PAM solutions the perfect option for contemporary, cloud-driven settings. The seamless integration of these solutions with cloud platforms guarantees uniform security in private, public, and hybrid cloud configurations.
The most significant advantage of cloud-native PAM systems is their ability to readily adapt to an organization’s changing needs without requiring major and costly infrastructure upgrades. Additionally, patches that keep security defenses current are constantly applied to cloud-native PAM solutions, relieving IT professionals of some of their responsibilities. In 2024, organizations may safeguard privileged access across all platforms with cloud-native PAM solutions, offering improved cost-effectiveness and simpler maintenance.
4. Just-in-time (JIT) privileged access
Just-in-Time (JIT) privileged access is the new face of modern PAM strategies. JIT access grants elevated permissions to users only when necessary and for a limited time, which significantly reduces the risk of unauthorized access. Time-bound access minimizes the potential for credential misuse and reduces the chances of prolonged access to critical systems by JIT PAM.
JIT PAM by ESDS ensures that temporary elevated permissions are removed when the task has been completed in cases where users require them to perform a specific task, such as an IT administrator doing some maintenance. The approach elevates security, traceability, and accountability; this process shows detailed logs indicating when and why access was granted. In 2024, more organizations are expected to adopt JIT access to bolster their security stance while streamlining the process of privileged access.
5. Convergence of identity and access management (IAM) and PAM
This is a critical trend in the convergence of IAM and PAM. The divergence in this area is because many users need a unified approach to handling their identities and access privileges. For an organization seeking to reduce complexity and improve security, combining IAM and PAM is as attractive as it gets. It allows an organization to manage its privileged and non-privileged accounts through one platform, giving the best overall view of all its user identities and access rights.
Unified IAM and PAM solutions streamline user provisioning, enforce access policies consistently, and provide centralized audit logs, all simplifying compliance management. In 2024, more organizations are expected to adopt these unified solutions, benefiting from improved visibility, reduced administrative burden, and enhanced security. By consolidating IAM and PAM, organizations can offer role-based access based on users’ roles and responsibilities, dynamically adjusting permissions without compromising security.
Wrapping up
Privileged Access Management is changing at breakneck speed. Zero Trust integration, AI-driven insights, cloud-native capabilities, just-in-time access, and IAM and PAM convergence lead the charge. These advancements point toward a shift toward more holistic, intelligent, and adaptive PAM solutions for sensitive data protection in a rapidly evolving cyber landscape.
Embracing all these trends enables organizations to increase their cybersecurity postures and secure privileged access through monitoring and compliance. In today’s world where cyber threats are growing in sophistication, embracing cutting-edge PAM strategies is the most crucial step towards staying resilient while safeguarding key resources. 2024 will shape the future into staying ahead of these trends.
- Achieving Secure, Reliable Compliance with India’s Data Sovereignty Mandates - November 17, 2025
- Implementing GPU workloads in critical government application - November 12, 2025
- Why Data Sovereignty Is Important for Indian Enterprises - August 22, 2025
