Vulnerability Assessment and Penetration Testing (vVAPT): Your complete guide
Finding security holes in software or a computer network involves using a technique called vulnerability assessment and penetration testing (VAPT Testing). VAPT needs to be more understood to refer to two different testing procedures. On the other hand, combining these two will result in superior outcomes. The Vulnerability Assessment’s objective is to find and fix bugs. Investigating and abusing the system is done during penetration testing to see if there are any vulnerabilities.

What is a Vulnerability Assessment?
Vulnerability assessment is a comprehensive process of identifying and evaluating well-known security vulnerabilities in a given environment. It is a high-level assessment of your information security posture that identifies weaknesses and offers mitigation strategies to either fix the defects or lower the associated risk level.
Why Vulnerability Management?
In the past ten years, malicious code, Trojans and sophisticated worms, botnets, DNS attacks, and spam websites have been the most often reported cyberattacks. Today, however, fraudsters are releasing new malware into the internet, including ransomware, pos assaults, and bitcoin wallet stealers, to name a few.
- Transformation of Information Security Needs
Data security regulations are changing at a breakneck pace as hackers look for new ways to get malware into the system. Businesses need help getting ready for information security incidents as a result.
- In this situation, conventional security measures are ineffective.
Long-term security measures (such as intrusion detection systems, antivirus software, encryption, preventive systems, patching, etc.) remain essential barriers against known dangers. However, the effectiveness of such solutions stays the same over time as intruders create new ways to get around such controls.
- Gaps in Incident Identification
Organizations cannot frequently detect data security vulnerabilities because of practically impossible-to-close detection gaps in their design.
How can you know if your firm requires a vulnerability assessment?
- Organizations frequently ignore vulnerability assessments and penetration testing, but every business is a potential target for hackers.
- Given recent ransomware attacks, this seems evident. Therefore, be accountable and ensure the proper security measures protect your application.
- A vulnerability assessment should be carried out once a year or soon after your application has undergone substantial changes.
The Primary Reasons for Vulnerabilities
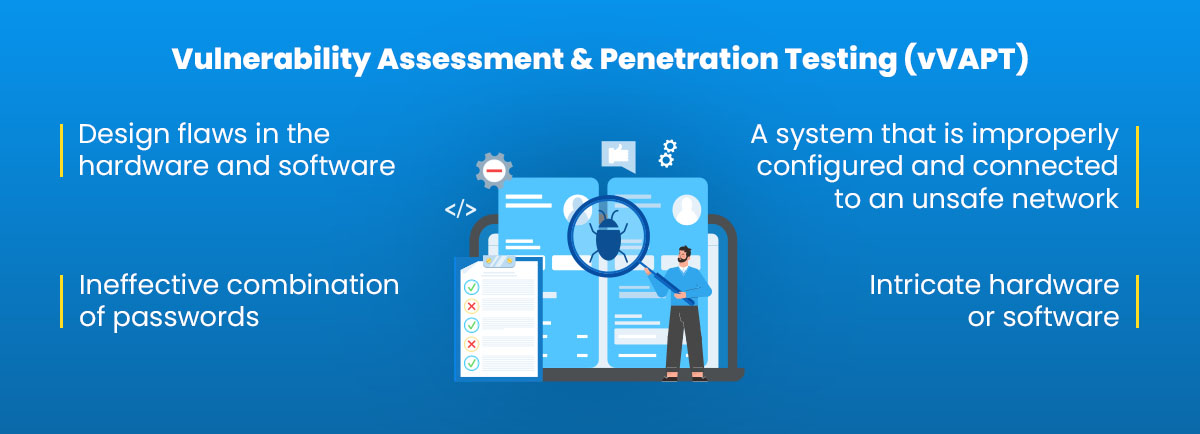
A system’s vulnerability stems primarily from incorrect configuration and poor programming techniques. Some of the causes of susceptibility are as follows.
- Design flaws in the hardware and software
- A system that is improperly configured and connected to an unsafe network
- Ineffective combination of passwords
- Intricate hardware or software
How do penetration tests work?
The goal of penetration testing, or PEN testing, is to identify security flaws in a network, system, or application that an attacker might exploit. These hackers are referred to as “white hat” hackers, and this practice is also known as ethical hacking. ‘White hat’ hackers will imitate the actual behavior of a cyber-criminal to pinpoint critical security holes and cracks; they will also provide solutions to these problems.
Additional Penetration Testing Types and Services
A pentest may go beyond a network to include social engineering assaults or physical security checks, depending on its extent. Also, there are two pentest types: “clear box” and “glass box,” which rely on the tester to investigate and are carried out with limited prior knowledge of the target systems.
Why Penetration Testing?

To safeguard financial data while transmission across networks or between systems.
To protect user data, find a program’s security flaws.
To identify systemic issues.
To determine how much tolerance, the organization has for cyber risks. To create a successful security strategy within the organization.
Penetration Testing: Discover hidden flaws before hackers do
Penetration testing assesses the entire application or system proactively to identify weak points or potential vulnerabilities, and it alerts security experts when preexisting security policies are broken. Security problems can only be fixed once the underlying reason is identified. To discover how an intruder will access data, penetration testing hacks into the system like a genuine hacker. This goes beyond simply finding security flaws. It identifies the vulnerabilities through which cybercriminals can enter the system and demonstrates the effectiveness of security safeguards or regulations.
Why is VAPT required?
Here are a few benefits VAPT can provide a business regarding security.
We thoroughly analyze the potential dangers to a company’s application.
Aid the company in identifying coding flaws that result in cyberattacks.
There is risk management at hand.
It protects the company’s finances and reputation.
Apps have internal and external attack protection. Prevents malicious attacks on the organization’s data.
How does VAPT defend against Data Breaches?
- Data breaches are a severe issue for all businesses and organizations, not just those who experience a hack. Identity theft, money theft, and diminished user trust can all come from data breaches. Data is the asset that any firm has the most exposure to risk.
- Businesses must make sure that their data is safeguarded and kept secure. Vulnerability assessments play a role in providing a certain amount of security against data theft. One of the best ways to guarantee the safety of your network and data from potential attacks by malevolent hackers is through vulnerability assessments.
- A critical phase in the vulnerability management process, vulnerability assessment is a technique for identifying known security flaws in a system or network.
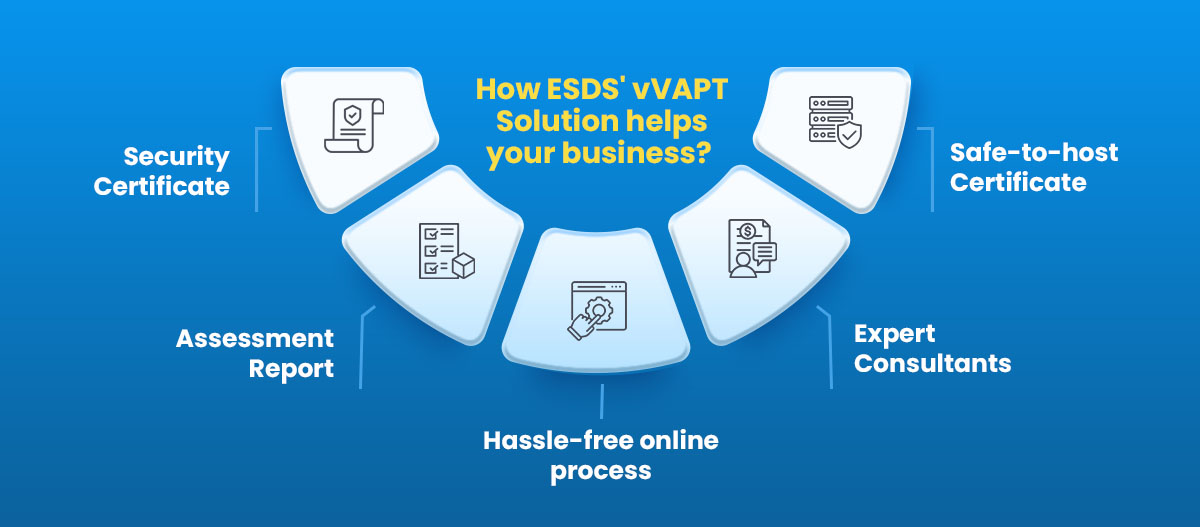
How ESDS’ vVAPT Solution helps your business?
Your infrastructure may have weaknesses in terms of cyber security, and Astra’s Vulnerability Assessment and Penetration Testing (VAPT) service may help you find them and devise a plan to remedy them.
A VAPT scan is a thorough examination that verifies the security of your online application. It is a professional-grade scan that includes a penetration test and a detailed vulnerability scan.
The complete application and its supporting infrastructure, including all network devices, management systems, and other elements, are analyzed by Astra’s VAPT scan. It is a thorough examination that aids in identifying security flaws so you may address them before a hacker can.
Security Certificate
With VAPT certification, you can demonstrate your commitment to security to customers and stakeholders after executing patch verification. In addition, maintain compliance with numerous regulatory bodies that require regular application testing, such as GDPR, ISO 27001, and PCI DSS.
Assessment Report
We will provide a detailed security evaluation report with recommended remedial steps. The information helps you proactively identify security vulnerabilities within your website and web applications to remediate any emerging problems.
Hassle-free online process
ESDS eliminates your hardships of physically getting in touch with the CERT-in-empanelled agency and going through the discussion process. It simply handles the entire process of VAPT virtually. With just a few clicks, you can be VAPT CERT-in certified.
Expert Consultants
Qualified CERT-In impaneled auditor Security Brigade executes the Vulnerability Assessment and Penetration Testing.
Safe-to-host Certificate
We offer a safe-to-host certificate to validate that your website is secure and its visitors safe from cyber-attacks.
Conclusion
Companies are scrambling to find new methods of data protection as the frequency of data breaches increases. There is a wealth of information on the internet on data protection measures that businesses can take. The fact is that in order to protect their data, companies of all sizes must use a top-notch VAPT solution. We’ve talked about the value of a VAPT solution and how it can shield your company from malicious attacks in our blog post. The nicest aspect is that all businesses can afford it.
- Why does your business need Endpoint Detection and Response (EDR)? - May 15, 2024
- Are your business endpoints completely secure? - March 26, 2024
- Is Colocation key to transforming your data center management strategy? - March 22, 2024