What is Endpoint Detection and Response (EDR)?
Endpoint Detection and Response (EDR) is a critical component of modern cybersecurity strategies. It is an advanced endpoint security solution designed to continuously monitor and protect end-user devices from cyber threats, such as ransomware and malware. EDR provides organizations with comprehensive visibility into their endpoints, allowing them to detect, investigate, and respond to security incidents effectively.
How Does EDR Work?
EDR (Endpoint Detection and Response) solutions work by continuously monitoring and recording the activities and events that occur on endpoints. This includes workloads, laptops, desktops, servers, and other devices. By analyzing this data in real-time, EDR solutions can detect suspicious behavior and potential threats. The key functions of EDR include:
1. Endpoint Visibility
EDR solutions provide real-time visibility into endpoints, allowing security teams to uncover adversary activities, even as they attempt to breach the environment. This visibility enables organizations to take immediate action to stop threats and prevent data breaches.
2. Threat Database
Effective EDR relies on a comprehensive threat database, which contains massive amounts of telemetry collected from endpoints. This database is enriched with context and can be mined for signs of attack using various analytic techniques.
3. Behavioral Protection
Unlike traditional antivirus solutions that rely on signature-based methods or indicators of compromise (IOCs), EDR employs behavioral approaches. It searches for indicators of attack (IOAs) to identify suspicious activities before a compromise occurs, providing proactive threat detection.
4. Insight and Intelligence
Integrating threat intelligence into EDR solutions provides contextual information about the attackers, including attribution and details about the attack. This helps organizations understand the motives and techniques used by adversaries, enhancing their ability to respond effectively.
5. Fast Response
EDR enables security teams to respond quickly and accurately to security incidents. By providing real-time information and actionable intelligence, organizations can stop attacks before they escalate into full-blown breaches, minimizing the impact on their business operations.
6. Cloud-based Solution
Cloud-based EDR solutions offer several advantages, including zero impact on endpoints and the ability to perform search, analysis, and investigation tasks accurately and in real time. This architecture ensures scalability, flexibility, and ease of management.
Key Benefits of EDR
Implementing an EDR solution offers several key benefits for organizations. Here are some of the best Endpoint Detection and Response benefits
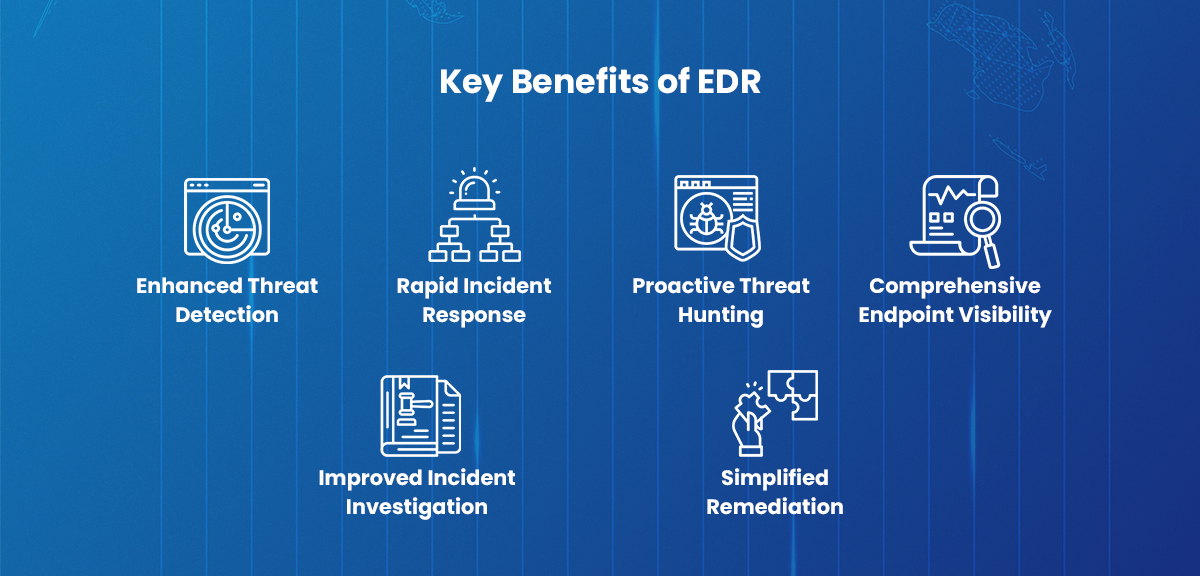
1. Enhanced Threat Detection
EDR solutions leverage advanced analytics and behavioral detection techniques to identify stealthy and sophisticated threats that may evade traditional security measures. This improves overall threat detection capabilities and reduces the risk of successful attacks.
2. Rapid Incident Response
With real-time visibility and actionable intelligence, EDR empowers security teams to respond swiftly and effectively to security incidents. This helps minimize the time between detection and response, reducing the potential impact of cyberattacks.
3. Proactive Threat Hunting
EDR solutions enable proactive threat hunting by leveraging advanced analytics and threat intelligence. Security teams can actively search for potential threats and indicators of compromise, allowing them to identify and neutralize threats before they cause significant damage.
4. Comprehensive Endpoint Visibility
EDR provides organizations with comprehensive visibility into endpoint activities, allowing them to monitor and track security-related events. This visibility helps organizations understand the behavior of adversaries, detect malicious activities, and gather valuable forensic evidence.
5. Improved Incident Investigation
EDR solutions store endpoint data in a centralized cloud-based platform, enabling security teams to rapidly investigate incidents. The ability to analyze historical and real-time data, combined with integrated intelligence, helps organizations gain a deeper understanding of security incidents and facilitates effective incident response.
6. Simplified Remediation
EDR solutions offer fast and decisive remediation capabilities. Security teams can isolate compromised endpoints from the network, preventing further damage and allowing for immediate remediation actions. This helps organizations mitigate the impact of security incidents and restore normal operations quickly.
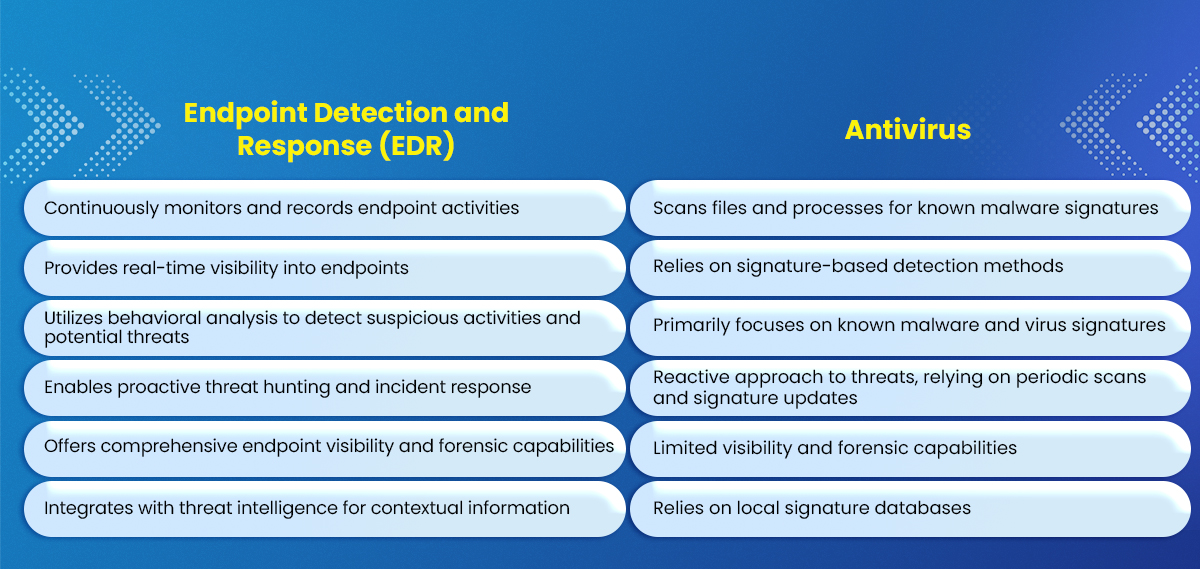
EDR vs Antivirus: Understanding the Difference
While traditional antivirus solutions focus on preventing known malware and viruses from infecting endpoints, EDR takes a more proactive approach. EDR solutions provide continuous monitoring, real-time visibility, and behavioral analysis to detect and respond to both known and unknown threats. Here are some key differences between EDR and antivirus:
Summing Up
EDR provides advanced threat detection, proactive threat hunting, real-time visibility, and comprehensive endpoint protection. While antivirus solutions are still important for preventing known threats, EDR goes beyond traditional antivirus capabilities to detect and respond to both known and unknown threats effectively.
EDR is a critical component of modern cybersecurity strategies, offering organizations enhanced protection, improved incident response capabilities, and comprehensive endpoint visibility. By implementing an EDR solution, organizations can strengthen their security posture and reduce the risk of successful cyberattacks.
- Top 5 Data Center Trends for 2024 - October 11, 2023
- Top 15 Cloud Computing Trends 2024 - October 4, 2023
- What is Infrastructure Monitoring and Why Infrastructure Monitoring Tool is Important for Your Business? - September 20, 2023
