What is Endpoint Security? Needs, Benefits, Challenges, and Best Practices

How you see data security is the reflection of how you treat your clients’ data. Goodwill, earning customers’ trust, and setting a benchmark is the must-have component in any and every business. Securing every device and its data is the whole responsibility of every organization.
The growing digital world as it grows has many advantages but does not lack several cons. Security concerns have become the primary point of discussion in the ever-increasing digital era.
What is an Endpoint?
Any hardware or virtual device that connects to the corporate environment is referred to as an endpoint. When networking, an endpoint will utilize either a TCP/IP (v4 or v6) address or another protocol (wired or wireless).
Endpoints can range from consumer electronics like desktop computers, laptops, tablets, and smartphones to servers, medical equipment, Internet of Things (IoT) gadgets, industrial control systems (ICS), point-of-sale (PoS) gadgets, ATMs, printers, network switches, routers, wearables, and much more.
Many different endpoints can use specific endpoint security solutions and management systems. Other options are platform or device-specific (Windows, mac OS, UNIX, Linux, Android, iOS, Azure, AWS, Google Cloud, etc.).
What is Endpoint Security?
Endpoint security is a technique used to protect endpoints on a network from online and offline threats, including user devices such as PCs, laptops, servers, smartphones, tablets, and the entire virtual environment. In simple terms, endpoint security refers to safeguarding company networks from dangers that may cause through local or remote devices. Any device that acts as an access point to an enterprise’s assets and applications can be considered an endpoint. These gadgets serve as attack vectors for fraudsters looking to exploit potential cybersecurity vulnerabilities.
Organizations are using cutting-edge tools with characteristics like machine learning (ML), artificial intelligence (AI), cloud, a virtual private network (VPN), encryption, and granular application control to deploy endpoint security to solve these issues. These modern tools protect businesses from the always-changing danger landscape. In addition, they protect enterprises from malware assaults, zero-day flaws, and other potential online dangers.
Why is Endpoint Security Essential for Every Organization?

For various reasons, an endpoint protection platform is an essential component of organizational cybersecurity. To begin with, in today’s corporate environment, data is a company’s most important asset – and losing that data, or access to that data, might put the entire organization at risk. Businesses have also had to deal with not just an increase in the number of endpoints, but also an increase in the variety of endpoints. On their own, these issues make company endpoint security more difficult, but they are exacerbated by remote work and BYOD rules, which render perimeter protection insufficient and create vulnerabilities.
Modern devices leverage the information-sharing capabilities of the cloud by connecting to servers remotely. With the rise in remote work, this practice is becoming incredibly popular. Compared to ten years ago, there are more networks with connected devices today.
These gadgets provide access points for hostile hackers that might steal assets from a business, view confidential data, or run malicious programs to take over your systems.
You may defend your assets from hackers by using endpoint security in the following ways:
- Endpoint security keeps an eye out for potential risks in an application’s behavior.
- Confidentiality is maintained while sensitive data shared between partners and vendors are secured.
- It blocks third-party programs from connecting to your devices and has several security measures to guarantee complete protection.
- Monitoring and alerting whenever the endpoint security tool detects an anomaly.
- It provides better flexibility and usefulness while safeguarding individual devices and corporate networks from threats.
Working of Endpoint Security

Any endpoint security solution’s primary purpose is to secure data and workflows connected with all devices that connect to the corporate network. It accomplishes this by inspecting files as they enter the network and comparing them to an ever-expanding database of threat information stored in the cloud.
The endpoint security solution offers system administrators a centralized management panel installed on a network or server that allows them to control the security of any devices that connect to it. Client software is then either remotely or directly deployed to each endpoint. When the endpoint is configured, the software delivers updates to it as needed, authenticates login attempts made from it, and administers corporate policies.
Endpoint security solutions also secure endpoints through application control. This prevents the user from downloading or using programs that the organization deems hazardous or unlawful. It also employs encryption to avoid data loss.
Businesses can use the endpoint security solution to detect malware and other typical security risks fast. Endpoint monitoring, detection, and response can also be provided, allowing businesses to detect increasingly advanced threats such as file-less malware, polymorphic attacks, and zero-day attacks. In the event of a security attack, this more advanced technique provides increased visibility and a broader range of reaction options.
Types of Endpoint Security
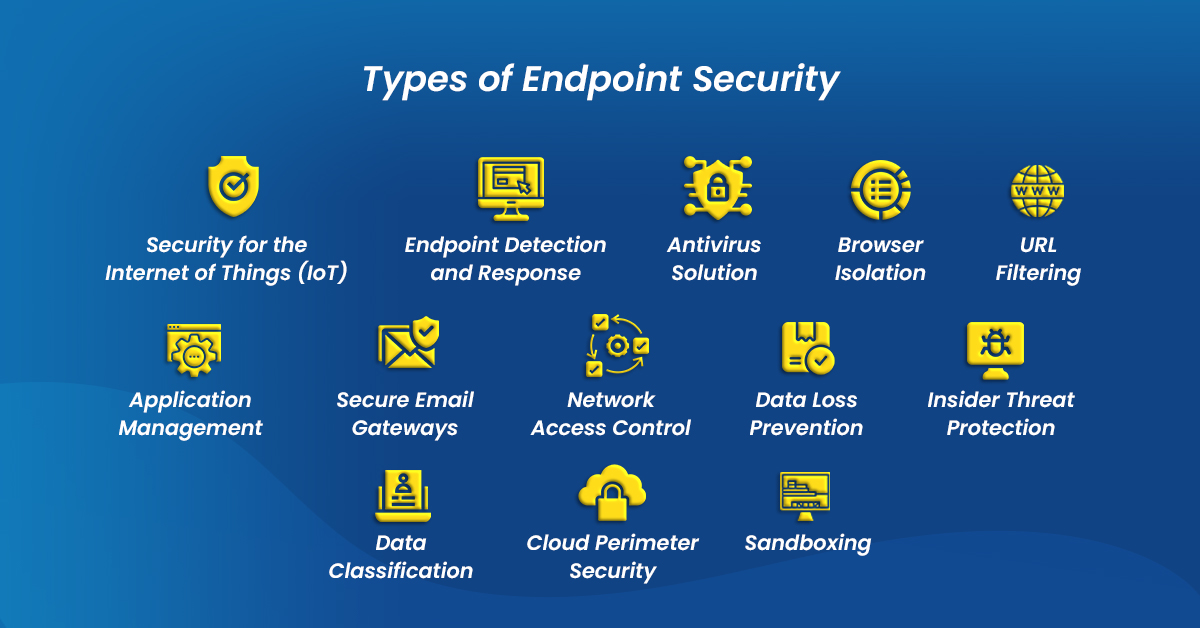
1. Security for the Internet of Things (IoT)
IoT devices are becoming more common in enterprise infrastructures as they aid communication and business processes. Unfortunately, endpoint security is typically built into IoT devices.
IoT security is one of the sorts of endpoint security offered for businesses to address this problem. These solutions help increase IoT device visibility, provide a consistent and straightforward layer of protection, and close network security holes.
2. Endpoint Detection and Response
EDR is one of the most popular endpoint security technologies since it provides a feature that works with the detection-mitigation model of modern cybersecurity. EDR solutions monitor every file and program that enters your company’s endpoints. EDR solutions can provide granular visibility, threat investigations, and ransomware and file-less malware detection. Additionally, EDR alerts your investigation teams so that prospective threats can be quickly identified and eliminated.
3. Antivirus Solution
Antivirus solutions continue to offer essential features and are arguably one of the most well-known and widely used types of endpoint security. These have antimalware features. As a result, businesses can defend against signature-based assaults, which occasionally happen. Additionally, by consulting with threat intelligence databases, antivirus software scans files for dangerous threats.
4. Browser Isolation
Surprise downloads; zero-day attacks, ransomware, crypto-jacking malware, and dangerous browser-executable code are just a few of the web browser attacks. Browser isolation uses segregated contexts where it cannot access valuable digital assets to carry out surfing sessions. Activity is still limited to safe, interactive media streams and isolated locations. After the user is done browsing, the application also eliminates web browser codes.
5. URL Filtering
URL filtering restricts online traffic to reliable websites. Additionally, URL filtering can stop shady downloads on your network, giving you more control over who and where downloads what.
6. Application Management
It should come as no surprise that application control manages permissions for apps, establishing strict limitations on what they can or cannot do. To achieve this, it employs whitelisting, blacklisting, and graylisting to stop malicious programs from launching and compromised applications from operating in a risky manner. This becomes crucial as businesses continue to use the cloud and the possibilities of external applications in their operations.
7. Secure Email Gateways
The primary method of data traffic entering and leaving your digital network is email. Thus, hackers use emails more than any other attack vector to disguise and spread their exploits. They may utilize email as their primary method of spreading malware up to 90% of the time, if not more.
Secure email gateways monitor suspicious activity in incoming and outgoing communications and block it from delivery. They can be set up to avoid phishing attempts by your IT infrastructure.
8. Network Access Control
NAC employs firewalls, which are placed between users, devices, and sensitive areas of your network.
9. Data Loss Prevention
A data loss prevention (DLP) strategy ensures that your most secure data resources are protected against exfiltration. One of the best ways to safeguard these assets is to keep employees informed about phishing tactics and install antimalware to prevent data loss from malicious programs hackers install on your endpoints.
10. Insider Threat Protection
Insider threats originate within your organization. Endpoints can be protected by controlling who has access to certain areas of your network, monitoring what they are doing, and ensuring all sessions are appropriately ended. Utilizing zero-trust network access (ZTNA) solutions is critical to governing who can access sensitive locations within your organization.
11. Data Classification
Companies use data classification to determine the endpoints that can be utilized to get unauthorized access to the most valuable and sensitive data. For example, a company may have multiple customer service employees who operate remotely and access critical financial information about its customers. In this case, data classification may aid in identifying a vital attack surface.
12. Cloud Perimeter Security
Cloud perimeter security in endpoints entails safeguarding your cloud resources against unauthorized devices and users. For example, a cloud firewall can restrict who and what devices can access your cloud resources. You can also utilize web filtering technologies that are hosted in the cloud.
13. Sandboxing
Sandboxing allows you to build an environment that mimics your regular end-user operating system while separating it from vulnerable network locations. Because you can sandbox individual applications, this can work with most types of endpoints.
Endpoint Security Implementation Challenges
- Lack of understanding about the endpoints in organizations
- Threat actors inside or outside the organization
- Security is difficult to standardize due to corporate endpoints’ number and diversity.
- One of the most significant security risks is the vulnerability of endpoints.
- Insider threats using authorized access to harm the security of an organization.
- Inadequate encryption standards
- Devices stolen or lost pose a security and compliance concern, particularly if they have access to sensitive data.
- The usage of personal devices
- Access to insecure remote resources
- Endpoints that are misconfigured
Best Practices for Endpoint Security
- Consistently applying endpoint protection policy
- Endpoint hardening
- Identify and onboard endpoints, or deny access to them
- Encrypt data stored on the devices
- Identify, prioritize, and remediate vulnerabilities
- Implementing threat detection, prevention, and mitigation
- Protecting devices from physical threats
- Secure endpoints of the vendors
Endpoint Security Benefits from ESDS

Endpoint security through a single security system
It can be challenging to install individual security systems. ESDS, in Endpoint security, offers one security system that connects to all computers, servers, and other devices. This shared trait enables security solutions to update, successfully dynamically preventing zero-day and multivector assaults.
It offers excellent protection for all the devices
A security tool for all devices, networks, and the information shared between them is endpoint security. You may continuously track and monitor applications across networks with the tool. Because of ESDS’ endpoint protection, businesses can now have more insight into what is happening on their networks.
Ensures a safe virtual environment
A local user interface created by endpoint security resembles the original network-based programs. The benefit of such a solution from ESDS is that it protects the enterprise’s servers and devices, ensuring that intruders cannot harm them.
Data loss prevention
Any organization can benefit from a database. However, the company’s vital data could be exposed if compromised. Endpoint security from ESDS offers an end-to-end data encryption capability that protects the business’s data from hackers. Thus, one of the key advantages of endpoint security is data loss prevention.
Improved user experience
Multiple security issues may discourage clients from using your company’s services. ESDS’ Endpoint security tracks user activity and application behavior, allowing users to pass the fewest possible security checks. Users can thus benefit from a flawless experience.
Lowers security expenses
ESDS’ Endpoint security controls all active devices in a network using a centralized security system. As a result, there is less need to recruit IT security personnel with expertise in handling or monitoring specific devices, as ESDS does it all for you.
Wrapping Up
Endpoint protection is required to prevent, mitigate, and repair external and internal threats. Solutions and strategies must scale to accommodate the increasing variety of devices, whether on-premise or remote, employee or vendor. Above all, you should construct your endpoint security technology stack with a solution provider like ESDS, that interacts and collaborates with the rest of your IT and security ecosystem.
- Decoding Generative AI: A Comprehensive Guide to Gartner’s Impact Radar - January 2, 2024
- 5 Best Practices for Cloud Security in 2024 - December 29, 2023
- 10 Best Machine Learning Ops Strategies for Cloud Environments in 2024 - December 29, 2023
