Why Do You Need Vulnerability Assessment and Penetration Testing?

VAPT is the process of identifying and exploiting all potential vulnerabilities in your infrastructure to reduce them. VAPT is performed by security specialists who specialize in offensive exploitation. Simply described, VAPT is a proactive “hacking” activity in which you exploit vulnerabilities in your infrastructure before hackers find them.
External security specialists do vulnerability assessment & penetration testing (VAPT), leveraging their experience to simulate hacker techniques, find significant security flaws, and cooperate with you to develop successful repair solutions.
Here are the below reasons for the need for the Vulnerability Assessment & Penetration Testing Tools:
- Leverage Comprehensive Evaluation
VAPT provides an integrated strategy by not only identifying holes in your systems but also simulating real-world assaults to assess feasibility, effect, and attack paths.
- Adopt a Security Approach
Regular VAPT reports can be an effective tool for enhancing SDLC security measures. Identifying vulnerabilities during testing and staging allows developers to remedy them before deployment.
- Empower Your Security Posture
Regularly scheduled VAPTs allow you to compare your security posture year after year. This will enable you to monitor progress, detect reoccurring flaws, and assess the efficacy of your security efforts.
- Stay Compliant with Security Standards
Many laws and compliance requirements require firms to conduct frequent security tests. Regular vulnerability scans verify that you satisfy these criteria, while pentest results allow compliance audits for SOC2, ISO 27001, CERT-IN, HIPAA, and other regulations.
Vulnerability Assessment & Penetration Testing Process Looks like
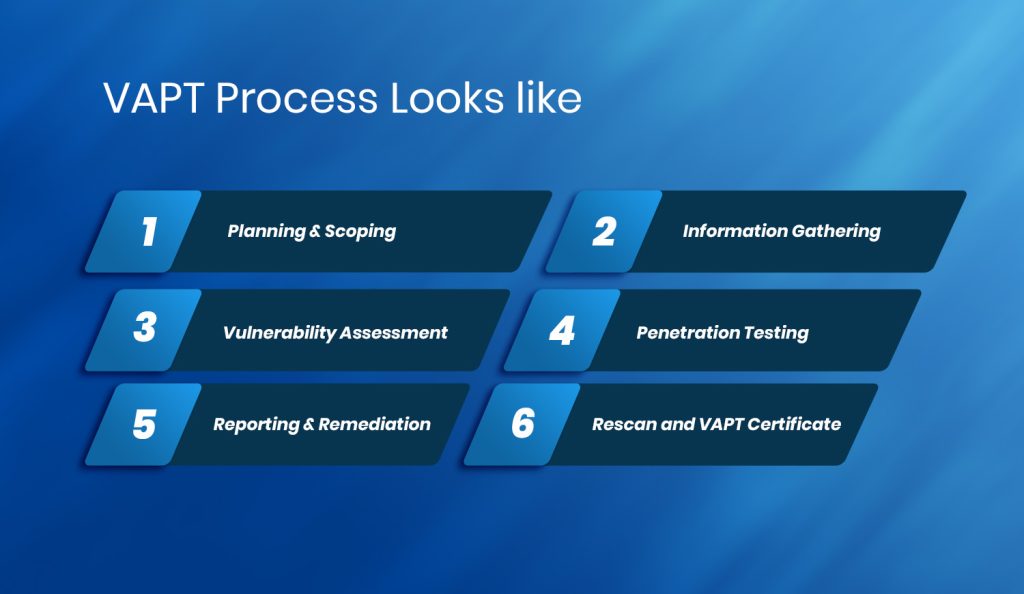
- Planning & Scoping
This phase specifies the VAPT’s aims and limitations. It entails selecting essential assets to be tested, deciding on testing methodology and compliance priorities, and developing communication channels with your VAPT testing provider.
- Information Gathering
During this VAPT testing step, the team collects data on the target systems, network architecture, and potential vulnerabilities from publicly available sources and allowed approaches. In the event of a gray box, they will collect information from you and begin mapping your target systems.
- Vulnerability Assessment
Providers use established scanners and automated techniques to scan your systems for known vulnerabilities during this step. This step detects possible software flaws, configuration settings, and security mechanisms.
- Penetration Testing
Security experts seek to exploit discovered flaws using hacking tactics. This stage replicates real-world assaults to determine the impact and efficacy of your security policies.
- Reporting & Remediation
Following exploitation, they provide a thorough VAPT report that details the vulnerabilities discovered, exploitation attempts conducted, and suggestions for remedy. This step also includes developing a strategy to resolve vulnerabilities and improve your overall security posture.
- Rescan & VAPT Certificate
After the vulnerabilities have been fixed, certain penetration testing businesses may offer rescans to confirm the above, create clean reports, and issue publicly verifiable VAPT certificates to aid compliance checks.
6 Significant Types of VAPT Tools
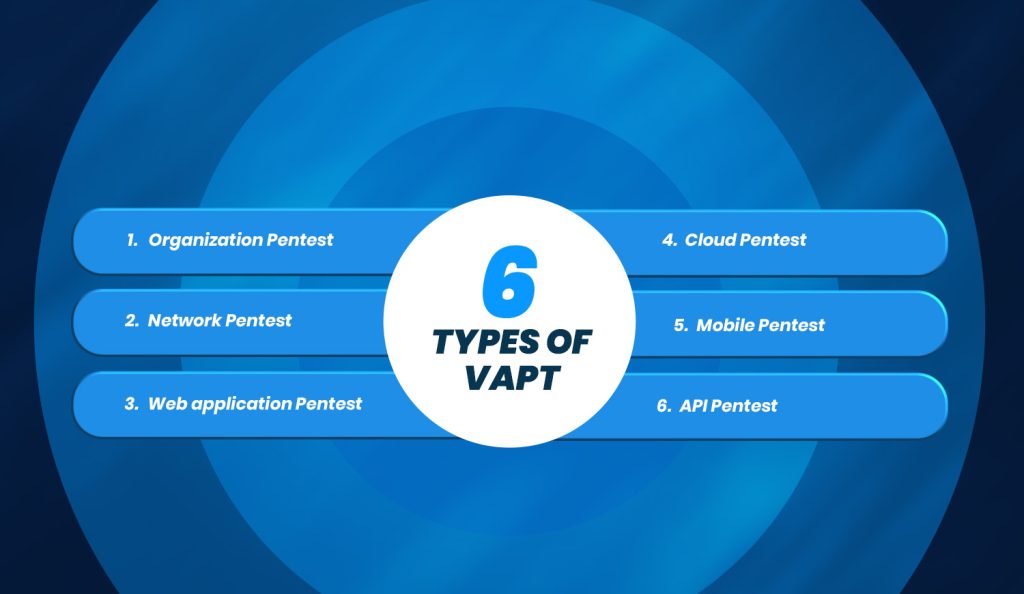
- Organization Penetration Testing
Organizational penetration testing is a comprehensive evaluation that mimics real-world assaults on an organization’s IT infrastructure, which includes the cloud, APIs, networks, online and mobile apps, and physical security.
Pen testers often use a multi-pronged strategy to uncover vulnerabilities and associated attack vectors, including vulnerability assessments, social engineering methods, and exploit kits.
- Network Penetration Testing
Network penetration testing uses ethical hacking techniques to thoroughly examine your network’s defenses for exploitable data storage and transmission flaws. Scanning, exploitation, fuzzing, and privilege escalation are all standard tactics.
Penetration testing professionals use a staged strategy to map the network architecture, identify systems and services, and then use different automated and manual ways to obtain illegal access, replicating real-world attacker behavior.
- Cloud Penetration Testing
Cloud pentests and VAPT audits are designed to identify vulnerabilities in your cloud setups, APIs, storage methods, and access controls.
It uses a combination of automated tools and manual testing to look for zero-day vulnerabilities and cloud-based CVEs utilizing a variety of methodologies. These frequently include SAST, DAST, API fuzzing, serverless function exploitation, IAM, and cloud setup methods.
- Web Application Penetration Testing
Web application penetration testing is a simulated type of cyber attack on a web application. It is a way to identify vulnerabilities and data theft.
- Mobile Penetration Testing
Mobile application penetration testing is a security assessment that finds and fixes vulnerabilities in mobile apps. It’s done by simulating real-world cyberattacks on the app.
- API Penetration Testing
Detect and remediate security vulnerabilities on a frequent basis. Ensuring compliance with business standards and authorities. Protecting sensitive information from unauthorized exposure and manipulation
How to Choose the Best VAPT Service Provider for You?
Here are the key points that need to be considered while choosing the best VAPT Service provider:
- Understand Your Requirements
Before looking at supplier possibilities, consider your organization’s particular needs. Consider the size and complexity of your IT infrastructure, industry laws, budget, timetable, and VAPT scope.
- Methodology Depth
Look for VAPT providers who use proven approaches, such as the OWASP Testing Guide (OTG) or PTES (Penetration Testing Execution Standard), to provide a thorough review.
Inquire about their testing methods and how they are tailored to your needs.
- Look Beyond Cost
While cost is an important consideration, search for VAPT providers who deliver value and ROI beyond the initial evaluation. Examine the complexity of reports, customizable metrics (if available), post-assessment help, remedial advice, and retesting choices.
What benefits does ESDS’s VAPT testing service offer your business?
Here are the key features provided by ESDS VAPT tools:
- VAPT Service
The online process eliminates the need for in-person interactions with CERT-In-empanelled agencies for added convenience.
- Expert Auditors
The Vulnerability Assessment and Penetration Testing (VAPT) security audits are conducted by qualified CERT-in impaneled auditors from the Security Brigade.
- Comprehensive Website Protection
VTMScan includes detailed CMS-specific scans for WordPress sites, addressing common vulnerabilities and ensuring robust security.
Final Thoughts
With the present state of cybercrime, the issue is no more whether to participate in a VAPT, but which VAPT is ideal for you.
A complete VAPT with continuous scanning not only strengthens your security posture but also fosters a security-first strategy, ensures compliance throughout the year, and strengthens consumer trust.
Finally, while the list of VAPT tools above is not complete, look for a supplier who goes above and beyond the fundamentals. Evaluate their scanning capabilities, techniques, VAPT experience in your specific business, and team knowledge.
- Why Do You Need Vulnerability Assessment and Penetration Testing? - March 13, 2025
- How to Choose the Right Private Cloud Service Provider in 2025? - February 27, 2025
- Why Cloud Migration is Essential: Benefits, Challenges, and Expert Tips - February 24, 2025
