Comprehensive Security Assessment
Identification of vulnerabilities across networks, applications, and systems through industry-recognized testing methodologies
Our Vulnerability Assessment and Penetration Testing services are structured to identify potential security exposures within your digital infrastructure, helping organizations assess risk and enhance system resilience.

Identification of vulnerabilities across networks, applications, and systems through industry-recognized testing methodologies

Continuous assessment to detect weaknesses in systems and applications that could impact security posture.

Alignment with the protocols and processes defined by the Indian Computer Emergency Response Team (CERT-In) for standardized and authorized testing procedures.

Web applications are vital for business but can present potential security challenges. While total risk elimination isn't possible, CERT-In facilitates organizations in strengthening their security frameworks through informed decisions based on vulnerability scanning reports
ESDS VAPT, as a service, assesses and ranks your organization's security technical strengths and loopholes with real-time insights into vulnerabilities.
VAPT is designed to secure websites and web applications, offering organizations the tools to safeguard their digital presence from evolving threats.

Our VAPT testing services include certification confirming alignment with compliance standards such as GDPR, ISO 27001, and PCI DSS, subject to post-patch verification.

A detailed evaluation report is shared, outlining identified vulnerabilities and suggested remediations for websites and web applications, supporting risk mitigation efforts

The testing is carried out by CERT-In empanelled auditors from Security Brigade, based on standardized procedures for evaluating technical security controls.

The VAPT process is facilitated online, enabling organizations to initiate assessments and receive reports digitally, with minimal procedural overhead.

A certificate indicating that the tested application meets the specified security parameters at the time of assessment is provided, subject to validation.

Optional periodic vulnerability scans using VTMScan are offered as an extended service, enabling multiple assessments over the course of a year.
Application security testing detects vulnerabilities, covers web and mobile apps, and reduces risks to meet compliance requirements.
This method uses internal and external assessments, along with device-level rules, to detect vulnerabilities and assess network risks.
Web application security testing for vulnerabilities like SQL injection, cross-site scripting, and logic flaws fight against cybercriminals.
IoT devices are vulnerable to hacking. IoT Security testing is crucial to ensure they function properly and are protected against cyber threats.
As mobile app usage grows, ESDS conducts thorough assessments using the latest frameworks and security and vulnerability scanning tools.
Cloud penetration testing evaluates a cloud system's strengths and flaws to enhance its security and identify risks, vulnerabilities, and gaps.
Wireless penetration testing identifies vulnerabilities, assess potential damage, and suggests remediation against unsecured wireless networks.




A single Vulnerability Assessment and Penetration Testing (VAPT) audit per year may not be sufficient to maintain strong website security. ESDS addresses this by offering additional annual VAPT services and leveraging our powerful tool, VTMScan, for continuous protection. VTMScan conducts comprehensive security audits four times a year, detecting a wide range of online threats, including OWASP Top-10 vulnerabilities, SQL Injections, and Cross-Site Scripting. It also performs CMS-specific scans for WordPress sites, identifying issues like user enumeration and plugin vulnerabilities. This proactive approach ensures your website remains secure year-round.
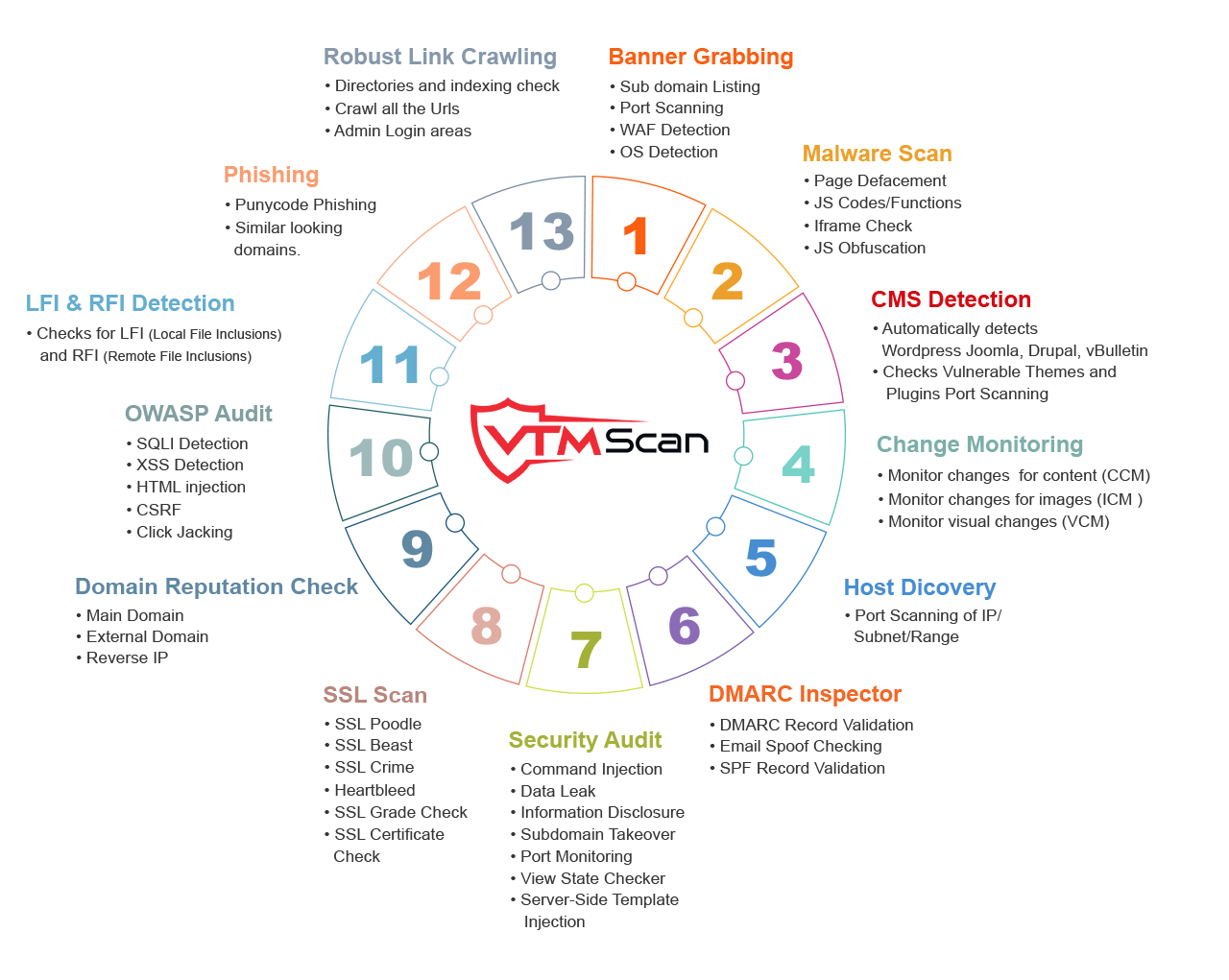
In addition to the standard Vulnerability Assessment and Penetration Testing (VAPT) audit, ESDS provides supplementary assessments throughout the year using VTMScan. These quarterly scans help identify potential threats on a recurring basis, allowing organizations to address vulnerabilities in a timely manner. This approach is designed to support ongoing security monitoring and strengthen web application risk management beyond a one-time audit.
The service is delivered through a fully digital process, minimizing the need for physical interaction during coordination with CERT-In empanelled agencies
All security audits under the Vulnerability Assessment and Penetration Testing (VAPT) framework are conducted by CERT-In empanelled professionals, following standard procedures.
In addition to manual and automated checks, the service includes CMS-specific scans using VTMScan, particularly for platforms like WordPress, to help identify common vulnerabilities.
Can’t find what you are looking for?
Regular VAPT audits are crucial to stay ahead of evolving hacker techniques. They identify security flaws and offer guidance on fixing them, helping ensure compliance with regulations like GDPR, ISO 27001, and PCI DSS.
Our team will guide you through any preparations needed, but typically, minimal preparation is required on your part. Our online tool makes the process smooth and Streamlined.
Plot No. B- 24 & 25, NICE Industrial Area, Satpur MIDC, Nashik 422 007. Maharashtra, INDIA